GATE-CS-2017 (Set 1)
Ans .
D
- Explanation :
162 = 3 * 3 * 3 * 3 * 2 To make it a perfect cube, we need at least 2 * 2 * 3 * 3 which is 36.
Ans .
C
- Explanation :
Assume, they are looking to the center of circular table, then the possible arrangement is:
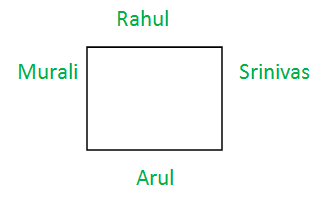
Ans .
D
- Explanation :
Grammatically, besides is an adverb or a preposition, and beside a preposition. Beside means next to. As a preposition, besides means in addition to or apart from. As an adverb, besides means as well or furthermore. Here, we use "besides" as a preposition meaning "in addition to". "besides money" is correct choice.
Ans .
C
- Explanation :
For 10 digits(0 to 9) total possible cases = (10)k Excluding digits 0, 5, 9, total possible cases = (7)k with numbers 1,2,3,4,6,7,8 Required probability = (7)k/(10)k= (0.7)k Therefore option C is correct.
Ans .
C
- Explanation :
According to the rule : when the main clause is in the past or past perfect tense, the subordinate clause must be in the past or past perfect tense.
Ans .
A
- Explanation :
There are atleast Two Men and Two Women. There are atleast 3 Right Handed People No women are Right Handed - infers there are three right handed men Every woman has a left-handed person to her immediate right - Means women circled in red needs to have a left handed person on her right and that too a man as on right side of ?? there is a right handed man. So, ?? - will be a left handed man
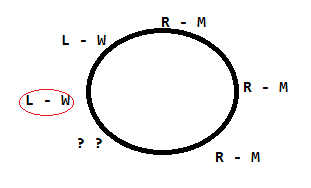 Therefore, option A (only 2 women) is correct.
Therefore, option A (only 2 women) is correct.
Ans .
B
- Explanation :
The author is trying to say that everything related to colonial past has a hold of nationalism in people’s imagination. It is not necessary that anything which is represented inadequately is the history. History and nationalism has a strong connection, but sometimes history is viewed with nationalism in mind. This is the author’s opinion.
Ans .
B
- Explanation :
As we know that, if x > y, then |x - y| = x - y and if x < y then |x - y| = y - x , because value of |x - y| is always non-negative. Therefore, Case 1: If x > y : (x + y) - |x - y| ] / 2 = (x + y) - (x - y) ] / 2 = 2y / 2 = y (Minimum of x , y) Case 2: If x < y : (x + y) - |x - y| ] / 2 = (x + y) - (y - x) ] / 2 = 2x / 2 = x (Minimum of x , y) Therefore in both the case we get minimum of (x,y). So, option B Note that you can take some random values of x and y, then verify given options.
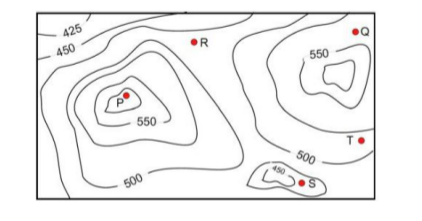
If in a flood, the water level rises to 525 m, which of the villages P, Q, R, S, T get submerged?
Ans .
C
- Explanation :
Given data - height of all villages P = 575 Q = 525 R = 475 S = 425 T = 500 Villages below the flood level - 525m are R <500m 425m<= S<=450m 500m <=T<= 525m Therefore option C is correct.
Ans .
D
- Explanation :
Total number of Shirts = 4 , Total candidates =4 So total combination of possibilities = 4 X 4 = 16 No.of ways 'Arun chooses red' + No.of ways Shwetha chooses white '= 2 Therefore, Answer is 16-2 = 14.
Ans .
A
- Explanation :
Here, half of the values of Y are to the left of the mean X = 0 and the remaining half of the values of Y lies to the right of the mean X = 0. hence,The median of Y = 0.
Ans .
