Message Transfer Agent: SMTP
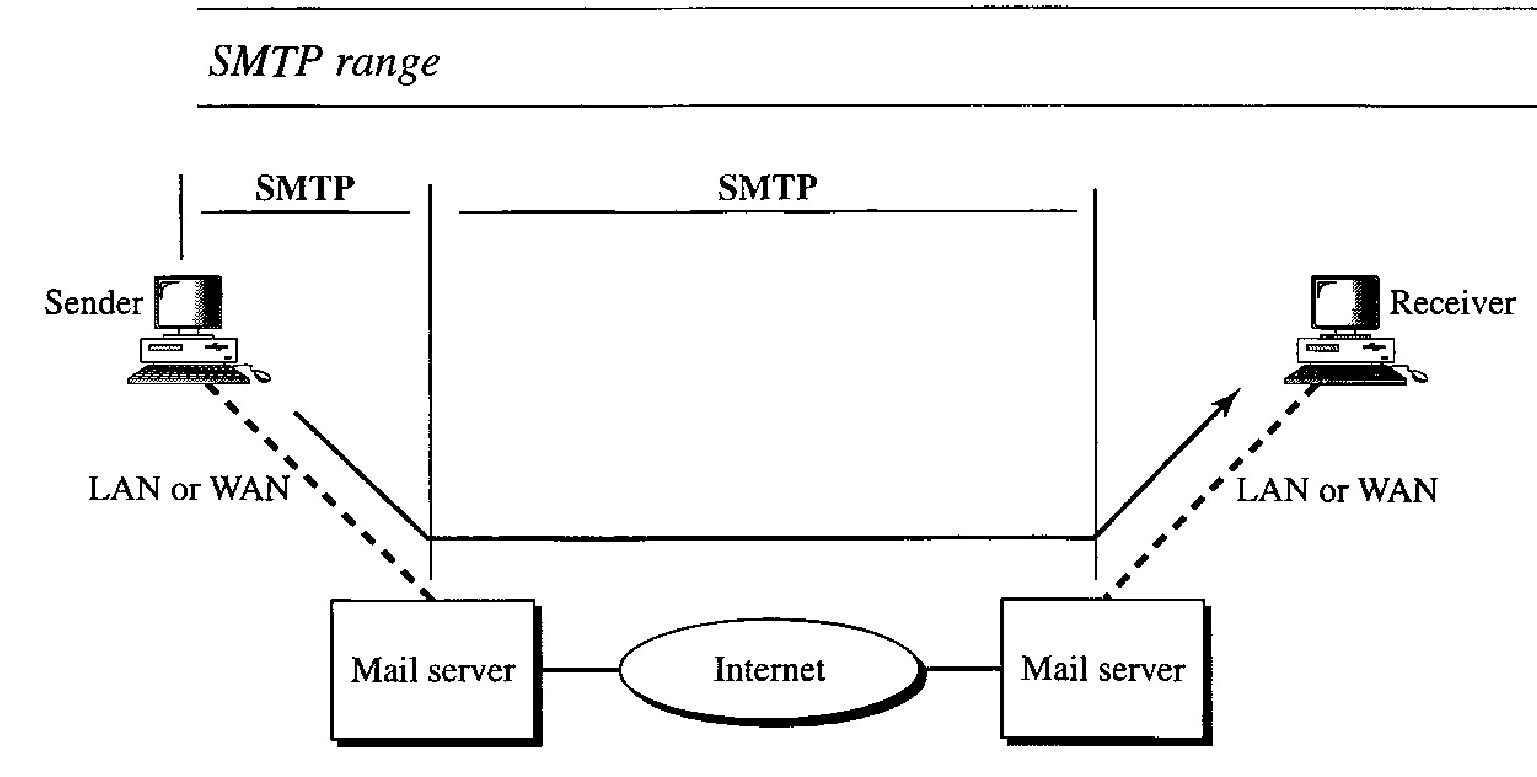
The actual mail transfer is done through message transfer agents. To send mail, a system must have the client MTA, and to receive mail, a system must have a server MTA. The formal protocol that defines the MTA client and server in the Internet is called the Simple Mail Transfer Protocol (SMTP).
