UGC NET - Dec 2011
Ans .
D
- Explanation :
In Linear type data can be traversed sequentially. For example, arrays, linked list. In non linear type data is traversed in a non-sequential,hierarchal manner. Example are trees, Binary search trees etc. So option D will be the correct answer.
Ans .
D
- Explanation :
The total number of comparisons in a bubble sort is
=(N-1)+(N-2)+…+2+1
=(N-1)*N/2=O(N2)
Since this value is not available in the list of options,we go with D.
Ans .
B
- Explanation :
Obviously, Fibonacci Number Is a Bad Example, even mentioned in Lipstuitz book ... But still you want details Insight, you can look here
Good=Tower of hanoi
Bad=Fibonacci
Silly=Recursion
Ans .
D
- Explanation :
The domain is all values that x can take on. The only problem I have with this function is that I cannot have a negative inside the square root. So I'll set the insides greater-than-or-equal-to zero, and solve. The result will be my domain:
–2x + 3 ≥ 0
–2x ≥ –3
2x ≤ 3
x ≤ 3/2 = 1.5
Then the domain is "all x ≤ 3/2".
The range requires a graph. I need to be careful when graphing radicals
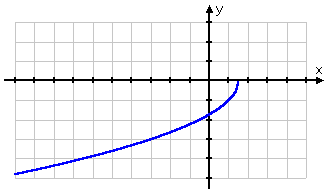
The graph starts at y = 0 and goes down (heading to the left) from there. While the graph goes down very slowly, I know that, eventually, I can go as low as I like (by picking an x that is sufficiently big). Also, from my experience with graphing, I know that the graph will never start coming back up. Then:
the range is "all y ≤ 0".
For Details you can refer to this link
Ans .
D
- Explanation :
Theorem.
In an undirected simple graph with N vertices without loops, there are at most N(N-1)/2 edges.
This can be proved by induction.
This can also be verified by drawing some simple graphs of 2,3, 4 and 5 vertices. But No multiple edges. So the answer is option D.
Ans .
B
- Explanation :
On .75th insertion probability of collision = 1/75
On 1.5th insertion probability of collision = 2/75
On 2.25th insertion probability of collision = 3/75
On 3th insertion probability of collision = 4/75
On 3.75th insertion probability of collision = 5/75
So the required probability is 1+2+3+4+5/75 = .20
Ans .
B
- Explanation :
Blind carbon copy (abbreviated Bcc:) allows the sender of a message to conceal the person entered in the Bcc: field from the other recipients. This concept originally applied to paper correspondence and now also applies to email.
Ans .
A
- Explanation :
In network topology, a star network is one where each host is connected to a central hub via a point-to—point link. It is considered a s the easiest topology to design and implement. It is also very easy to add nodes. But the disadvantage is that the hub represents a single point of failure. If the hub is down then the entire network becomes down.
Ans .
B
- Explanation :
The amount of uncertainty in a system of symbols is called Entropy
Ans .
C
- Explanation :
X.25 is used in packed switched network. The idea is to connect a dumb terminal to a packet-switched network.
Ans .
A
- Explanation :
Hot potato routing is a routing technique enabling packet routing without storing them in buffers. Instead, this technique continuously transfers data packets until they reach their destination without the packets having to wait or be stored in a buffer.
Ans .
C
- Explanation :
Start and stop bits are used in serial communications for Synchronization
Ans .
C
- Explanation :
Prototyping refers to an initial stage of a software release in which developmental evolution and product fixes may occur before a bigger release is initiated. These kinds of activities can also sometimes be called a beta phase or beta testing, where an initial project gets evaluated by a smaller class of users before full software release
Ans .
D
- Explanation :
A software requirements specification (SRS) is a description of a software system to be developed. It lays out functional and non-functional requirements, and may include a set of use cases that describe user interactions that the software must provide. Software requirements specification establishes the basis for an agreement between customers and contractors or suppliers (in market-driven projects, these roles may be played by the marketing and development divisions) on what the software product is to do as well as what it is not expected to do.
Ans .
C
- Explanation :
The cyclomatic number V(G) of a graph with n vertices, e edges and p connected component is
V(G) = e - n + p
Ans .
C
- Explanation :
Emergency fixes known as patches are result of Corrective Maintenance
Ans .
A
- Explanation :
Design recovery from source code is done during reverse engineering
Ans .
D
- Explanation :
Following is used to demonstrate that the new release of software still performs the old one did by rerunning the old tests : Regression testing
Ans .
