GATE-CS-2015 (Set 3)
Ans .
B
- Explanation :
In ROAD to URDG transformation, every character is replaced by next third character in alphabetic sequence. (R by U, O by R, A by D and D by G) Applying same, SWAN becomes VZDQ
Ans .
C
- Explanation :
Refer use of the here.
Ans .
B
- Explanation :
Refer http://dictionary.reference.com/browse/extraneous
Ans .
A
- Explanation :
Pediatrician is a doctor for children. Gynaecologist is a doctor for Females.
Ans .
B
- Explanation :
f(x) = 2x+33
Ans .
C
- Explanation :
Conquering Persia was the reason for Alexander turning his attention towards India
Ans .
B
- Explanation :
Six selected members are P, Q, R, S, T and U Portfolios are Home, Power, Defence, Telecom, and Finance. U does not want any portfolio if S gets one of the five. R wants either Home or Finance or no portfolio. Q says that if S gets either Power of telecom, then she must get the other one. T insists on a portfolio if P gets one Which is the valid distribution of portfolios? A) P-Home, Q-Power, R-Defence, S-Telecom, T-Finance Not valid as R doesn't get home or finance here R-Home, S-Power, P-Defence, Q-Telecom, T-Finance Is valid and satisfies all conditions. C) P-Home, Q-Power, T-Defence, S-Telecom, U-Finance Not valid as U is not satisfied. Condition for U is, S should not get any portfolio. D) Q-Home, U-Power, T-Defence, R-Telecom, P-Finance Like A, not valid as R doesn't get home or finance here
Ans .
A.
- Explanation :
3rd course of action is not correct. Banning water supply can not solve the problem.
Ans .
B
- Explanation :
i) is incorrect "He was guilty of throwing away his wicket several times after working hard to lay a strong foundation. " (ii) is correct, "His critics pointed out that until he addressed this problem, success at the highest level will continue to elude him." (iii) is correct, "His critics pointed out that until he addressed this problem, success at the highest level will continue to elude him." (iv) is incorrect "Temperament is also required"
Ans .
D
- Explanation :
1 - (1 - m) (1 - p) (1 - c) = 0.75 -------(1) (1 - m)pc + (1 - p)mc + (1 - c)mp + mpc = 0.5 -------(2) (1 - m)pc + (1 - p)mc + (1 - c)mp = 0.4 -------(3) From last 2 equations, we can derive mpc = 0.1 After simplifying equation 1, we get. p + c + m - (mp + mc + pc) + mpc = 0.75 p + c + m - (mp + mc + pc) = 0.65 -------(4) After simplifying equation 3, we get pc + mc + mp - 3mpc = 0.4 Putting value of mpc, we get pc + mc + mp = 0.7 After putting above value in equation 4, we get p + c + m - 0.7 = 0.65 p + c + m = 1.35 = 27/20
Ans .
B
- Explanation :
The size of ready queue doesn't depend on number of processes. A single processor system may have a large number of processes waiting in ready queue.
Ans .
B
- Explanation :
S2 is true, as X' + Y' = Y' + X' S1 is false. Let P = 1, Q = 1, R = 0, we get different results (P # Q) # R = (P' + Q')' + R' = (0 + 0)' + 1 = 1 + 1 = 1 P # (Q # R) = P' + (Q' + R')' = 0 + (0 + 1)' = 0 + 0 = 0
Ans .
A
- Explanation :
When the ALL condition is followed by a list, the optimizer expands the initial condition to all elements of the list and strings them together with AND operators. When the ANY condition is followed by a list, the optimizer expands the initial condition to all elements of the list and strings them together with OR operators, as shown below. Source: http://oracle-base.com/articles/misc/all-any-some-comparison-conditions-in-sql.php
Ans .
C
f(x) = 1 - |x|
f(0) = 1
f(1) = f(-1) = 0
f(0.5) = f(-0.5) = 0.5
The maximum is attained at x = 0, and the maximum value is 1.
Ans .
D
Ans .
A
Ans .
D
Ans .
B
- Explanation :
Length and checksum can be modified when IP fragmentation happens. Time To Live is reduced by every router on the route to destination. Only Source Address is what IP address can not change SO B is the answer.
Ans .
B
- Explanation :
The time taken by search, insert and delete on a BST is always proportional to height of BST. Height may become O(n) in worst case.
Ans .
C
- Explanation :
In Clustered Index, data blocks are stored in a way to match the index. Therefore, only one clustered index can be created on a given database table. Refer https://msdn.microsoft.com/en-IN/library/ms190457.aspx for more details.