SMTP is used two times, between the sender and the sender's mail server and between the two mail servers.
SMTP simply defines how commands and responses must be sent back and forth. Each network is free to choose a software package for implementation.
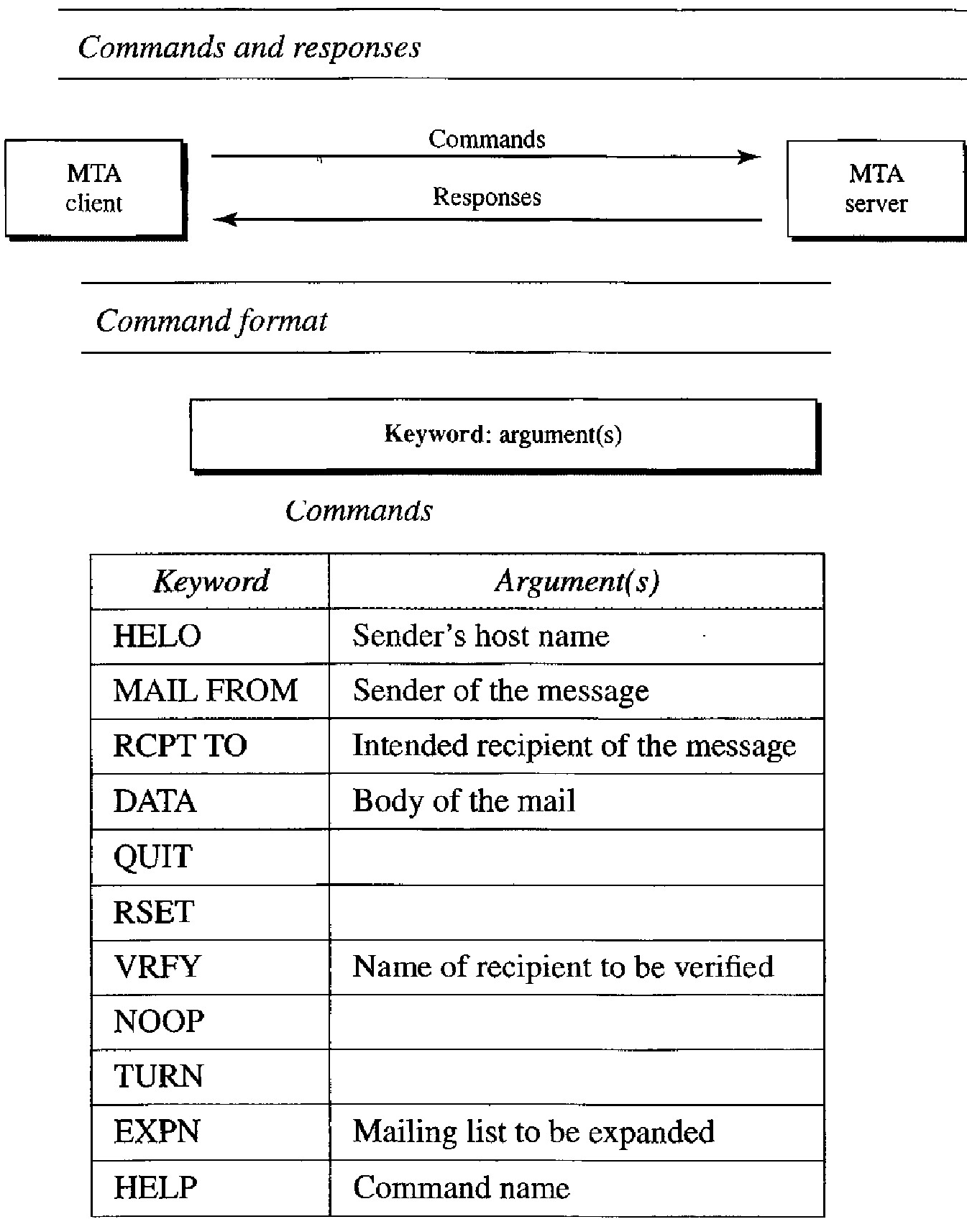
SMTP uses commands and responses to transfer messages between an MTA client and an MTA server
Each command or reply is terminated by a two-character (carriage return and line feed) end-of-line token.