C
- Explanation :
A binary tree is a data structure which has at most two child nodes. A binary tree can be traversed in three ways. Inorder, preorder and postorder. The three methods of traversal can be explained this way.
TYPE FIRST SECOND THIRD Inorder L - Left Ro - Root R - Right Preorder Ro - Root L - Left R - Right Postorder L - Left R - Right Ro - Root
Left will always be followed by right. But Root would be either in the front or in the middle or at the last depending on whether it is pre, in or postorder traversal. So given a post order traversal of a binary tree, we can know the root first. In the question, the post order traversal is given as DEBFCA. Since Root is the last node to be traversed in a post order traversal we know one thing for sure. A is the root.
Next, we are left with only DEBFC. Here some of the nodes belong to the left side of the binary tree and some belong to the right side. How many nodes belong to the left and how many belong to the right. Since left side of the binary tree is considered first, and since every node is expected to have at most two child, DEB will be the left side of the binary tree and FC would be the right.
Now, we know that FC is in the right side of the binary tree. Again the last node would be the root of the sub tree and F its left side.
Next we come to the left side of the binary tree and it is DEB. Again B would be the root of the sub tree. D and E are its left and right side respectively. So the binary tree would look something like this given below.
After constructing the binary tree, writing the preorder traversal is very simple. In preorder traversal root comes first. Since A is the root, A would appear first. Following Root would be the Left and Right sub tree and so the left subtree would be BDE. Again B would be the root of the left sub tree followed by D and E which are the left and right child respectively. SO the preorder traversal till now would be ABDE. Last comes the Right sub tree. Here again C would be the root of the right sub tree followed by C its left child. So the entire preorder traversal of the tree would be ABDECF. So option C is the right answer.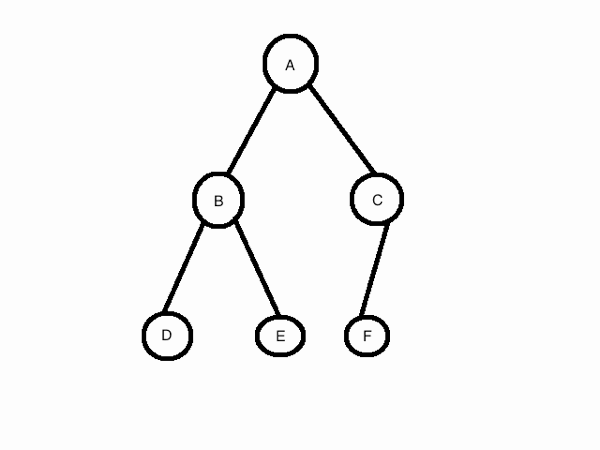
Ans .
B
- Explanation :
Disk access is slower compared to memory access. When we compare a binary tree to a B+ tree, B+ tree is supposed to have a higher fanout. What is a fanout actually?. B+ trees can store a relatively large number of pointers to child nodes in each node. Fanout means the number of pointers per node. B+ trees minimize the depth of the tree( and so one can reach the leaf node faster)by employing high fanout. That is linking many children from each node. Because of a high fanout the number of I/O operations required to find an element in the tree would be less. So B+ trees are preferred. The option is B.
Ans .
C
- Explanation :
ZAP deletes the entire file except the file structure
Ans .
A
- Explanation :
Actually the question should be which command is used for closing the text file, which has been created using SET ALTERNATE TO . The answer is SET ALTERNATE OFF. SET ALTERNATE ON directs the output to text file. OFF disables the output to text file.
Ans .
C
- Explanation :
Option B and D are completely ruled out. Since the question talks about data security threat choosing option C is correct than option A.
Ans .
A
- Explanation :
when structure of database file with 20 records is modified ? EOF ( ) Prints. T
Ans .
A
- Explanation :
The SQL Expression Select distinct T.branch name from branch T, branch S where T.assets > S.assets and S.branch-city = DELHI, finds the name of all branches that have greater asset than any branch located in DELHI.
Ans .
A
- Explanation :
Dijkestra banking algorithm in an operating system, solves the problem of deadlock avoidance
Ans .
A
- Explanation :
The multiuser operating system, 20 requests are made to use a particular resource per hour, on an average the probability that no request are made in 45 minutes is e-15
Ans .
B
- Explanation :
On receiving an interrupt from an I/O device, the CPU branches off to the interrupt service routine after completion of the current instruction
Ans .
B
- Explanation :
The maximum amount of information that is available in one portion of the disk access arm for a removal disk pack is a cylinder of data.
Ans .