Ans .
B
- Explanation :
Total faults detected = 159 Real faults detected among all detected faults = 159 - 75 = 84 Since probability distribution is same, total number of real faults is (100/75)*84 = 112 Undetected real faults = 112- 84 = 28
Ans .
c
- Explanation :
Refer http://dictionary.reference.com/browse/extraneous
Ans .
B
- Explanation :
Insert(Root,key)
{
if(Root is NULL)
Create a Node with value as key and return
Else if(Root.key <= key)
Insert(Root.left,key)
Else
Insert(Root.right,key)
}
Ans .
B
- Explanation :
Block Size = 16 bytes
Block Offset = 4
No. of sets or cache lines = 212
Number of index bits = 12
Size of main memory = 220
Number of tag bits = 20 - 12 - 4 = 4
Let us consider the hex address E201F
Tag lines = First 4 bits = E (in hex)
Cache lines = Next 12 bits = 201 (In Hex)
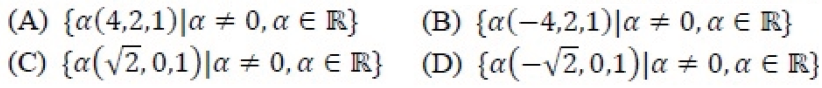
Ans .
B
- Explanation :
And let the given matrix be A (square matrix of order 3 x3) The characteristic equation for this is : AX = zX ( X is the required eigenvector ) AX - zX = 0 [ A - z I ] [X] = 0 ( I is an identity matrix of order 3 ) put z = 1 ( because one of the eigenvalue is 1 ) [ A - 1 I ] [X] = 0 The resultant matrix is : [ 0 -1 2 ] [x1] [0] | 0 0 0 ] |x2] =|0| [ 1 2 0 ] |x3] [0] Multiplying thr above matrices and getting the equations as: -x2 + 2x3 = 0 ----------------(1) x1 + 2x2 = 0-----------------(2) now let x1 = k, then x2 and x3 will be -k/2 and -k/4 respectively. hence eigenvector X = { (k , -k/2, -k/4) } where k != 0 put k = -4c ( c is also a constant, not equal to zero ), we get X = { ( -4c, 2c, 1c ) }, i.e. { c ( -4, 2, 1 ) } Hence option B.
Ans .
C
- Explanation :
SLR parser is a type of LR parser with small parse tables and a relatively simple parser generator algorithm. Canonical LR parser or LR(1) parser is an LR(k) parser for k=1, i.e. with a single lookahead terminal. It can handle all deterministic context-free languages. LALR parser or Look-Ahead LR parser is a simplified version of a canonical LR parser
Ans .
A
- Explanation :
oad factor = (no. of elements) / (no. of table slots) = 2000/25 = 80
Ans .
B
- Explanation :
The given regular expression matches with all strings that contain 0011. The complement should match with all strings except the strings with 0011 as substring. Following are some interesting facts/observations from this question. 1) Complement of a regular language is also regular. 2) Since complement is regular, it is always possible to make a DFA for complement. 3) A DFA that accepts its complement is obtained from the above DFA by changing all non-accepting states to accepting states and vice versa as done in this question. Below is DFA for the complement. We can get below DFA by first drawing DFA of regular language for strings with substring as 0011. After drawing DFA, we can invert all states (single circle to double circle and vice versa)
Ans .
B
- Explanation :
89 / \ 19 50 / \ / \ 17 12 15 2 / \ / \ / \ 5 7 11 6 9 100 Minimum number of swaps required to convert above tree to Max heap is 3. Below are 3 swap operations. Swap 100 with 15 Swap 100 with 50 Swap 100 with 89 100 / \ 19 89 / \ / \ 17 12 50 5 / \ / \ / \ 7 11 6 9 2 15
Ans .
A
- Explanation :
The value of function point metric = UPF * VAF
Here,
UPF: Unadjusted Function Point (UFP) count
VAF: Value Adjustment Factor
UPF = 4*30 + 60*5 + 23*4 + 8*10 + 7*2 = 606
VAF = (TDI * 0.01) + 0.65
Here TDI is Total Degree of Influence
TDI = 3*4 + 0*4 + 4*6 = 36
VAF = (TDI * 0.01) + 0.65
= 36*0.01 + 0.65
= 0.36 + 0.65 = 1.01
FP = UPF * VAF
= 1.01 * 606
= 612.06
Ans .