D
- Explanation :
Client has sent FIN segment to the server and moves to FIN-WAIT-1, i.e. waiting for the ACK for own FIN segment. There are two possibilities here : 1.If Client receives ACK for its FIN then client will move to FIN-WAIT-2 and will wait for matching FIN from server side. After receiving the FIN from server, client will send ACK and move to TIME-WAIT state. 2.Client has sent FIN segment but didn’t get ACK till the time. Instead of ACK, client received FIN from server side. Client will acknowledge this FIN and move to CLOSE state. Here Client will wait for the ACK for its own FIN. After receiving ACK, client will move to TIME-WAIT state. Here we encounter First Case. So, the solution is (D).
Ans .
B
- Explanation :
First let’s know what is Birthday attack : Using Birthday Attack, some fraudulent message can be generated which has same hash value and digital signature as the original message. But this question is more about Private Key. Let’s analyse each option one by one - I. Instead of intended message, Sender can take some fraudulent message and encrypt it with own private key and then receiver’s public key. This is POSSIBLE. II. Third party don’t have that Private Key to encrypt the message. So this is NOT possible. III. And the same way R also don’t have that Private key to encrypt the message. So, the only possibility is - (I) S can launch a birthday attack to replace m with a fraudulent message. Option (B) is correct.
Ans .
B
- Explanation :
According to Static Single Assignment 1. A variable cannot be used more than once in the LHS 2. A variable should be initialized atmost once. Now looking at the given options * a - code violates condition 1 as p1 is initialized again in this statement: p1 = u * v * c- code is not valid as q1 = p2 * c , q2 = p4 + q3 - In these statements p2, p4, q3 are not initialized anywhere * d- code is invalid as q2 = p + q is incorrect without moving it to register Therefore,Option (B) is correct.
Ans .
A
- Explanation :
Given
V -> W VW -> X Y -> VX Y -> Z
We need to find the minimal cover of these FDs Option B. W->X can not implied by the given FDs, so incorrect Option C. Y->X can be implied from Y->V and V->X, hence redundant Option D. W->X can not implied by the given FDs, so incorrect Option A. Minimal cover of dependencies that can be extracted out as V -> W V -> X Y -> V Y -> Z Therefore, option A is most appropriate
Ans .
C
- Explanation :
Given, with arrival time and burst time:
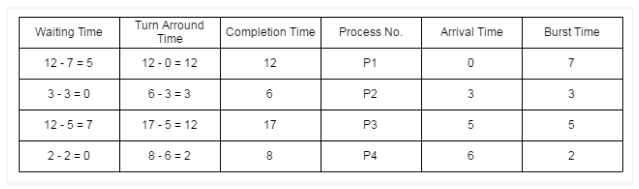 Using (preemptive) shortest remaining time first algorithm, gantt chart is:
Using (preemptive) shortest remaining time first algorithm, gantt chart is:
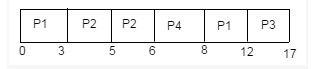 Therefore, Average waiting time = ( 5 + 0 + 7 + 0 ) / 4 = 12 / 4 = 3
Therefore, Average waiting time = ( 5 + 0 + 7 + 0 ) / 4 = 12 / 4 = 3
Ans .
B
- Explanation :
* The minimum height of a binary search tree will be when tree is full complete tree: So, Min height of a binary search tree = log2(n+1) - 1 = log2(15+1) - 1 = 4 - 1 = 3 * The maximum height of a binary search tree will be when the tree is fully skewed So, Max height of the binary search tree = n-1 = 15 - 1 = 14.
Ans .
D
- Explanation :
Given, (¬ p) → (¬ q) = ¬ (¬ p) ∨ (¬ q) { since x → y = ¬ (x) ∨ y } = (¬ ¬ p) ∨ (¬ q) = (p) ∨ (¬ q) {Using double negation rule} = (¬ q) ∨ (p) (it is equivalent to statement (iii)) = (q) → (p) { since x → y = ¬ (x) ∨ y } (it is equivalent to statement (ii)) So, option (D) is correct
Ans .
C
- Explanation :
Output of Query will be: DeptName Number AA 4 AB 3 AC 3 AD 2 AE 1 4 + 3 + 3 + 2 + 1 = 13 / 5 = 2.6
Ans .
