UGC NET - June 2014
Ans .
C
- Explanation :
Infrared signals can be used for short range communication in a closed area using line of sight propagation.
Ans .
A
- Explanation :
A bridge has access to Physical address in the same network.
Ans .
D
- Explanation :
The minimum size of an Ethernet frame is 64 bytes. The breakup of this size between the fields is: Destination Address (6 bytes) + Source Address (6 bytes) + Frame Type (2 bytes) + Data (46 bytes) + CRC Checksum (4 bytes). The minimum number of bytes passed as data in a frame must be 46 bytes. If the size of the data to be passed is less than this, then padding bytes are added. The maximum size of an Ethernet frame is 1518 bytes. The breakup of this size between the fields is: Destination Address (6 bytes) + Source Address (6 bytes) + Frame Type (2 bytes) + Data (1500 bytes) + CRC Checksum (4 bytes). The maximum number of bytes of data that can be passed in a single frame is 1500 bytes.
Ans .
A
- Explanation :
Baud rate = 3000 / 6 = 500 baud/s
Ans .
D
- Explanation :
The minimum frame length for 10 Mbps Ethernet is 64 bytes and maximum is 1518 bytes.
Ans .
D
- Explanation :
Grammar G is called LL(1) if and only if whenever, If A->α|β are two distinct productions of G, the following conditions hold :- 1. (a) FIRST(α) , FIRST(β) must be disjoint. This is to be able to deterministically guess the production. (b) At most one of the strings α or β can derive ? (Since FIRST(α), FIRST(β) are disjoint. 2. If α-> ε then FIRST(β) and FOLLOW(A) must be disjoint
Ans .
D
- Explanation :
Removing left recursion and factoring the grammar do not suffice to convert an arbitrary CFG to LL(1) grammar.
Ans .
C
- Explanation :
A shift-reduce parser scans and parses the input text in one forward pass over the text, without backing up. A shift/reduce parser has two different actions it can take SHIFTING and REDUCING. Shift: the shift action is when the parser takes the first unanalysed word from the sentence, looks up its dictionary rule, and puts a token of category of the word onto the stack. Reduce: the reduce action is when the parser tries to match the topmost category tokens on the stack to the right hand side of the rule. If this succeeds, the tokens are removed and a token for the category on the left hand side of the rule is put on the stack instead. the shift-reduce parser faces four types of conflicts:
1. shift vs. shift;
2. shift vs. reduce left;
3. shift vs. reduce right;
4. reduce left vs. reduce right
Ans .
D
- Explanation :
S->S1|S3, S1->aS1c |S2|λ, S2->aS2b|λ, S3->aS3b|S4| λ, S4->bS4c|λ this grammer gives appropriate solution.
Ans .
C
- Explanation :
p->aq|br|λ, q->bs|ap r->as|bp, s->ar|bq,p is both initial and final state gives above solution.
Ans .
C
- Explanation :
p->aq|br|λ, q->bs|ap r->as|bp, s->ar|bq,p is both initial and final state gives above solution.
Ans .
A
- Explanation :
Key Process Areas : It identifies a cluster of related activities that, when performed collectively, achieve a set of goals considered important.
Ans .
D
- Explanation :
Risk management is the area that tries to ensure that the impact of risks on cost,multi source cost, quality, and schedule is minimal. Like configuration management which minimizes the impact of change, risk management minimizes the impact of risks. risk in incremental development is considered. Risk management can be considered as dealing with the possibility and actual occurrence of those events that are not ?regular? or commonly expected. Information Hiding is not a Risk Management Technique because Information hiding is the principle of segregation of the design decisions in a computer program that are most likely to change, thus protecting other parts of the program from extensive modification if the design decision is changed.Information hiding is a powerful programming technique because it reduces complexity.
Ans .
C
- Explanation :
The software architecture of a program or computing system is the structure or structures of the system, which comprise software elements, the externally visible properties of those elements, and the relationships among them. Architecture is concerned with the public side of interfaces; private details of elements?details having to do solely with internal implementation?are not architectural.
Ans .
C
- Explanation :
There are 14 Relative Complexity Adjustment Factors. They are 1. Requirement for reliable backup and recovery 2. Requirement for data communication 3. Extent of distributed processing 4. Performance requirements 5. Expected operational environment 6. Extent of online data entries 7 Extent of multi-screen or multi-operation online data input. 8. Extent of online updating of master files 9. Extent of complex inputs, outputs, online queries and files 10. Extent of complex data processing 11. Extent that currently developed code can be designed for reuse 12. Extent of conversion and installation included in the design 13. Extent of multiple installations in an organization and variety of customer organizations 14. Extent of change and focus on ease of use
Ans .
D
- Explanation :
Regression testing is primarily a maintenance activity. The purpose of regression testing is to validate the modified software and detect whether the unmodified code is added.
Ans .