D
- Explanation :
The question asks about the number of bits in the physical address. The word size is 1024. So, the number of bits required to calculate the offset into each page = 210=1024=10 bits.
So for 32 frames(25) of 1024 words each,we would require a total of 5+10 bits = 15 bits. Therefore the option is D.
Ans .
D
- Explanation :
Data transfer operation is performed by Bus Unit and Arithmetic and Logic operation are performed by ALU. So all the operation mentioned are not performed by CPU.
Ans .
B
- Explanation :
The number of gates for the different classification are as follows.
Small Scale Integration(SSI) - <10
Medium Scale Integration(MSI) - between 10 to 1000
Large Scale Integration(LSI) - >1000
Very Large Scale Integration(VLSI) - >100000
So the answer is option B.
Ans .
A
- Explanation :
the maximum value of unsigned integer is 216 –1.
Ans .
D
- Explanation :
Negative numbers can be represented in signed magnitude form, or '1' complement form or '2''s complement form. So the option is D.
Ans .
C
- Explanation :
Consider a cellular System
which has S duplex channels available for reuse.
Each cell allocated group of k channels (k < S)
S channels divided among N cells (unique and disjoint) then S = kN
Cluster: N cells, which completely use the complete set of available frequencies.
If a cluster is replicated M times in the system, the number of duplex channels C as a measure of capacity is C = MkN = MS
So capacity is directly proportional to the replication factor in a fixed area.
Factor N is called cluster size and is typically equal to 4,7,12.
If cluster size N is reduced while cell size is kept constant -more clusters are required, -more capacity is achieved
Large cluster size indicates that co-channel cells are far from each other
Conversely, small cluster size means co-channel cells are located much closer together
The value of N is a function of how much interference a mobile or BS can tolerate
Clusters are inversely proportional to N
-Capacity is directly proportional to Clusters
-Thus frequency reuse factor is given by 1/N.
Ans .
A
- Explanation :
- = in X - = Y + 1 means X = X - Y + 1
Ans .
A
- Explanation :
Handoff mechanism is used to transfer an ongoing call from one base station to another when person on call is moving or in vehicle and local base station area.
Ans .
C
- Explanation :
CFL's are closed under union, concatenation, and Kleene closure. But not under intersection or difference. So the correct answer is option C.
Ans .
B
- Explanation :
Electronic spamming is the use of electronic messaging systems to send an unsolicited message (spam), especially advertising, as well as sending messages repeatedly on the same site. While the most widely recognized form of spam is email spam. Other options are examples of real security and privacy risks.
