UGC NET DEC 2017 PAPER 2
Ans .
A
- Explanation :
Every 24hrs, time will be 4 o'clock again. Now for 101 hours , 101 = 24*4 + 5 hours. So after 101 hours, time will be 4 o'clock + 5 hrs = 9 o'clock
Ans .
D
- Explanation :m = 3 x 42 + 1 x 41 + 3 x 40 = 48 + 4 + 3 = 55
n = 3 x 42 + 2 x 41 + 2 x 40 = 48 + 8 + 2 = 58
m + n = 55 + 58 = 113
a) 6 x 42 + 3 x 41 + 5 x 40 = 96 + 12 + 5 = 113
b) 3 x 44 + 2 x 43 + 3 x 42 + 1 x 41 + 2 x 40 = 768 + 128 + 48 + 4 + 2 = 950
c) 2 x 44 + 1 x 43 + 3 x 42 + 2 x 41 + 3 x 40 = 512 + 64 + 48 + 8 + 3 = 635
d) 1 x 43 + 3 x 42 + 0 x 41 + 1 x 40 = 64 + 48 + 0 + 1 = 113
Ans .
A
- Explanation :
Matrix A multiplies with Matrix B
Ans .
C
- Explanation :6C3 = 6! / 3! = (6 x 5 x 4 x 3!) / 3! = 6 x 5 x 4 = 120
Ans .
C
- Explanation :
GC AD GB GA AE DG BC BF ED CF AC DB 2 2 3 3 4 4 4 4 5 5 6 NIL
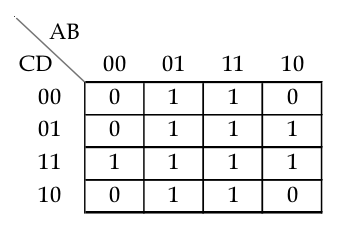
Ans .
A
- Explanation :
Ans .
B
- Explanation :
Make pair of 3 numbers from right i.e. 1 011 101 011 and convert each pair into octal as 1 = 1, 011 = 3, 101 = 5, 011 = 3
Ans .
A
- Explanation :
¬ (P ↔ Q) is equivalent to P ↔ ¬ Q
Ans .
B
- Explanation :
inverse of ∃ x H(x) is ∀ x ¬ H(x)
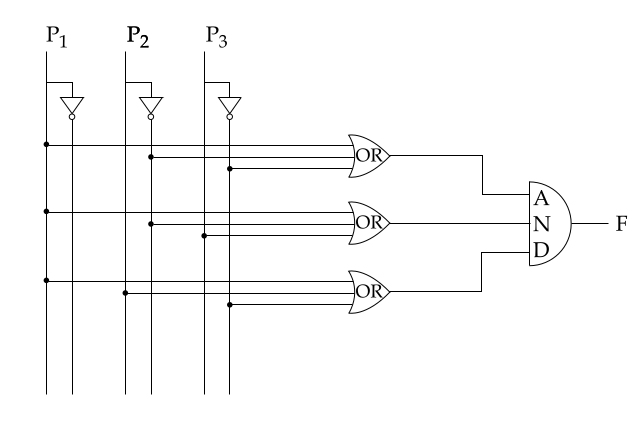
Ans .
B
- Explanation :
P1+P2'P3'
Ans .
A
- Explanation :
*(ptrdata++) is the correct way to represent pointer address in C++.
Ans .
C
- Explanation :
Array element access operates from left to right
Ans .
A
- Explanation :
A member function can always access the data in the class of which it is member
Ans .
B
- Explanation :
Virtual function is dynamic
Ans .
B
- Explanation :
Class templates differ from function templates in the way they are initiated is a False statement
Ans .
B
- Explanation :
A ‘view’ is a virtual table, which occurs after executing a pre-compiled query.
Ans .
C
- Explanation :
AVG-aggregates the queries
(a) Entity integrity (i) enforces some specific business rule that do not fall into entity or domain
(b) Domain integrity (ii) Rows can’t be deleted which are used by other records
(c) Referential integrity (iii) enforces valid entries for a column
(d) Userdefined integrity (iv) No duplicate rows in a table
Ans .
B
- Explanation :
None
Ans .
D
- Explanation :
Normal Forms- different classes of relations are created using technique to prevent modification anomalies.
Ans .
C
- Explanation :
MODIFY is used to change or modify the fields.
Ans .
C
- Explanation :
floor(i/2) array is representated.
Ans .
A
- Explanation :
Height = 3
Ans .
C
- Explanation :
No minimum spanning tree contains Emax.
Ans .
