GATE-CS-2017 (Set 2)
Ans .
B
- Explanation :
Let us consider all choices : Choice A : 12 [Wrong] There is no integer x that satisfies below equation 12 * 3 + x * 11 = 100 x = 64/11 [Which is not an integer] Choice B : 15 [Right] 15 * 3 + x * 11 = 100 x = 55/11 = 5 Choice C : 18 [Wrong] There is no integer x that satisfies below equation 18 * 3 + x * 11 = 100 x = 46/11 [Which is not an integer] Choice D : 19 [Wrong] There is no integer x that satisfies below equation 19 * 3 + x * 11 = 100 x = 43/11 [Which is not an integer]
Ans .
A
- Explanation :
V is to the West of W, V W Z is to the East of X and the West of V. X Z V W W is to West of Y. X Z V W Y Therefore, V is in middle. So option A is correct.
Ans .
B
- Explanation :
With adjectives and adverbs, enough comes after adjectives and adverbs. With nouns, enough comes before noun. In the given question, enough is used with bright which is an adjective, so enough will come after the adjective. So bright enough is the correct option.
Ans .
D
- Explanation :
Ways to collect both Red = 3C2 Ways to collect both Green = 4C2 Ways to collect both Blue = 3C2 Total Ways = 10C2 P(Socks of Same Colour) = (3C2 + 4C2+ 3C2 ) / 10C2 = 4/15 Therefore, Option D is correct
Ans .
D
- Explanation :
Yield - produce or provide Resistance - the refusal to accept or comply with something. Rest are all synonyms. Hence, (D) is correct.
Ans .
C
- Explanation :
The given function is a continuous function in range [-5, 5]. The Intermediate Value Theorem states if a continuous function has values of opposite sign inside an interval, then it has a root in that interval. The function changes sign twice in range [-5, 5]. It becomes positive to negative in range [-5, 0] when ex + 0.5x2 becomes less than 2. It becomes positive to negative in range [0, 5] when ex + 0.5x2 becomes more than 2.
Ans .
B
- Explanation :
In given question there are three boxes incorrectly labeled: Box 3 labeled as Apples and Oranges - Original Content can be Apple or Orangle (This box will have only one fruit, so whichever we pick would be the correct label). Let's say the picked item was Apple, therefore the box labeled Orange will have Apples and Oranges.) Box 2 - Oranges - This box will definitely not have orange (as its mislabeled) and it can not contain only apple (As it is in box 3) So this will have Original Content- both oranges and Apples Box 1 - Apples - This is the leftover box and it can now have Original Content - Orange Therefore option B is correct.
Ans .
A
- Explanation :
X = 4777....(till 30 digits) or X = 4.7777? * 1029 X29 = (4.777?*1029 )3 = (4.777...)3 * 10 87 So, (X3 )3 requires 3 + 87 = 90 digits. Therefore, option A.
Ans .
B
- Explanation :
This paragraph is taken from the book - Reading Lolita in Tehran by- AZAR NAFISI. "Seemingly" means appearing to be something which is Not True. Or, not what its look like. Author is criticizing the fake ideology of Iranian politics. Author is trying to say that Literature is more important than fake ideology. But this is how she is expressing- ..... they were handmaidens to something seemingly more urgent - namely ideology.. means- Ideology is not more important than litrature. So, (B) seemingly is CORRECT.
Ans .
D
- Explanation :
Region R has maximum air pressure variation as it which has maximum number of lines crossing the area. Therefore option C is correct Alternate Solution We have to see for the region which has maximum change in air pressure for thunderstorm. In region P : the air pressure changes only once by 0.05 as only 2 lines are crossing the region. The first line with the air pressure 0.95 and the next one is with pressure 0.9. In region Q : No line crosses the region which implies that the air pressure doesn't change. In region R : the air pressure changes at 4 places resulting in maximum change in air pressure in the whole region. The minimum pressure in R is 0.65 and the maximum is 0.8. In region S : the air pressure in the region in 0.95 and other contouring line is outside the region thus no change in air pressure within the region. Thus the probability of thunderstorm is maximum in region R.
Ans .
A
- Explanation :
It is not raining (~p) and it is pleasent (r) : (¬p ∧ r)
It is raining (p) and it is cold (q) : (p∧q) it is not pleasant (¬r) only if it is raining and it is cold : ¬r → (p∧q)
So the answer should be- (¬ p ∧ r) ∧ ((¬ r → (p ∧ q)) So, option (A) is true.
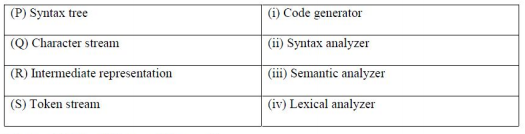
Ans .
C
- Explanation :
P - iii Syntax tree is input to semantic analyser Q - iv Character stream is input to lexical analyser.
