UGC NET- Dec2015
Ans .
B
- Explanation :
For at least 3 women means there must be 3 or more than 3 women. Therefore we can choose 3 women from 12 women and 2 men from 20 men 4 women from 12 women and 1 men from 20 men 5 women from 12 women and 0 men from 20 men 12C3 x 20C2 + 12C4 x 20C1 + 12C5 x 20C0 = 220 x 190 + 495 x 20 + 79 = 52492
Ans .D
- Explanation :
G is bipartite if and only if all closed walks in G are of even length. Every minimal cycle in GG has length 4, that is every cycle of length strictly greater than 4 can be divided in cycles of length 4 For solution plz visit to see above theorem proof https://www.cs.sfu.ca/~ggbaker/zju/math/euler-ham.html http://www.sas.upenn.edu/~htowsner/math340/Lecture%207%20(Sep%2019).pdf
Ans .
D
- Explanation :
An infinite set is countable if and only if it is possible to list the elements of the set in a sequence (indexed by the positive integers). In mathematics, a countable set is a set with the same cardinality (number of elements) as some subset of the set of natural numbers. A countable set is either afinite set or a countably infinite set. Whether finite or infinite, the elements of a countable set can always be counted one at a time and, although the counting may never finish, every element of the set is associated with a natural number. Source https://en.wikipedia.org/wiki/Countable_set So The set of negative integers is countable is true(infinite countable) the integers that are multiples of 7 Answer: Countably infinite; listing: 0, 7, -7, 14, -14, 21, -21, 28, -28, ... ....is True The set of even integers is countable is true(infinite countable) the real numbers between 0 and 1 2 Answer: Uncountable (similar to diagonalization proof for real numbers between 0 and 1)
Ans .
C
- Explanation :
A simple graph G=(V,E) is called bipartite if its vertex set can be partitioned into two disjoint subsets V=V1⋃V2, such that every edge has the form e=(a,b) where aϵV1 and bϵV2. Bipartite graphs are equivalent to two-colorable graphs.
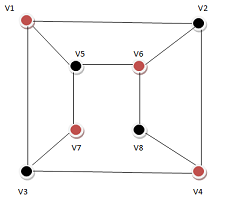 1. Assign Red color to the source vertex (putting into set V1).
2. Color all the neighbours with Black color (putting into set V2).
3. Color all neighbour’s neighbour with Red color (putting into set V1).
4. This way, assign color to all vertices such that it satisfies all the constraints of m way coloring problem where m = 2.
5. While assigning colors, if we find a neighbour which is colored with same color as current vertex, then the graph cannot be colored with 2 colors (ie., graph is not Bipartite).
So answer is option (C).
1. Assign Red color to the source vertex (putting into set V1).
2. Color all the neighbours with Black color (putting into set V2).
3. Color all neighbour’s neighbour with Red color (putting into set V1).
4. This way, assign color to all vertices such that it satisfies all the constraints of m way coloring problem where m = 2.
5. While assigning colors, if we find a neighbour which is colored with same color as current vertex, then the graph cannot be colored with 2 colors (ie., graph is not Bipartite).
So answer is option (C).
Ans .
D
- Explanation :
Caterpillar tree: In graph theory, a caterpillar is a tree in which all the vertices are within distance 1 of a central path. Theorem: All caterpillars are graceful. So, (a), (b) and (c) are graceful.
Ans .
A
- Explanation :
(a) P: Gora gets the job Q: Gora works hard R: Gora gets promotion S: Gora will be happy The argument can bet written as (P˄Q)→R R→S ¬S Therefore ¬P˅¬Q (b) Let P: Puneet is not guilty Q: Pankaj is telling the truth The argument can bet written as P˅Q ~Q Therefore, P Thus by disjunctive syllogism, the argument is valid. Disjunctive Syllogism: The disjunctive syllogism rule may be written as: P˅Q, ¬P ⊢Q It may also be written as: ((P˅Q)˄¬P)→Q where P, and Q are propositions expressed in some formal system.
Ans .
NONE OF THE ABOVE
- Explanation :
∀m ∀n P(m, n) says that every number divides every other number and result should be a postive integer. Clearly it is a false proposition. Eg: if m=10 n=3 10 divides 3 does not follow the proposition a is false ∀n P(1, n) says that any positive integer is divisible by 1 and result will be a +ve integer. That is correct b is true ∃m∀nP(m,n) says that there are some +ve integers which divides any other +ve integer. The proposition is correct example: 1 c is true Correct option must be a-- false b--true c--true None of the given options follows
Ans .