D
- Explanation :
2^4 = 16
Ans .
D
- Explanation :
A function F is called self dual if it has equal number of minterms and maxterms, also mutually exclusive terms should not be included. the number of mutually exclusive terms is (pair wise) is 2n/2 = 2n-1. Number of functions possible by taking any of the one term from above mentioned mutually exclusive pair is = 2^2n-1
Ans .
C
- Explanation :
For an n-bit word (2's complement) which includes the sign bit, there are 2n-1 - 1 positive integers, 2n -1 negative integers and one 0 for a total of 2n unique states. so option iii is wrong hence answer C
Ans .
A
- Explanation :
If we put Ε!xp(x) denoting "there exists a unique x such that P(x) is true" we can get both options correct.
Ans .
D
- Explanation :
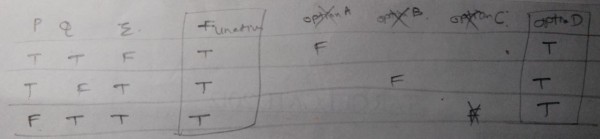
Ans .
A
- Explanation :
The upper bound and lower bound for the number of leaves in a B-Tree of degree K with height h is Kh and 2[K/2]h-1
Ans .
C
- Explanation :
m=n≥ 2 If G is connected simple graph with n vertices where n ≥ 3, then G has a Hamilton circuit if the degree of each vertex is at least n/2.
Ans .
B
- Explanation :
B is appropriate solution.
Ans .
A
- Explanation :
Since 48 cards of a 52-card deck are not aces, you are guaranteed to have at least two aces only if you have at least 50 cards.
Ans .
B
- Explanation :
B has perfect pairs.
Ans .
D
- Explanation :
The Object Request Broker (ORB) manages interaction between clients and servers. This includes the distributed computing responsibilities of location, referencing and 'marshaling' of parameters and results. The Object Request Broker or ORB takes care of all of the details involved in routing a request from client to object, and routing the response to its destination.
Ans .
B
- Explanation :
A computer program which is capable of acting on behalf of the user in order to accomplish a given computational task.
Ans .
C
- Explanation :
C has perfect pairs.
Ans .
A
- Explanation :
SET :Secure Electronic Transaction
Ans .
D
- Explanation :
Let total page =100. Effective Access Time = (30+100)* .7 +( 30+100+100)*(1- .7)=91+69=160
Ans .
D
- Explanation :
D has perfect pairs.
Ans .
B
- Explanation :
example of banker's algorithm.
Ans .
B
- Explanation :
B has perfect pairs.
Ans .
C
- Explanation :
option C will generate required output.
Ans .
B
- Explanation :
Elements in each half of the array are sorted amongst themselves.
Ans .
B
- Explanation :
Using Hoffman's algorithm, code for a is 1111; b is 0; c is 110; d is 1110; e is 10. Average code length is 4 x.12 + 1 x .4 + 3 x.15 + 4 x.08 + 2 x.25 = 2.15
Ans .
C
- Explanation :
Searching for an element in the hash table requires O(1) time for the average time, whereas for direct addressing it holds for the worst case time.
Ans .
B
- Explanation :
An algorithm is made up of 2 modules Ml and M2. If time complexity of M1 is h(n) and M2 is g(n) then the time complexity of the algorithm is max (h(n) ,g(n)).
Ans .
B
- Explanation :
3 is correct number.
Ans .
B
- Explanation :
B has perfect pairs.
Ans .
C
- Explanation :
we pass base address of the array when we pass array.
Ans .
D
- Explanation :
"computer" will get printed infinitely.
Ans .
C
- Explanation :
friend function allows one class to access other unrelated class.
Ans .
A
- Explanation :
successful completion of a program is indicated by 0.
Ans .
C
- Explanation :
example of External level data hiding.
Ans .
D
- Explanation :
A prime attribute cannot be transitively dependent on a key in a BCNF relation.
Ans .
A
- Explanation :
A clustering index is created when primary key is declared and ordered.
Ans .
B
- Explanation :
Find the closure set of all the options give. If any closure covers all the attributes of the relation R then that is the key. Algorithm to find Closure Set Step1: Equate an attribute or attributes to X for which closure needs to be identified. Step2: Take each FD (functional dependency) one by one and check whether the left side of FD is available in X, if yes then add the right side attributes to X if it is not available. Step3: Repeat step 2 as many times as possible to cover all FD's. Step4: After no more attributes can be added to X declare it as the closure set. FDs: C->F, E->A, EC->D, A->B Find closure set for CD. X = CD = CDF {C->F} No more attributes can be added to X. Hence closure set of CD = CDF Find closure set for EC. X = EC = ECF {C->F} = ECFA {E->A} = ECFAD {EC->D} = ECFADB {A->B} Closure set of EC covers all the attributes of the relation R..
Ans .
D
- Explanation :
D has perfect pairs.