D
- Explanation :
Thread share all other resources of process except local data like - register , stack. So, option (D) is correct
Ans .
C
- Explanation :
The vectors a1, a2, …, an are linearly dependent. For the system AX = B, Rank of coefficient matrix A = Rank of augmented matrix (A / B) = k (k< n) Hence, the system has infinitely many solutions.
Ans .
B
- Explanation :
Given, first order logic sentence F: ∀x (∃y R(x, y)) with following sentences: (i) ∃y (∃x R(x, y)) is true. Because we have ∀x (∃y R(x, y)) → ∃x (∃y R(x, y)) → ∃y (∃x R(x, y)). (ii) ∃y (∀x R(x, y)) is false. Because we have ∀x (∃y R(x, y)) ← ∃y (∀x R(x, y)). (iii) ∀y (∃x R(x, y)) is false. Because for ∃y can not imply ∀y. (iv) ∼∃x (∀y ∼R(x, y)) is true. Because ∼∃x (∀y ∼R(x, y)) = ∀x (∼ ∃y ∼R(x, y)) = ∀x (∃y ∼∼R(x, y)) = ∀x (∃y R(x, y)).
Ans .
C
- Explanation :
Follow of Q is first of R so we get {w} but since R can be Null so we have to check first of S which is {y} so FOLLOW Q={w,y}
Ans .
A
- Explanation :
Miss rate of L2 cache = (memory references generated by L2 cache) / (memory references generated by L1 cache) = 7 / 140 = 0.05
Ans .
B
- Explanation :
For the large number, value of inverse of number is less than a constant and value of constant is less than value of square root. 10 is constant, not affected by value of n. √n Square root and log2n is logarithmic. So log2n is definitely less than √n. n has linear growth and 100/n grows inversely with value of n. For bigger value of n, we can consider it 0, so 100/n is least and n is max. So the increasing order of asymptotic complexity will be :
100/n < 10 < log2n < √n < n
Ans .
D
- Explanation :
The address of student grade can only be accessed by using the base address of Student. * Post-increment addressing mode. (R1)+ - Will give the next address and not the desired grade address * Pre-decrement addressing mode, -(R1) - Will give the previous address and not the desired grade address * Register direct addressing mode, R1 : In this mode, the address of the operand is embedded in the instruction code. * Index addressing mode: It is the only mode which gives access to next address by adding displacement in base address using displacement mode. * Base register contains a pointer to a memory location. An integer (constant) is also referred to as a displacement. * The address of the operand is obtained by adding the contents of the base register plus the constant. Therefore, option D is correct
Ans .
D
- Explanation :
This statement assigns a location to x. Now, (int*)malloc(sizeof(int)); again assigns a new location to x , previous memory location is lost because now we have no reference to that location resulting in memory leak. Therefore, option D is correct
Ans .
A
- Explanation :
Solving the above k- map = ca = ac = (a' + c')' Since complement of variables are also available. So, this can be implemented using one NOR gate. Therefore, option A is correct
.png)
Ans .
C
- Explanation :
Kruskal’s is a greedy technique of Minimum Spanning Tree Algorithm to find an edge of the least possible weight that connects any two trees in the forest. QuickSort is a Divide and Conquer algorithm. It picks an element as pivot and partitions the given array around the picked pivot. Floyd Warshall Algorithm is for solving the All Pairs Shortest Path problem using Dynamic Programming. The problem is to find shortest distances between every pair of vertices in a given edge weighted directed Graph.
Ans .
B
- Explanation :
As it is stated in the question, that m and n are valid Lists but not explicitly specified if the lists are empty or not. We can have two cases: 1. Case 1: If lists are not NULL : Invocation of join will append list m to the end of list n if the lists are not NULL. For Example:Before join operation : m =1->2->3->4->5->null n =6->7->8->9->nullAfter join operation : 6->7->8->9->1->2->3->4->5->null 2. Case 2: If lists are NULL : If the list n is empty and itself NULL, then joining and referencing would obviously create NULL pointer issue. Therefore option B is correct
Ans .