Ans .
A
- Explanation :
The ATM adoption layer is not service dependent where as other statements about ATM networks are true.
Ans .
B
- Explanation :
Software risk estimation involves Risk probability and risk impact
Ans .
D
- Explanation :
The number of bits required for an IPv6 address is 128 bits and The number of bits required for an IPv4 address is 32 bits
Ans .
B
- Explanation :
The proposition ~ qvp is equivalent to q→p
As shown in the Truth Table below the columns for proposition P and option B are same so, ~ qvp is equivalent to q→p
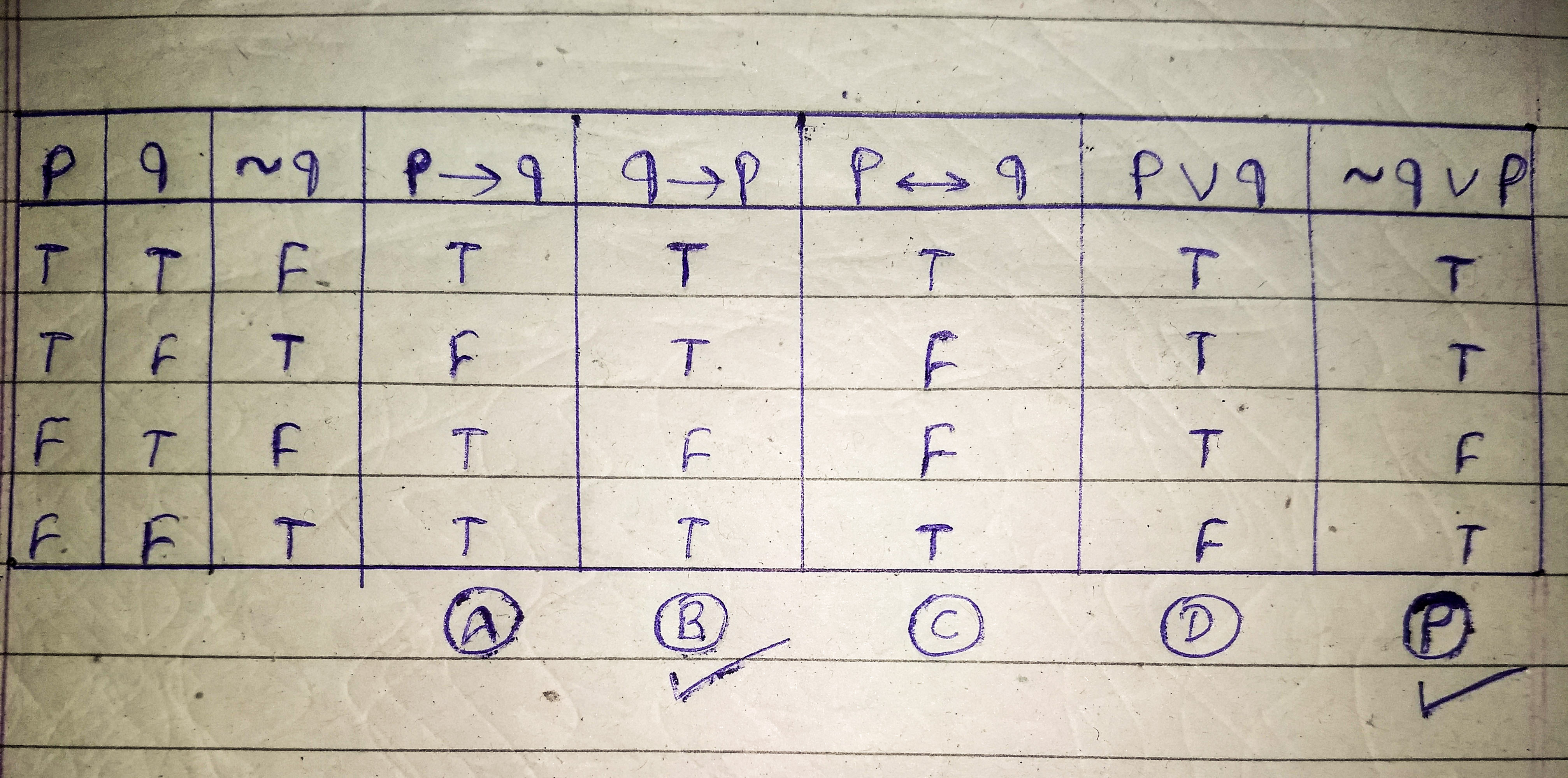
Ans .
D
- Explanation :
Enterprise Resource Planning (ERP) automate and integrates the majority of business processes.
Ans .
C
- Explanation :
ERP is expensive to implement.
Ans .
D
- Explanation :
To compare, overlay or cross analyze to maps in GIS All three options should satisfy.
Ans .
B
- Explanation :
Web Mining is used for Information filtering, Online transaction processing, Click stream analysis but it can not be used for Crime fighting on the internet
Ans .
B
- Explanation :
A telephone conference call is an example of same time / different place.
Ans .
A
- Explanation :
For options given here The probability of choosing correctly an unknown integer between 0 and 9 with 3 chances is 963/1000.
Options given here may be incorrect as many thinks answer for this question can be given as below:
Let call the unknown integer as X.
There is 10 options of X, that is 0, 1, 2, 3, 4, 5, 6, 7, 8, 9.
case 1: Correct guessing in the first guessing.
So for the first time correct, we have The chance is 1/10.
Since we have guessed it correct in the first time, we don't need to count the second guessing and the third guessing.
case 2: Correct guessing in the second guessing.
For the second time correct, we must have been guessed it wrong in the first chance, it's 9/10.
And for the correct guessing in the second guess, we only have 9 options left for X, since we will not choose the same number as we have guessed in te first guessing. So, it'll be 1/9.
So, the probability for this case is 9/10 * 1/9 = 1/10.
case 3: Correct guessing in the second guessing
We must have been guessed it wrong in the first and second guessing.
So, just like the previous case, the total probability for this case is 9/10 * 8/9 * 1/8 = 1/10
So, total probability is case 1 OR case 2 OR case 3 = 1/10 + 1/10 + 1/10 = 3/10
From this difficult explanation it's easy to prove that for N times guessing an integer which has M options, we have the probability is N/M
Hope this help.
Ans .
A
- Explanation :
The number of nodes in a complete binary tree of height h (with roots at level 0) is equal to 20 + 21 + ..... 2h
UPSCFEVER - POPULAR PAGES
Join The Movement
Discussions and Comments
- Explanation :