B
- Explanation :
Lexicographic or lexicographical order (also known as lexical order, dictionary order, alphabetical order or lexicographic(al) product) is a generalization of the way words are alphabetically ordered based on the alphabetical order of their component letters. This generalization consists primarily in defining a total order over the sequences (often called words in computer science) of elements of a finite totally ordered set, often called alphabet
Ans .
D
- Explanation :
Inorder:3, 4, 5, 7, 9, 14, 15, 16, 17, 18, 20
Ans .
C
- Explanation :
Switch takes data sent from one network device and forwards it to the destination node based on MAC address
Ans .
C
- Explanation :
Non - adaptive algorithms do not take their decisions on measurements or estimates of the current traffic and topology.
Ans .
A
- Explanation :
The number of bits used for addressing in Gigabit Ethernet is 32 bits.
Ans .
D
- Explanation :
Transport layer is also called end-to-end layer
Ans .
A
- Explanation :
The IP address 0.0.0.0, the lowest address, is used by hosts when they are being booted. It means ‘‘this network’’ or ‘‘this host.’’ IP addresses with 0 as the network number refer to the current network. These addresses allow machines to refer to their own network without knowing its number (but they have to know the network mask to know how many 0s to include). The address consisting of all 1s, or 255.255.255.255—the highest address—is used to mean all hosts on the indicated network. It allows broadcasting on the local network, typically a LAN.
Ans .
A
- Explanation :
ax=FFF5 h and cx=0 h with the above ALP following output is generated.
Ans .
D
- Explanation :
ax=00B7H; CF=1 with the above ALP following output is generated.
Where {+, *} are quantification characters.
Ans .
C
- Explanation :
0*1*0*1+ Doesn't include even values
Ans .
B
- Explanation :
Ambiguous grammar. In computer science, an ambiguous grammar is a context-free grammar for which there exists a string that can have more than one leftmost derivation or parse tree, while an unambiguous grammar is a context-free grammar for which every valid string has a unique leftmost derivation or parse tree.
Ans .
A
- Explanation :
None.
Ans .
B
- Explanation :
Scalability is the capability of a system, network, or process to handle a growing amount of work, or its potential to be enlarged to accommodate that growth
Ans .
C
- Explanation :
C-LOOK (Circular LOOK) One variant of LOOK is C-LOOK. It is an effort to remove the bias in LOOK for track clusters at the edges of the platter. C-LOOK basically only scans in one direction. Either you sweep from the inside out, or the outside in. When you reach the end, you just swing the head all the way back to the beginning. This actually takes advantage of the fact that many drives can move the read/write head at high speeds if it's moving across a large number of tracks (e.g. the seek time from the last track to track 0 is smaller than one would expect and usually considerably less than the time it would take to seek there one track at a time).The huge jump from one end request to the other is not considered as a head movement as the cylinders are treated as a circular list
Ans .
B
- Explanation :
None
Ans .
A
- Explanation :
Another component that is involved in the CPU-scheduling function is the dispatcher, which is the module that gives control of the CPU to the process selected by the short-term scheduler. It receives control in kernel mode as the result of an interrupt or system call.
Ans .
D
- Explanation :
Two atomic operations permissible on Semaphores are wait and signal
Ans .
B
- Explanation :
Defects are more likely to arise after software has been used often.
Ans .
C
- Explanation :
Re-organising and modifying existing software systems to make them more maintainable.
Ans .
D
- Explanation :
Having a separate testing phase after a build phase
Ans .
B
- Explanation :
Unit Testing,Integration Testing,Validation Testing,System Testing
Ans .
D
- Explanation :
Regression testing is a type of software testing that ensures that previously developed and tested software still performs the same way after it is changed or interfaced with other software. Changes may include software enhancements, patches, configuration changes, etc.
Ans .
A
- Explanation :
The Sunway TaihuLight is a Chinese supercomputer which, as of November 2017, is ranked number one in the TOP500 list as the fastest supercomputer in the world, with a LINPACK benchmark rating of 93 petaflops
Ans .
B
- Explanation :
ERP software packages are themselves combinations of seperate applications for manufacturing, materials, resource planning, general ledger, human resources, procurement and order entry. Hence True.
Ans .
D
- Explanation :
Agglomerative hierarchical clustering is a bottom-up clustering method where clusters have sub-clusters, which in turn have sub-clusters, etc. ... Then, in each successive iteration, it agglomerates (merges) the closest pair of clusters by satisfying some similarity criteria, until all of the data is in one cluster.
Ans .
B
- Explanation :
Bluetooth needs very less amount of battery power.
Ans .
C
- Explanation :
Amdahl’s law states that in parallelization, if P is the proportion of a system or program that can be made parallel, and 1-P is the proportion that remains serial, then the maximum speedup that can be achieved using N number of processors is 1/((1-P)+(P/N). If N tends to infinity then the maximum speedup tends to 1/(1-P) hence, 20.