A
- Explanation :
Types of Proofs. Suppose we wish to prove an implication p ? q. Here are some strategies we have available to try. � Trivial Proof: If we know q is true then p ? q is true regardless of the truth value of p. � Vacuous Proof: If p is a conjunction of other hypotheses and we know one or more of these hypotheses is false, then p is false and so p ? q is vacuously true regardless of the truth value of q. � Direct Proof: Assume p, and then use the rules of inference, axioms, defi- nitions, and logical equivalences to prove q. � Indirect Proof or Proof by Contradiction: Assume p and �q and derive a contradiction r ? �r. � Proof by Contrapositive: (Special case of Proof by Contradiction.) Give a direct proof of �q ? �p. Assume �q and then use the rules of inference, axioms, definitions, and logical equivalences to prove �p.(Can be thought of as a proof by contradiction in which you assume p and �q and arrive at the contradiction p ? �p.) � Proof by Cases: If the hypothesis p can be separated into cases p1 ? p2 ? � � � ? pk, prove each of the propositions, p1 ? q, p2 ? q, . . . , pk ? q, separately. (You may use different methods of proof for different cases.)
Ans .
NONE OF THE ABOVE
- Explanation :
Ans .
D
- Explanation :
When a Group G must hold The commutative property then group is Abelian group.
Ans .
B
- Explanation :
term =1 , sum=0 suppose inp entered = 3 so First iteration term= 1*x/1 = x sum = 0 + x =x Second iteration term = x*x/2= x2/2 =x2/2! sum= x+x2/2! Third iteration term = =x2/2! *x/3 =x3/3.2.1=x3/3! sum= x+x2/2!+x3/3! and so on so sum= x+x2/2!+x3/3!+................
Ans .
A
- Explanation :
A publicly derived class is a subtype of its base class. Inheritance provides for code reuse. BOTH are correct
Ans .
C
- Explanation :
For Matching Any String in Oracle Like Operator is Used. also % symbol is used as a wild card character to represent multiple characters. so the answer is C.
Ans .
B
- Explanation :
Normalization: Reduces data redundancy in a database Data Dictionary: Contains metadata describing database structure Referential Integrity : Enforces match of primary key to foreign key External Schema: Define view(s) of the database for particular user(s).
Ans .
B
- Explanation :
Both time and space complexities are better in non-recursive than in recursive program
Ans .
B
- Explanation :
Base address+ offseet
Ans .
A
- Explanation :
This function is provided so that the terminate handler can be explicitly called by a program that needs to abnormally terminate, and works even if set_terminate has not been used to set a custom terminate handler
Ans .
D
- Explanation :
Entity type refers to some thing that may exist in real world with name and attributes
Ans .
A
- Explanation :
Indexes are used to simplify the access of database
Ans .
D
- Explanation :
ABD CLOSURE = { ABDE}={ABDEF}={ABCDEFG} SO CANDIDATE KEY IS ABD
Ans .
C
- Explanation :
IEEE 802.11 Services
Ans .
A
- Explanation :
Types of services are not related to fragmentation
Ans .
D
- Explanation :
Each frame carries 1 byte from each channel; the size of each frame, therefore, is 4 bytes, or 32 bits. Because each channel is sending 100 bytes/s and a frame carries 1 byte from each channel, the frame rate must be 100 frames per second. The bit rate is 100 × 32 = 3200 bps.
Ans .
A
- Explanation :
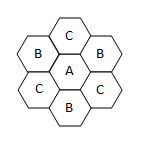 Each cell has six other adjacent cells, in a hexagonal grid. If the central cell uses frequency group A, its six adjacent cells can use B, C, B, C, B, and C respectively. In other words, only 3 unique cells are needed. So the answer is 840/3 = 280 frequencies.
Each cell has six other adjacent cells, in a hexagonal grid. If the central cell uses frequency group A, its six adjacent cells can use B, C, B, C, B, and C respectively. In other words, only 3 unique cells are needed. So the answer is 840/3 = 280 frequencies.
Ans .
NONE OF THE ABOVE
- Explanation :
p=3, q=13, d=7, e=3, M=5, C=? C = Me mod n n = p*q = 3*13 = 39 C = 53 mod 39 = 8 Answer is 8.
Ans .