Commands are sent from the client to the server. The format of a command is shown in Figure below. It consists of a keyword followed by zero or more arguments. SMTP defines 14 commands. The first five are mandatory; every implementation must support these five commands. The next three are often used and highly recommended. The last six are seldom used.
Responses are sent from the server to the client. A response is a threedigit code that may be followed by additional textual information. Table 26.8 lists some of the responses. Responses are divided into four categories. The leftmost digit of the code (2, 3, 4, and 5) defines the category.
The process of transferring a mail message occurs in three phases: connection estab- lishment, mail transfer, and connection termination.
Message Access Agent: POP and IMAP
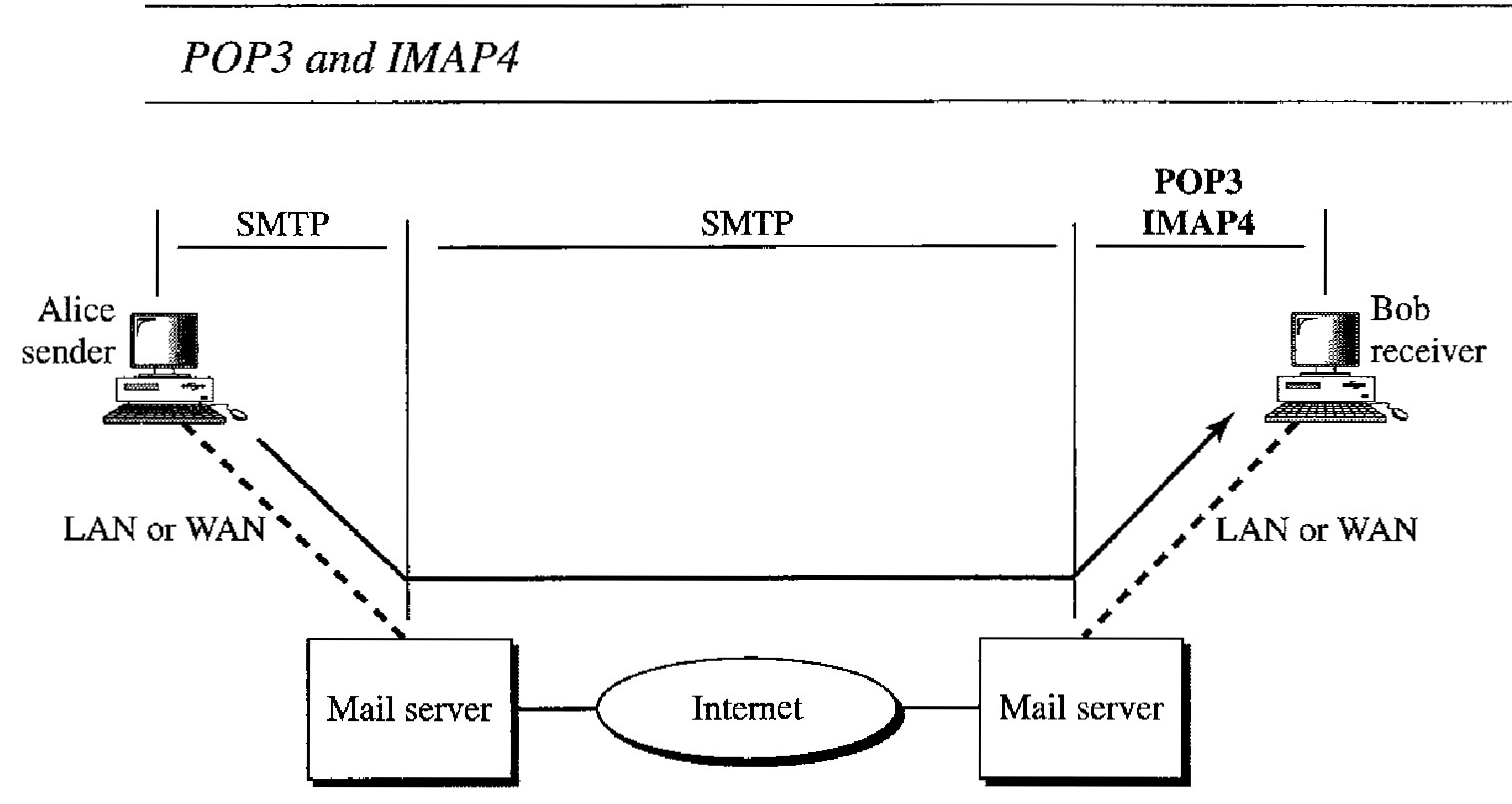
The first and the second stages of mail delivery use SMTP. However, SMTP is not involved in the third stage because SMTP is a push protocol; it pushes the message from the client to the server.
In other words, the direction of the bulk data (messages) is from the client to the server. On the other hand, the third stage needs a pull protocol; the client must pull messages from the server. The direction of the bulk data is from the server to the client. The third stage uses a message access agent.