R - i Intermediate code is input to code generator S -ii Token stream is input to syntax analyser. Therefore option C.
Ans .
D
- Explanation :
In contiguous allocation there is always possibility of external fragmentation. Both indexed and linked allocation are free from external fragmentation.Therefore, option D
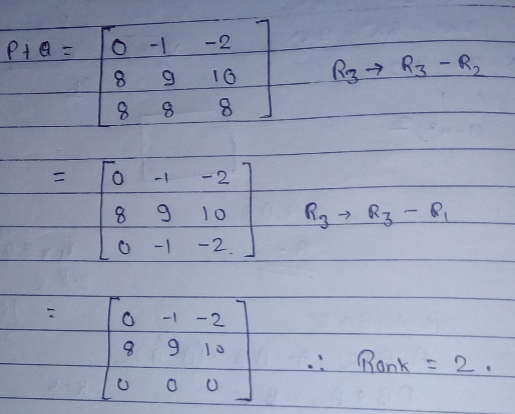
Ans .
B
- Explanation :
Ans .
D
- Explanation :
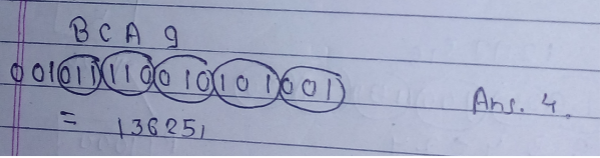
Ans .
C
- Explanation :
In one to many or many to one participation, relation is merged in table which is on many side and if there is total participation then relation is merged in that side.
Therefore, option C is correct
Ans .
C
- Explanation :
- Tower of Hanoi - Ɵ(2n)
- Heap sort worst case - Ɵ(n log n)
- Binary Search - Ɵ(log n)
- Addition of two nxn matrices - Ɵ (n2)
Ans .
C
- Explanation :
RIP uses distance vector routing (DVR) protocol which employ the hop count as a routing metric. Also, RIP uses the UDP as its
transport protocol with port no 520. OSPF uses link state routing (LSR) protocol works within a single Autonomous System. OSPF encapsulates its data
directly into IP Packets and does not use either TCP or UDP. Therefore, statement (III) is false and only statements I, II and IV are correct. Option (C) is true.
Ans .
C
- Explanation :

Ans .
B
- Explanation :
In IPV4 frame format there are 40 bytes of option field, out of which only 38 bytes can be used, 2 bytes are reserved . Also one IPV4 adress is of 4 bytes Thus maxmimum IPV4 address that can be hold <= 38/4 = 9
Ans .
A
- Explanation :
Given, Q -> R(Primary Key) S -> P (Primary Key) Entry to be deleted - P (3) and Q(8) Q can be deleted directly Now, S - > P but the relationship given is on delete set NULL, Therefore when we delete 3 from T1 ,the entry in T2 having 3 will be NULL. Therfore, Option A - Answer is 0 entries
Ans .
D
- Explanation :
In BFS, we print a starting node, then its adjacent, then adjacent of adjacent, and so on.. Option A : MNOPQR Wrong We cannot visit "O" before "R" as we start from "M". Note that "O" is adjacent of adjacent for "M" and "R" is adjacent of "M". Option B : NQMPOR Wrong We cannot visit "P" before "O" as we start from "N". Note that "P" is adjacent of adjacent for "N" and "O" is adjacent. Option C : QMNROP Wrong We cannot visit "R" before "O" as we start from "Q". Note that "R" is adjacent of adjacent for "Q" and "O" is adjacent of "Q" Option D : POQNMR Right We visit "P", then its adjacent "O", "Q" and "N" Finally we visit adjacent of adjacent "M" and "R"
Ans .
B
- Explanation :
I. A connected UDP socket can be used to communicate with multiple peers simultaneously is WRONG :
Even if UDP is connectionless, every UDP socket has a single specified IP number and port number to connect to.
Therefore we can not use same socket to connect to multiple peers simultaneously.
II. A process can successfully call connect function again for an already connected UDP socket is RIGHT : We can call connect again to connect to a new
peer and disconnect previous peer if implementation allows.
Ans .
B
- Explanation :
Context free language are closed under union and difference with regular language. It is not closed under complementation and intersection . Complement of CFL is recursive language .
Ans .
A
- Explanation :
- static char var; -> A variable located in data section of memory as it is static in nature
- m = malloc(10); m = null; ->This is a lost memory which cannot be freed as m=NULL
- Char *Ptr[10]; -> 10 memory locations of char type are allocated to store addresses
- register int var1;-> Request to allocate a CPU register to store data
Ans .