B
- Explanation :
In TCP, as sender and receiver can send segments at the same time, It is FULL-DUPLEX. TCP has options for selective acknowledgement. With selective acknowledgments (SACKs), the data receiver can inform the sender about all segments that have arrived successfully, so the sender need retransmit only the segments that have actually been lost. As each BYTE is counted in TCP segment, and Sequence number of First BYTE is kept into header, TCP is BYTE stream protocol. So, only 1st is correct and other incorrect. Reference : https://tools.ietf.org/html/rfc2018 This solution is contributed by sandeep pandey.
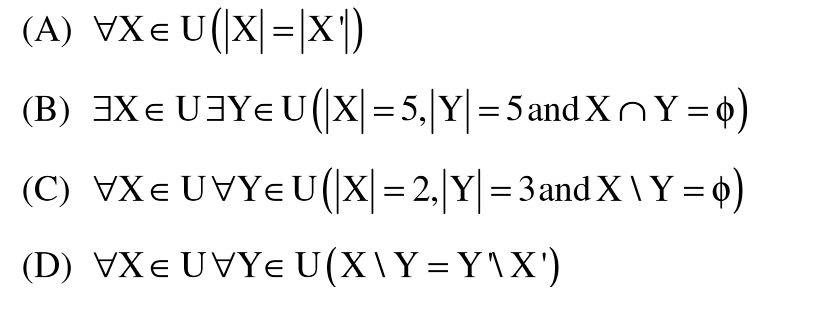
Ans .
D
- Explanation :
A is false, Take an example like X = {1, 2, 3, 4}, X' = {5, 6}, |X| is not same as |X'|. B is false, as any two subsets of size 5 of U would definitely have some common elements. C is false, Take an example like X = {1, 2} Y = {3, 4, 5}, X\Y = {1, 2}.
Ans .
B
- Explanation :
“The result of the toss is head if and only if I am telling the truth.”
If the person is of Type 1 who always tell truth, then result must be head.
If the person is of Type 2 who always tell lie, then result must be head.
Negation of a sentence of the form "X is true if and only if Y is true" is "Either X is true and Y is false, or X is false and Y is true."
Refer: http://math.stackexchange.com/questions/10435/negation-of-if-and-only-if
Which means "Either toss is head and I am not telling truth, or toss is tail
and I am telling truth".
Since the person always lie, it is "Either toss is head and I am not telling truth"
Ans .
A
- Explanation :
This can be proved using Handshaking Lemma. Refer below post to see complete proof. Handshaking Lemma and Interesting Tree Properties
Ans .
A
- Explanation :
Now ptr is actually pointing to the first element of array p. ptr++ will make it point to the next element of array p. Its value will then change to 2004. One of the Rule of Pointer Arithmetic is that When you subtract two pointers, as long as they point into the same array, the result is the number of elements separating them. ptr is pointing to the second element and p is pointing to the first element so ptr-p will be equal to 1(Excluding the element to which ptr is pointing). Now ptr = 2004 -----> *(2004) = 1012 ----> *(1012) ----> 40. Therefore, final answer is 140. This solution is contributed by Pranjul Ahuja. .
.
Ans .
B
- Explanation :
ime complexity of merge sort is T(nLogn)
c*64Log64 is 30
c*64*6 is 30
c is 5/64
For time 6 minutes
5/64*nLogn = 6*60
nLogn = 72*64 = 512 * 9
n = 512.
Ans .
B
- Explanation :
Propagation time = (8000 * 1000)/ (4 * 10^6)
= 2 seconds
Total round trip propagation time = 4 seconds
Transmission time for one packet = (packet size) / (bandwidth)
= (10^7) / (500 * 10^6)
= 0.02 seconds
Total number of packets that can be transferred before an
acknowledgement comes back = 4 / 0.02 = 200
Maximum possible window size is 200.
In Go-Back-N, maximum sequence number should be one more than
window size.
So total 201 sequence numbers are needed. 201 different sequence
numbers can be represented using 8 bits.