B
- Explanation :
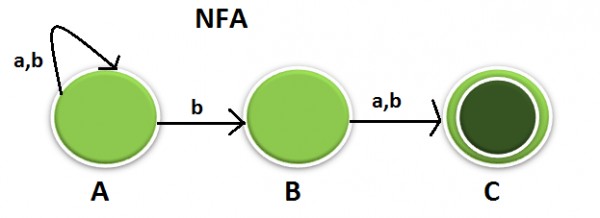
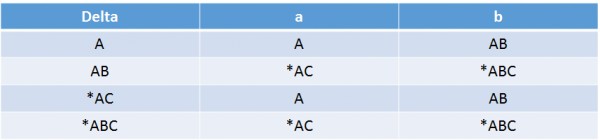
NFA to DFA Conversion: In the STT below you can see 4 states are there but before confirming the ans lets try to minimize, It cant be minimized further because A goes to Nonfinal & AB goes to Final hence can not be merged. Similarly *AC goes NF & *ABC goes to F hence can not be merged. Hence 4 is the final ans.
Ans .
D
- Explanation :
Since given number is in unsigned bit representation, its decimal value starts with 0. We have i bit in integral part so maximum value will be 2i Thus integral value will be from 0 to 2i - 1 We know fraction part of binary representation are calculated as (1/0)*2-f Thus with f bit maximum number possible = sum of GP series with a = 1/2 and r = 1/2 Thus fmax = {1/2(1 – (1/2)f}/(1 – 1/2) = 1 – 2-f Thus maximum fractional value possible = 2i – 1 + (1 – 2-f ) = 2i - 2-f
Ans .
A
- Explanation :
Given, v= Total vertices = 10 e = v - 1 =9 Degree = 2 * e = 18 Therefore, option A is correct
Ans .
B
- Explanation :
Let’s generate a string from given grammar : S → abScT → ab abScT cT → abab abcT cTcT → abababc bT cTcT → abababcb bT cTcT → abababcbb bT cTcT → abababcbbbb cTcT → abababcbbbbc b cT → abababcbbbbcbc bT → abababcbbbbcbcbb. This string can rule out all wrong options. Now let’s try to analyse this string. abababcbbbbcbcbb → {(abncbm1cbm2...cbmn | n, m1, m2, ....., mn >= 1 } We can clearly rule out option (A), (C) and (D) with help of the string generated by given grammar. Only option (B) is correct.
Ans .
C
- Explanation :
Overflow indicates that the result was too large or too small to fit in the original data type. Overflow flag indicates an overflow condition for a signed operation. Signed numbers are represented in two's complement representation. The overflow occurs only when two positive number are added and the result is negative or two negative number are added and the result is positive. Otherwise, the sum has not overflowed. Therefore, a XOR operation can quickly determine if an overflow condition exists. i.e., (A7 . B7 )⊕(S7) = (A7 . B7 . S7‘ + A7‘ . B7‘ . S7 = 1
Ans .
D
- Explanation :
A SAFE EXPRESSION is one that is guaranteed to yield a finite number of tuples as its results. Otherwise, it is called UNSAFE Given, DepId can be permitted to be NULL I. {t | ∃ u ∈ EMP (t[EMPName] = u[EmpName] ∧ ∀ v ∈ DEPT (t[DeptId] ≠ DeptId]))} : Gives empnames who donot belong to any department II. {t | ∃ u ∈ EMP (t[EMPName] = u[EmpName] ∧ ∃ v ∈ DEPT (t[DeptId] ≠ DeptId]))} : Gives empnames who donot belong to some department III. {t | ∃ u ∈ EMP (t[EMPName] = u[EmpName] ∧ ∃ v ∈ DEPT (t[DeptId] = DeptId]))}: Gives empnames who donot belong to same department All of these queries are giving some results which are finite and thus all are safe expressions. Therefore, option D is correct.
Ans .
A
- Explanation :
I. Minimum Spanning Tree of G is always unique - MST will wlways be distinct if the edges are unique so Correct II. Shortest path between any two vertices of G is always unique - Shortest path between any two vertices can be same so incorrect. Therefore, option A is correct.