C
- Explanation :
S --> XY X --> aX | a // This produces only "a" Y --> aYb | ∈ // This produces and "a" for every "b" Option (A) and (B) are wrong because n can be zero also due to epsilon in Y Option (D) is wrong because Y-->aYb produces equal number of a's and b's. Since there is one variable X which produces at least one a. Therefore numbers of a's are always greater than numbers of b's.
Ans .
C
- Explanation :
TAs per handshaking lemma, Sum of degree of all vertices < = 2 * no. of edges. Let v be number of vertices in graph. ==> 3*v <= 2*25 ==> Minimum value of v = 16
Ans .
C
- Explanation :
In 32-bit IEEE-754 format 1st bit represent sign 2-9th bit represent exponent and 10-32 represent Mantissa (Fraction part) Sign = 0, so positive 2-9 bits — 01111100 when subtracted by 01111111 i.e., 126 decimal value gives -> 0000 0011 Which is -3.(negative as the value is less than 126) As number is less than 126 it is subtracted otherwise 126 would have been subtracted from it in 32 bit representation. (https://www3.ntu.edu.sg/home/ehchua/programming/java/datarepresentation.html) Mantissa is normal ,hence, 1.M can be used .Which is 1.1101101. Thus, Data + 1.1101101 * 2^-3 (±M * B^(±e) ) Mantissa shift right 3 times -> +0.0011101101 = 0.228 = 2.28 * 10^-1 Thus, option c is correct.
Ans .
B
- Explanation :
Since, Circular queue deletes an item using Front pointer and insert an element using Rear pointer. If we want to insert an element into circular queue then we have to
increment Rear pointer to next node then insert element. Then after update the next pointer of Rear node to the Front node. This method will have O(1) time for Insertion
and Deletion. Only statement (ii) is true. So, option (B).
Ans .
C
- Explanation :
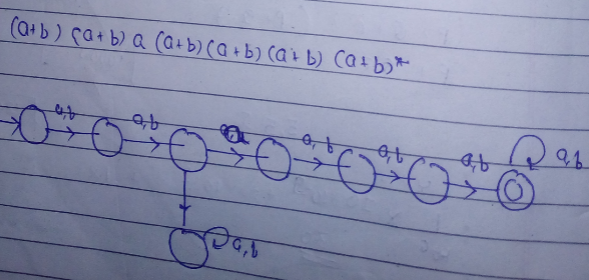
Ans .
A
- Explanation :
LR parsers in term of power CLR > LALR > SLR > LR(0) Therefore, Option A is only correct option
Ans .
D
- Explanation :
x2 – 13x + 36 = 0 ==> x2 – (b + 3)x + (3*b + 6) = 0 ….. { expanding numbers in base b ) putting the values of x we get b = 8.
Ans .
A
- Explanation :
Here in the given lattice a should be related as (a,a) , (a,b), (a,c), (a,d), (a,e) b: (b,c), (b,e), (b,b). c: (c,c), (c,e) d: (d,d), (d,e) e: (e,e) all pairs are already present here . Thus answer will be zero.
Ans .
B
- Explanation :
Every thread have its own stack , register, and PC, so only address space that is shared by all thread for a single process. Therefore, option B is correct.
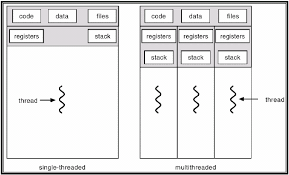
Ans .
C
- Explanation :
#include void main() { int x = 1, y = 1; printxy(x,y); } void printxy(int x, int y) { int *ptr; x = 0; // ptr point to variable of value 0 ptr = &x; // y has value pointed by ptr -> x= 0; y = *ptr; // value pointed by ptr is set to 1 -> x= 1; *ptr = 1; //x be changed to 1 and y will remain 0 printf("%d,%d", x, y); }
Ans .
D
- Explanation :
 Therefore, option D is correct.
Therefore, option D is correct.
Ans .
A
- Explanation :
Since, L2 cache is shared between Instruction and Data. Average Instruction fetch Time = L1 access time + L1 miss rate * L2 access time + L1 miss rate * L2 miss rate * Memory access time = 2 + 0.2 * 8 + 0.2 * 0.1 * 90 = 5.4 ns
Average Data fetch Time = L1 access time + L1 miss rate * L2 access time + L1 miss rate * L2 miss rate * Memory access time = 2 + 0.1 * 8 + 0.1 * 0.1 * 90 = 3.7 ns
So, average read (access) time = Fraction of Instruction Fetch * Average Instruction fetch time + Fraction of Data Fetch * Average Data Fetch Time = 0.6×5.4+0.4×3.7 = 4.72ns
Option (A) is correct.
Ans .
A
- Explanation :
x == ( y * q + r ) x= product, y= multiplicand, q = quotient , r = remainder
- For loop to be terminated, the quotient has to be 0, so only options C and D are left
- If q=0 -> r=x should apply
Ans .