C
- Explanation :
The pages which are not in main memory are:
1020 will not cause page fault (1024-2047) 3012 will not cause page fault (3072-4095) 6120 will not cause page fault (4096-5119) 8100 will not cause page fault (6144-7167)Page Address Address that will cause page fault 1 1K 1024-2047 3 3K 3072-4095 4 4K 4096-5119 6 6K 6144-7167
Ans .
C
- Explanation :
T = Ninstr x 1µs + 15,000 x 2,000 µs = 60s Ninstr x 1µs = 60,000,000 µs – 30,000,000 µs = 30,000,000 µs Ninstr = 30,000,000 The number of instruction between two page faults is Ninstr /NPageFaults = 30,000,000/15,000 = 2,000 If the mean interval between page faults is doubled, the number of instruction between two page faults is also doubled and is 4,000. Now the number of page faults is 30,000,000/4,000 = 7,500 T’ = 30,000,000 µs + 7,500 x 2,000 µs = 30,000,000 µs + 15,000,000 µs = 45,000,000 µs = 45s Doubling the memory, doesn’t mean that the program runs twice as fast as on the first system. Here, the performance increase is of 25%
Ans .
B
- Explanation :
Time in msec to read a block of 1024 bytes (Access time or Disk Latency) = seek time + average rotational delay + transfer time If there are 16384 bytes per track there are 1024/16384 tracks to be read for this block. Seek time = 40 msec Rotational delay = 16 msec Transfer time = (sectors_read/sectors per rev.) x rotational delay = (1024/16384) x 16 = 1 average rotational delay = rotational delay/2 = 16/2 = 8 access time = 40 + 8 + 1 = 49
Ans .
A
- Explanation :
Let us start with x=0 as smallest value is zero, so Available = 0 0 0 1 1 Need of each process = Maximum - Allocated so Need matrix becomes Need Matrix Process A 0 1 0 0 1 Process B 0 2 1 0 0 Process C 1 0 3 0 0 Process D 0 0 1 1 1 since available = 0 0 0 1 1 is not less than equal to any process need so x is not equal to 0 next smallest we take x = 1 so available = 0 0 1 1 1 since available <= process D need so we allocate now available becomes = allocated + available =1 1 1 1 0 + 0 0 1 1 1 =1 1 2 2 1 now need of process A <= available so process A completed and available becomes = allocated + available = 1 0 2 1 2 + 1 1 2 2 1 = 2 1 4 3 3 now need of process C <= available so process C completed and available becomes = allocated + available = 1 1 0 1 0 + 2 1 4 3 3 = 3 2 4 4 3 now need of process B <= available so process B completed and available becomes = allocated + available = 2 0 1 1 0 + 3 2 4 4 3 = 5 2 5 5 3 So system in safe state. Hence the correct option is (1) 1
Ans .
C
- Explanation :
The file /etc/gettydefs contains information used by getty(1m) to set up the speed and tty settings for a line. It supplies information on what the login-prompt should look like. It also supplies the speed to try next if the user indicates the current speed is not correct by typing a character.
Ans .
D
- Explanation :
(a) What is the maximum number of cells possible in the base cuboid? pn. This is the maximum number of distinct tuples that you can form with p distinct values per dimensions. (b) What is the minimum number of cells possible in the base cuboid? p. You need at least p tuples to contain p distinct values per dimension. In this case no tuple shares any value on any dimension. (c) What is the minimum number of cells possible in the data cube, C? (2n-1)p+1. The minimum number of cells is when each cuboid contains only p cells, except for the apex, which contains a single cell. (d) What is the maximum number of cells possible (including both base cells and aggregate cells) in the data cube, C? (p+1)n. The argument is similar to that of part (a), but now we have p+1 because in addition to the p distinct values of each dimension we can also choose ?.
Ans .
B
- Explanation :
P{M/S} = Probability that a person had meningitis , conditioned by the existence of existence of stiff neck P{S/M} = probability that a person complains about stiff neck, conditioned by the existence of meningitis. P{S} = proportion of people who complain about stiff neck. = 1/20P{M} = proportion of people who had meningitis. = 1/50,000Then:P{M|S} = (P{S|M}*P{M}) / P{S} =(1/2 x 1/50,000) / 1/20 = 0.0002 =( 2/10000)*100=2/100=0.02%
Ans .
B
- Explanation :
OLAP means online Analytical Processing. OLAP performs multidimensional analysis of business data and provides the capability for complex calculations, trend analysis, and sophisticated data modeling.
Ans .