Ans .
A
- Explanation :
The assembly code using the load/store architecture can be written as follows: Load R1, b Load R2, c ADD R1, R2 Div R1, 3 Load R2, d Add R1, R2 Load R2, a Sub R2, 1 Mul R2, R1 Hence minimum 2 registers required.
Ans .
C
- Explanation :
In the function foo every time in the while foo is called with the value 3 because val is passed with post decrement operator so the value 3 is passed and val is decremented later. Every time the function is called a new variable is created as the passed variable is passed by value, with the value 3. So the function will close abruptly without returning any value. In the function bar, in the while loop value the value of val variable is not decrementing, it remains 3 only. Bar function in the while loop is called with val-1 i.e 2 but value of val is not decremented, so it will result in infinite loop.
Ans .
D
- Explanation :
The expression (r → p) → q is always true when q is true, regardless of the value of the expression (p → q) → r.
Ans .
A
- Explanation :
Instruction Bytes i 0-3 i+1 4-7 i+2 8-11 i+3 12-15 Next Instruction 16 According to PC Relative Mode, Effective PC address = next instruction address + offset 0(i) = 16 + offset 0-16 = offset Offset = -16
Ans .
B
- Explanation :

Ans .
D
- Explanation :
If we notice the productions of this grammar S->aSb | bSa | SS | ∈ these productions will always produce number of a's and b's equal. Also , S-> SaS this production may add more number of a's to number of a's and b's produced by the productions above. So all, in all this grammar is generating Number of a's = Number of b's or Number of a's are greater than number of b's If we check option (d), it has more number of b's than a which surely cannot in no way be generated by this grammar.
Ans .
A
- Explanation :
In an RSA cryptosystem, for public key: GCD( ϕ(n) , e) = 1 And, for private key: (e * d) mod ϕ(n) = 1 Where, ϕ(n) = (p -1)*(q - 1) = (13 - 1)(17 - 1) =12*16 = 192 Such that 1 < e, d < ϕ(n) Therefore, the private key is: (35 * d) mod ϕ(n) = 1 d = 11
Ans .
B
- Explanation :

Ans .
A
- Explanation :
Given, if TS(T2) < TS(T1) then T1 is killed else T2 waits. * T1 holds a lock on the resource R * T2 has requested a conflicting lock on the same resource R According to algo, TS(T2) < TS(T1) then T1 is killed else T2 will wait. So in both cases neither deadlock will happen nor starvation. Therefore, option A is correct
Ans .
A
- Explanation :
Given, Number of bytes in the information frame = 1980 Number of bytes in the acknowledge frame = 20 Number of overhead bytes in the information frame = 20 Therefore, useful Data = Total Data – Overhead = 1980 - 20 = 1960 Tt(Data) = (1960*8) / 10^6 = 15.68 millisecond Tt(ACK) = 20*8 / 10^6 = 0.16 millisecond Two way round trip time = 2 * Tp = 2*0.75 = 1.5 millisecond T(precess) = 0.25(for info) + 0.25(for ack) = 0.5 millisecond Efficiency = Useful Time / (Tt(info) + + Tt(ACK) + 2* Tp + Tprocess ) = 15.68 / (15.84 + 0.16 + 2*0.75+ 0.5 ) = 0.8711111 = 87% Option (A) is correct.
Ans .
C
- Explanation :
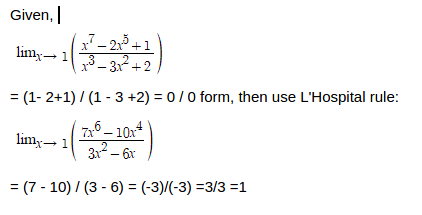
Ans .