Currently two message access protocols are available: Post Office Protocol, version 3 (POP3) and Internet Mail Access Protocol, version 4 (lMAP4). Figure below shows the position of these two protocols in the most common situation Post Office Protocol, version 3 (POP3) is simple and limited in functionality. The client POP3 software is installed on the recipient computer; the server POP3 software is installed on the mail server.
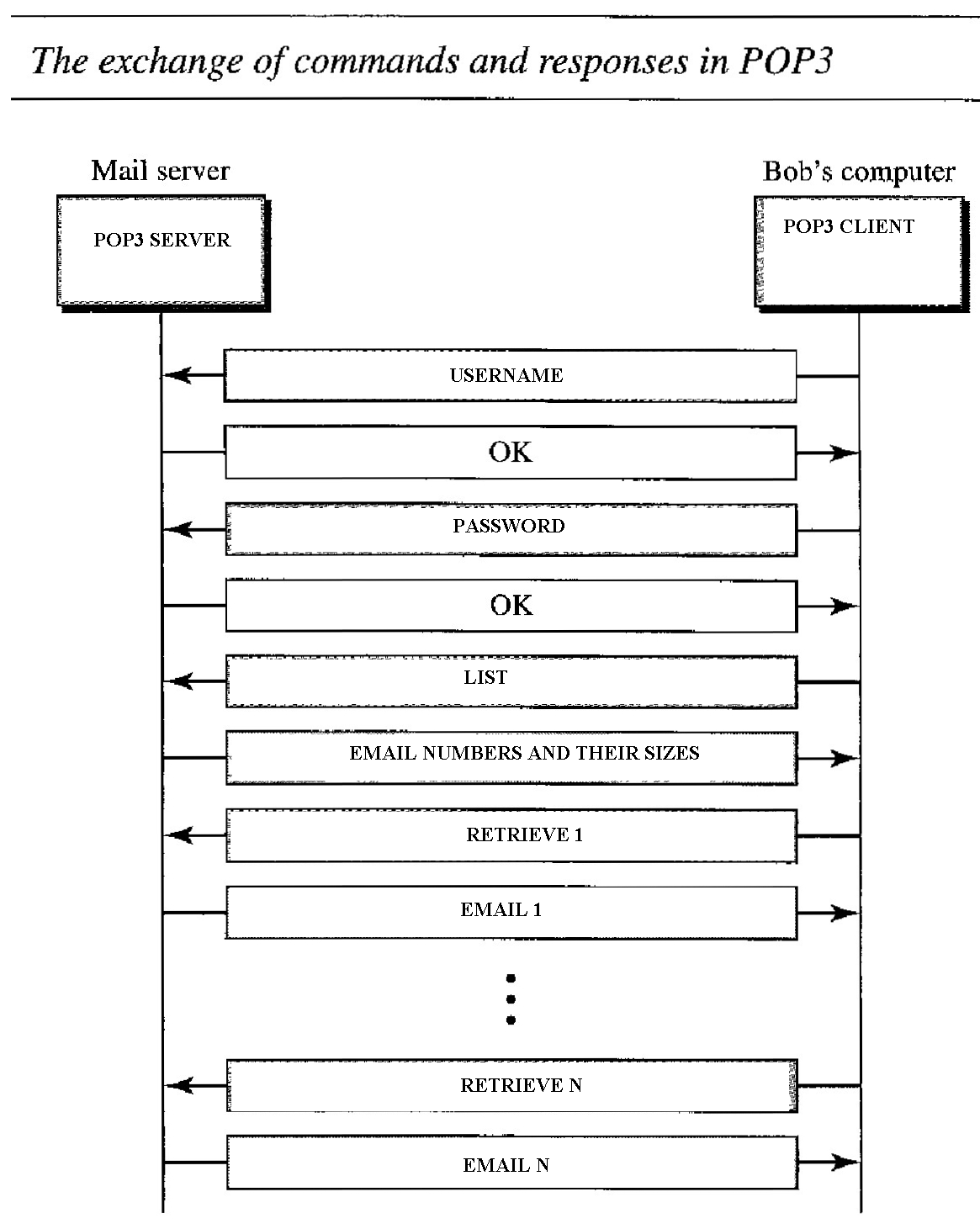
Mail access starts with the client when the user needs to download e-mail from the mailbox on the mail server. The client opens a connection to the server on TCP port 110. It then sends its user name and password to access the mailbox. The user can then list and retrieve the mail messages, one by one. Figure below shows an example of downloading using POP3.
POP3 has two modes: the delete mode and the keep mode. In the delete mode, the mail is deleted from the mailbox after each retrieval.
In the keep mode, the mail remains in the mailbox after retrieval. The delete mode is normally used when the user is working at her permanent computer and can save and organize the received mail after reading or replying.
The keep mode is normally used when the user accesses her mail away from her primary computer (e.g., a laptop). The mail is read but kept in the system for later retrieval and organizing.
Another mail access protocol is Internet Mail Access Protocol, version 4 (IMAP4). IMAP4 is similar to POP3, but it has more features; IMAP4 is more powerful and more complex.
POP3 is deficient in several ways. It does not allow the user to organize her mail on the server; the user cannot have different folders on the server. (Of course, the user can create folders on her own computer.)
In addition, POP3 does not allow the user to partially check the contents of the mail before downloading. IMAP4 provides the following extra functions:
o A user can check the e-mail header prior to downloading.
o A user can search the contents of the e-mail for a specific string of characters prior to downloading.
o A user can partially download e-mail. This is especially useful if bandwidth is limited and the e-mail contains multimedia with high bandwidth requirements.
o A user can create, delete, or rename mailboxes on the mail server.
o A user can create a hierarchy of mailboxes in a folder for e-mail storage.
FILE TRANSFER
Transferring files from one computer to another is one of the most common tasks expected from a networking or internetworking environment. One popular protocol involved in transferring files: File Transfer Protocol (FTP).
File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another.
Although transferring files from one system to another seems simple and straightforward, two systems may use different file name conventions.
Two systems may have different ways to represent text and data.
Two systems may have different directory structures. All these problems have been solved by FTP in a very simple and elegant approach.