A
- Explanation :
To design an effective and efficient data warehouse, we need to understand and analyze the business needs and construct a business analysis framework. Each person has different views regarding the design of a data warehouse. These views are as follows: The top-down view - This view allows the selection of relevant information needed for a data warehouse. The data source view - This view presents the information being captured, stored, and managed by the operational system. The data warehouse view - This view includes the fact tables and dimension tables. It represents the information stored inside the data warehouse. The business query view - It is the view of the data from the viewpoint of the end-user.
Ans .
C
- Explanation :
Double hashing uses the idea of applying a second hash function to the key when a collision occurs. The result of the second hash function will be the number of positions form the point of collision to insert. There are a couple of requirements for the second function: it must never evaluate to 0 must make sure that all cells can be probed
Ans .
C
- Explanation :
Check for the Cycles in the graph, you will find that node A,B,E form one cycle. node F,G form another cycle. Node C,D form another cycle. and H is having self loop.
Ans .
D
- Explanation :
As in the TREE-SEARCH procedure for binary search trees, the nodes encountered during the recursion form a path downward from the root of the tree. The number of disk pages accessed by B-TREE-SEARCH is therefore O(h) = O(logt n), where h is the height of the B-tree and n is the number of keys in the B-tree.
Ans .
D
- Explanation :
The In-order Traversal is Left--Root--Right. following this we have first root at 15, then left sub tree root at 13, then left subtree root at 4, then left is 2 and so on which results in 2 4 3 13 7 6 15 17 20 18 18
Ans .
C
- Explanation :
An ideal sort is an in-place-sort whose additional space requirement is O(1). that is, an in place sort manipulates the elements to be sorted within array or list space that contained the original unsorted input.
Ans .
A
- Explanation :
Various congestion policy at network layer are : Virtual circuit versus datagram Packet queueing and service policy Packet discard policy Routing algorithm Packet lifetime management
Ans .
A
- Explanation :
Loop unrolling is a compiler optimization applied to certain kinds of loops to reduce the frequency of branches and loop maintenance instructions. It is easily applied to sequential array processing loops where the number of iterations is known prior to execution of the loop. The general idea of loop unrolling is to replicate the code inside a loop body a number of times. The number of copies is called the loop unrolling factor. The number of iterations is divided by the loop unrolling factor. Loop unrolling is most effective when computations involving the loop control variable can be simulated by the compiler. For example, when a loop is stepping sequentially through an array, increments to a register that points to array entries can be simulated by the compiler with changes in the displacements in load and store instructions. Loop unrolling can reduce the number of loop maintenance instruction executions by the loop unrolling factor. In effect, the computations are done by the compiler rather than being done during program execution.
Ans .
C
- Explanation :
in assembly AX=AH+BL AL is the lower 8 bits AH is the higher bits 8 HERE AL and Ah both contains 15 or F so AX contains 0F0F or 0000 1111 0000 1111 XOR AL AL will return 0 in AL so AX becomes 0000 1111 0000 0000 MOV CL,3 will store 3 in CL shr ax,cl will shift right ax by 3 so 0000 1111 0000 0000 will become 0000 0001 1110 0000 or 01E0 in hexadecimal.
Ans .
B
- Explanation :
in option B. if (000)* executed twice then output is 000000 i.e. even number of zeros
Ans .
C
- Explanation :
System calls are usually invoked by using a software interrupt
Ans .
D
- Explanation :
The loader transfers the executable image of a C++ program from hard disk to main memory.
Ans .
C
- Explanation :
Error leads to fault and fault leads to failure
Ans .
D
- Explanation :
timeboxing allocates a fixed time period, called a time box, to each planned activity. Several project management approaches use timeboxing
Ans .
B
- Explanation :
We let y1=x-1, y2=y-2, y3=z-3, y4=u-0 We count the number of solutions for y1+y2+y3+y4=29-6=23 n=4, r=23 The number of solutions is C(n+r-1, r) = C(4+23-1, 23) = C(26,23) = C(26,3) = 26x25x24/1x2x3 = 2600
Ans .
C
- Explanation :
block = 2^10 block pointer size = 4B entries possible in block = 2^10 / 2^2 = 256 direct pointer gives = 10 * 256 = 10 blocks single indirect gives = 256 * 256 = 2^8 blocks double indirect gives = 256 * 256 * 256 = 2^16 blocks triple indirect gives = 256 * 256 * 256 * 256 = 2^14 blocks total = 16777546 blocks = 16777546 * 1024 = 17180207104 ~ 16 GB
Ans .
B
- Explanation :
E-Banking uses electronic means to transfer funds directly from one account to another rather than by cheque or cash.