A
- Explanation :
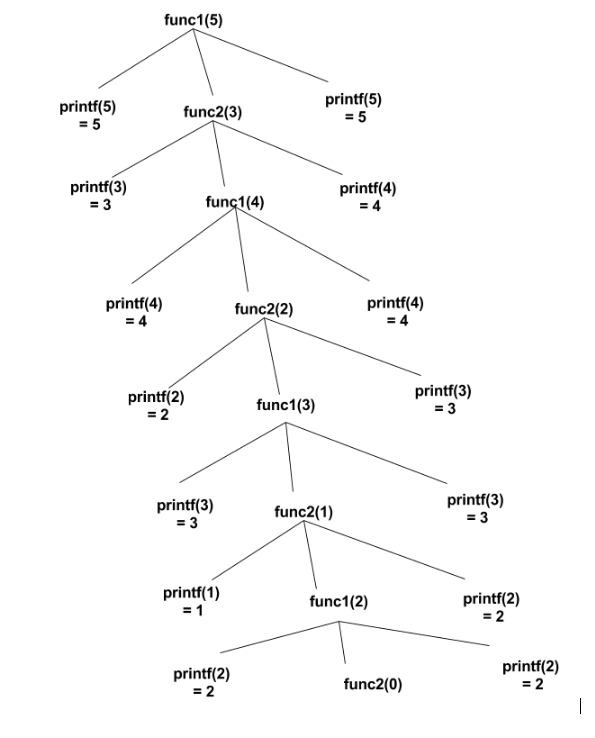
Ans .
B
- Explanation :
In first iteration there are 4 conflict misses and 6 compulsory misses. In second iteration, there are 4+4 = 8 conflict misses and this is the same for iterations 3..10. So, totally 8×9+4=76 conflict misses.
Ans .
C
- Explanation :
We add (n-1) 0's to the LSB of dividend(message) and divided by given GF
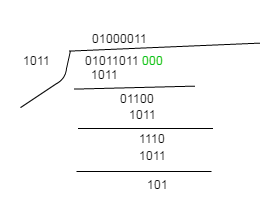 The remainder will be CRC, it will be added to the LSB of the original message, that should be transmitted to the receiver. That is: 01011011101.
The remainder will be CRC, it will be added to the LSB of the original message, that should be transmitted to the receiver. That is: 01011011101.
Ans .
A
- Explanation :
Union of context free language is also context free language. L1 = {an bncm | m, n >= 0 } and L2 = {ambncn| m, n >= 0} L3 = L1 ∪ L2 = { an bncm ∪ ambncn| n >= 0, m >= 0 } is also context free. L1 says number of a’s should be equal to number of b’s and L2 says number of b’s should be equal to number of c’s. Their union says either of two conditions to be true. So it is also context free language. Intersection of CFG may or may not be CFG. L3 = L1 ∩ L2 = { an bncn| n >= 0 } need not be context free.
Ans .
B
- Explanation :
Number of control flow paths for 10 if terminals if then else ; stmt if then else ; if then else ; stmt .............. 10 times. Observe that there is a semi-colon after every if structure. Since, every if structure has 2 control flows. Therefore, 1st terminal has 2 control flows, 2nd terminal has 2 control flows, 3rd terminal has 2 control flows, ........... 9th terminal has 2 control flows, and 10th terminal has 2 control flows. Using multiplication law of counting, we get = 2*2*2*2*2......10 times = 2^10 = 1024 number of control flow paths for 10 if terminals. 1024 is correct answer.
Ans .
D
- Explanation :
1)Reentrant (Recursive) locks allow a thread to reacquire the lock. That means same process can claim the lock multiple times without blocking on itself. This prevents the thread from deadlocking itself. This is main advantage of reentrant locks over non-reentrant locks. 2)Non-reentrant (Non- recursive) locks not allow a thread to reacquire the lock. That means same process can not claim the lock multiple times without releasing it. So, if a thread/process is unable to acquire a lock, it blocks until the lock becomes available. This situation is deadlocked. 3)Therefore, only one thread and only one lock can cause deadlock, if thread does try to reacquire lock.
Ans .
B
- Explanation :
((strlen(s) - strlen(t)) > c) ? strlen (s) : strlen (t) = (3 - 5 > 0) = (-2 > 0) Important point here is while comparing -2 with c, result will be a positive number as c is unsigned. So, out of these two , strlen (s) will be printed. Therefore, option B is correct.
Ans .