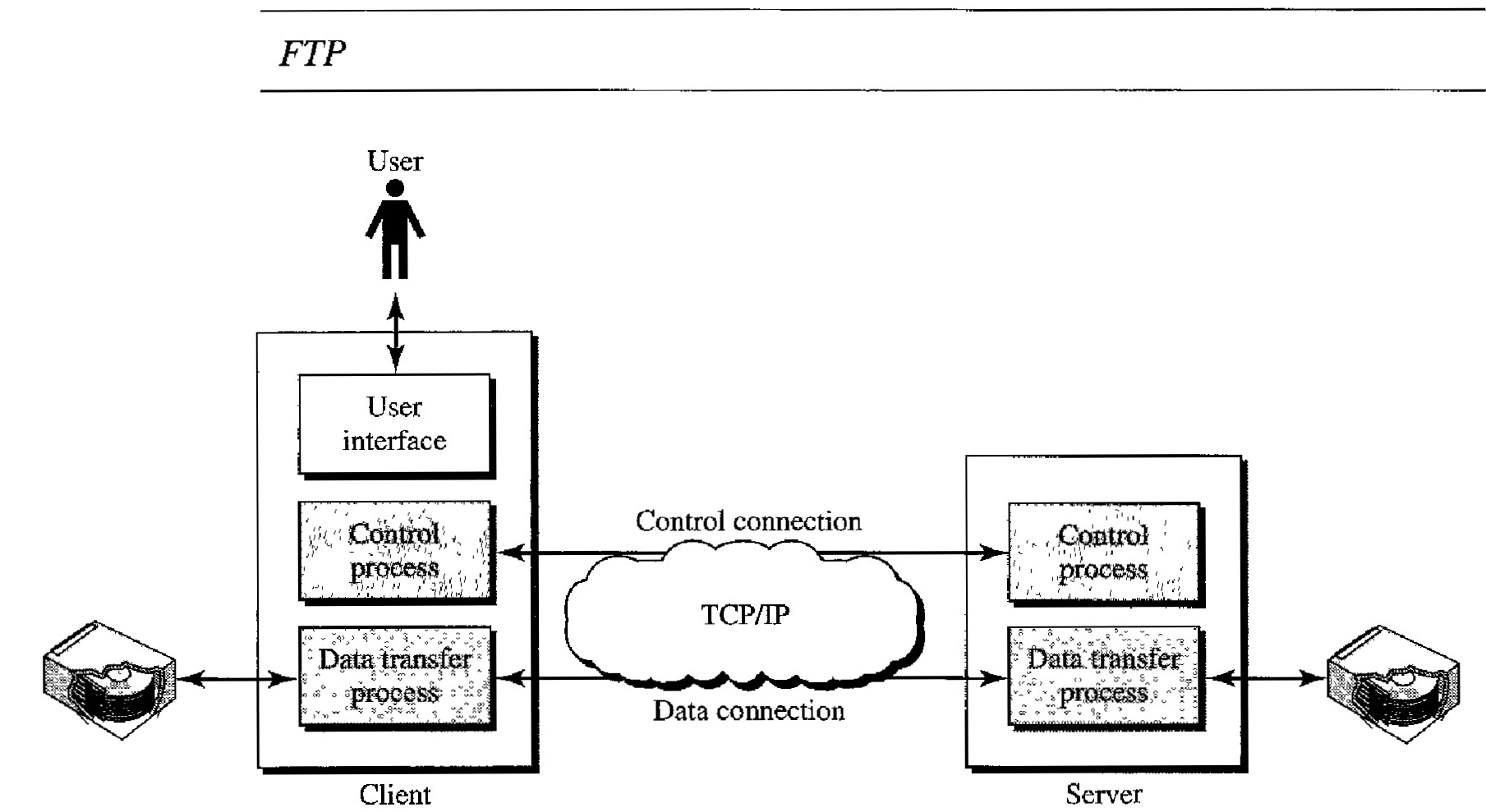
FTP differs from other client/server applications in that it establishes two connections between the hosts.
One connection is used for data transfer, the other for control information (commands and responses).
Separation of commands and data transfer makes FTP more efficient.
The control connection uses very simple rules of communication.