C
- Explanation :
Extended transition function describes what happens when we start in any state and follow any sequence of inputs. Since this is an epsilon NFA so we have to consider the epsilon moves also and see which states we can reach after the input string is over. The starting state is q2, from q2 transition with input a is dead so we have to look for epsilon transition. With epsilon transition we reach to q0, at q0 we have a transition with input symbol a so we reach to state q1. From q1 we can take transition with symbol b and reach state q3 but from q3 we have no further transition with symbol a as input so we have to take another transition from state q1 that is the epsilon transition which goes to state q2. From q2 we reach to state q0 and read input b and then read input a and reach state q1. So q1 is one of the state of extended transition function. From q1 we can reach q2 with epsilon as input (mans with no input) and from q2 we can reach q0 with epsilon move so state q2 and q0 are also part of extended transition function. So state q1, q2, q0.
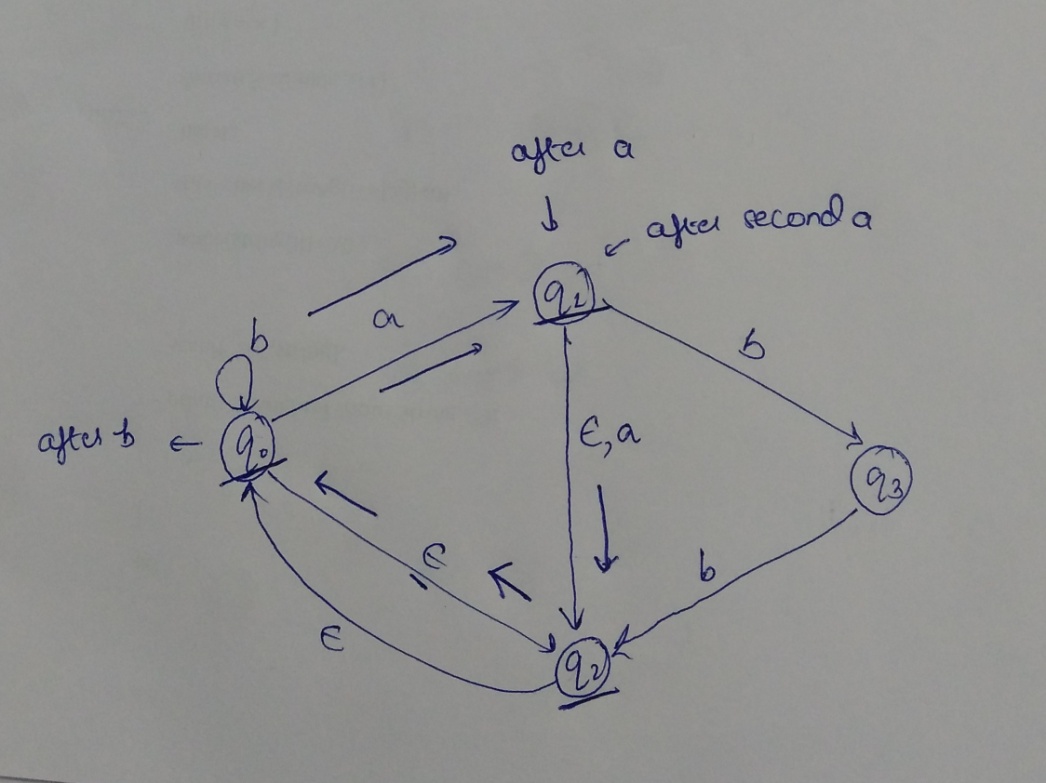
Ans .
C
- Explanation :
We know for left recursion : A -> Aα/β After removing left recursion it can be written as A->βA’ A’->αA’/ε Thus for : E->E- T/T α= -T , β= T . thus new production after removing left recursion is E->TE’ and E’->- TE’/ ε T->FT’ and T’->+FT’/ ε F->(E)/id .
Ans .
A
- Explanation :
- Access time of L1 = 1
- Access Time of L2=8
- miss penalty L1 cache (2*L2) = 18*2 = 2*a
- miss penalty L2 cache say a = 18
- AMAT (average memory access time) =2
Ans .
A
- Explanation :

Ans .
D
- Explanation :
Propagation delay = link length/ signal speed = (10^7)/(2*10^8 )sec = 5 =.005 sec =50 msec Transmission delay = data length/signal bandwith = 50000*8/10^6 sec =.04 sec =400 msec
Ans .
A
- Explanation :
In an RSA cryptosystem, for public key: GCD( ϕ(n) , e) = 1 And, for private key: (e * d) mod ϕ(n) = 1 Where, ϕ(n) = (p -1)*(q - 1) = (13 - 1)(17 - 1) =12*16 = 192 Such that 1 < e, d < ϕ(n) Therefore, the private key is: (35 * d) mod ϕ(n) = 1 d = 11