B
- Explanation :
Type of mapping is direct map; for this direct map, 10 bits are required in itss Tag. It is updated to 16 way set Associative map then new tag field size = 10 + log216 = 14 bits, because for k way set associative map design, log2k bits are additionally required to the number of bits in tag field for Direct map design.
Ans .
D
- Explanation :
The best way to solve such a problem is by using Binary Search. Search the sorted array by repeatedly dividing the search interval in half. Begin with an interval covering the whole array. If the value of the search key is less than the item in the middle of the interval, narrow the interval to the lower half. Otherwise narrow it to the upper half. Find mid element -Is mid = 1 ? -Is mid >1?(not possible here) -Is mid < 1 ? Proceed accordingly, Worst case of this problem will be 1 at the end of the array i.e 00000.....1 OR 1.......0000. It will take log n time worst case. n=31, Hence log 231 = 5. Therefore, option D is correct.
Ans .
C
- Explanation :
The general formula for the union of 3 sets is: (A union B union C) = A + B + C - (A intersect B) - (A intersect C) - (B intersect C) + (A intersect B intersect C). Assuming, A = 3, B = 5, C = 7 = 500/3 + 500/5 + 500/7 - 500/3*5 - 500/5*7 - 500/7*3 + 500/105 = 271 Therefore, option C is correct.
Ans .
C
- Explanation :
Result of T1: CA CB CC Result of T2 = CR/T1 SA SC SD SF Total = 4 Therefore, option C is correct
Ans .
B
- Explanation :
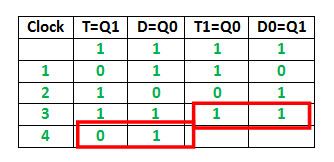 It can be observed from the diagram that : Q1 Q0 after the 3rd cycle are 11 and after the 4th cycle are 01
Therefore, option B is correct
It can be observed from the diagram that : Q1 Q0 after the 3rd cycle are 11 and after the 4th cycle are 01
Therefore, option B is correct
Ans .
A
- Explanation :
|u| = 2|v| =|2v|. So u and 2v are vectors of the same length in directions of u and v, so their sum u+2v bisects the angle. w = u + αv = u + 2 v That is α = 2 Because, If we have two vectors with equal magnitude in the direction of given vectors, then their sum will bisect the angle between them.
Ans .
A
- Explanation :
This definition is given as Halting of Turing Machine. Every recursive language is computable, but converse may not be true.
Ans .
B
- Explanation :
Belady’s anomaly proves that it is possible to have more page faults when increasing the number of page frames while using the First in First Out (FIFO) page replacement algorithm. For example, if we consider reference string 3 2 1 0 3 2 4 3 2 1 0 4 and 3 slots, we get 9 total page faults, but if we increase slots to 4, we get 10 page faults. S1: Random page replacement algorithm (where a page chosen at random is replaced) suffers from Belady’s anomaly. -> Random page replacement algorithm can be any including FIFO so its true S2: LRU page replacement algorithm suffers from Belady’s anomaly . -> LRU does'nt suffer from Belady’s anomaly . Therefore, option B is correct
Ans .
A
- Explanation :
Digits : 5-0101, 4-0100, 3-0011, 2-0010, 1-0000 Countof 1s : 2, 3, 5, 6, 7 Total: 2+3+5+6+7 = 23 Therfore, option A is correct
Ans .
A
- Explanation :
Given, total number of instructions (n) = 20 For naive pipeline (NP): Number of stages(k) = 5 Clock time (Tp) = max { (stage delay+buffer delay) } = { 7, 6, 22, 12, 5 } = 22 nsec Execution time (Enp) = ( k + n - 1 )*Tp = ( 5 + 20 - 1 )*22 = 528 nsec For efficient pipeline (EP): number of stages(k) = 6 ( delay with 20 nsec stage is divided into 12 nsec and 8 nsec ) Clock time (Tp) = max { (stage delay+buffer delay) } = { 7, 6, 14, 10, 14, 5 } = 14 nsec Execution time (Eep) = ( k + n - 1 )*Tp = ( 6 + 20 - 1 )*14 = 350 nsec Therefore, Speedup = (Enp) / (Eep) = 528 / 350 = 1.508