We need to transfer only a line of command or a line of response at a time. The data connection, on the other hand, needs more complex rules due to the variety of data types transferred.
However, the difference in complexity is at the FTP level, not TCP.
For TCP, both connections are treated the same. FTP uses two well-knownTCP ports: Port 21 is used for the control connection, and port 20 is used for the data connection.
The FTP client has three components: user interface, client control process, and the client data transfer process. The server has two components: the server control process and the server data transfer process. The control connection is made between the control processes. The data connection is made between the data transfer processes.
The control connection remains connected during the entire interactive FTP session. The data connection is opened and then closed for each file transferred. It opens each time commands that involve transferring files are used, and it closes when the file is transferred. In other words, when a user starts an FTP session, the control connection opens. While the control connection is open, the data connection can be opened and closed multiple times if several files are transferred.
Communication over Data Connection
We want to transfer files through the data connection. File transfer occurs over the data connection under the control of the commands sent over the control connection.
However, we should remember that file transfer in FTP means one of three things:
o A file is to be copied from the server to the client. This is called retrieving a file. It is done under the supervision of the RETR command.
o A file is to be copied from the client to the server. This is called storing a file. It is done under the supervision of the STOR command.
o A list of directory or file names is to be sent from the server to the client. This is done under the supervision of the LIST command. Note that FTP treats a list of directory or file names as a file. It is sent over the data connection.
The client must define the type of file to be transferred, the structure of the data, and the transmission mode.
Before sending the file through the data connection, we prepare for transmission through the control connection.
The heterogeneity problem is resolved by defining three attributes of communication: file type, data structure, and transmission mode
File Type : FTP can transfer one of the following file types across the data connection: an ASCII file, EBCDIC file, or image file.
The ASCII file is the default format for transferring text files. Each character is encoded using 7-bit ASCII.
The sender transforms the file from its own representation into ASCII characters, and the receiver transforms the ASCII characters to its own representation.
If one or both ends of the connection use EBCDIC encoding (the file format used by IBM), the file can be transferred using EBCDIC encoding.
The image file is the default format for transferring binary files. The file is sent as continuous streams of bits without any interpretation or encoding. This is mostly used to transfer binary files such as compiled programs.
Data Structure : FTP can transfer a file across the data connection by using one of the following interpretations about the structure of the data: file structure, record structure, and page structure.
In the file structure format, the file is a continuous stream of bytes. In the record structure, the file is divided into records. This can be used only with text files. Inthe page structure, the file is divided into pages, with each page having a page number and a page header. The pages can be stored and accessed randomly or sequentially.
Transmission Mode : FTP can transfer a file across the data connection by using one of the following three transmission modes: stream mode, block mode, and compressed mode. The stream mode is the default mode.
Data are delivered from FTP to TCP as a continuous stream of bytes. TCP is responsible for chopping data into segments of appropriate size.
If the data are simply a stream of bytes (file structure), no end-of-file is needed. End-of-file in this case is the closing of the data connection by the sender.
If the data are divided into records (record structure), each record will have a l-byte endof-record (EOR) character and the end of the file will have a l-byte end-of-file (EOF) character.
In block mode, data can be delivered from FTP to TCP in blocks. In this case, each block is preceded by a 3-byte header.
The first byte is called the block descriptor; the next 2 bytes define the size of the block in bytes.
In the compressed mode, if the file is big, the data can be compressed. The compression method normally used is run-length encoding.
In this method, consecutive appearances of a data unit are replaced by one occurrence and the number of repetitions. In a text file, this is usually spaces (blanks), In a binary file, null characters are usually compressed.
Anonymous FTP
To use FfP, a user needs an account (user name) and a password on the remote server. Some sites have a set of files available for public access, to enable anonymous FTP.
To access these files, a user does not need to have an account or password. Instead, the user can use anonymous as the user name and guest as the password.
User access to the system is very limited. Some sites allow anonymous users only a subset of commands.
For example, most sites allow the user to copy some files, but do not allow navigation through the directories.