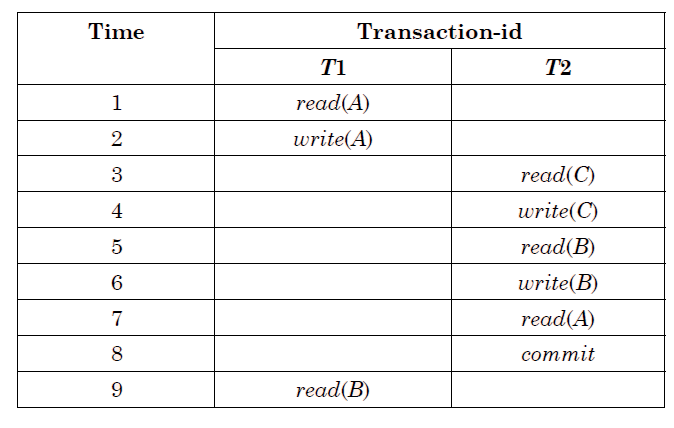
Ans .
B
- Explanation :
if transaction fails, atomicity requires effect of transaction to be undone. Durability states that once transaction commits, its change cannot be undone (without running another, compensating, transaction). Recoverable schedule: A schedules exactly where, for every set of transaction Ti and Tj. If Tj reads a data items previously written by Ti, then the commit operation of Ti precedes the commit operation of Tj. Aborting involves undoing the operations and redoing them since by the time stamp it is aborted. Option (A): T2 must be aborted and then both T1 and T2 must be re-started to ensure transaction atomicity. It is incorrect because it says abort transaction T2 and then redo all the operations. But there is no gaurantee that it will succeed this time as again T1 may be fail. Option(B): Schedule S is non-recoverable and cannot ensure transaction atomicity. Correct, it is by definition an irrecoverable schedule so now even if we start to undo the actions one by one(after t1 fails) in order to ensure transaction atomicity. Still we cannot undo a commited transaction. hence this schedule is irrecoverable by definition and also not atomic since it leaves the database in an inconsistent state. Simply dirty read so nonrecoverable. Option (C): Only T2 must be aborted and then re-started to ensure transaction atomicity. It is incorrect because it says abort only transaction T2 and then redo all the T2 operations. But this is dirty read problem as it is reading the data item A which is written by T1 and T1 is not committed. Again it will be the dirty read problem. So incorrect. Option (D): Schedule S is recoverable and can ensure transaction atomicity and nothing else needs to be done. Incorrect, it is clearly saying that schedule s is recoverable but it is irrecoverable because T2 read the data item A which is written by T1 and T1 failed and rollback, at the rollback T1 start undo all operations and modified the value of A with previous value but T2 is already committed so T2 can't change the read value of A which was earlier taken from T1.
Ans .
D
- Explanation :
In C, 2D arrays are stored in row major order. Therefore, S2 is correct, but S3 is not correct.
Ans .
D
- Explanation :
The given grammar is ambiguous as there are two possible leftmost derivations for string "c". First Leftmost Derivation S ? F F ? c Second Leftmost Derivation S ? H H ? c
An Ambiguous grammar can neither be LL(1) nor LR(1)
Ans .
B
- Explanation :
We can build a push down automata for L1 and L3, but can not build push down automata for L@. Note that a PDA can uses a stack. L1 and L3 can be identified using a single stack, but L2 can't be.
Ans .
B
- Explanation :
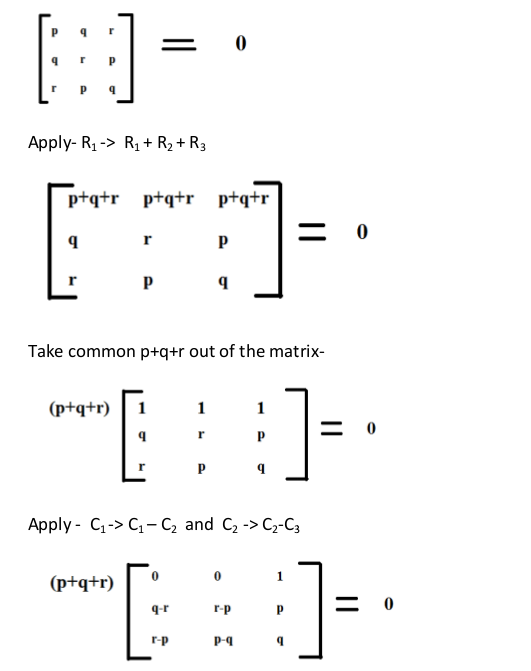
Ans .
B
- Explanation :
Turnaround time is the total time taken between the submission of a program/process/thread/task (Linux) for execution and the return of the complete output to the customer/user. Turnaround Time = Completion Time - Arrival Time. FCFS = First Come First Serve (A, B, C, D) SJF = Non-preemptive Shortest Job First (A, B, D, C) SRT = Shortest Remaining Time (A(3), B(1), C(4), D(2), B(5)) RR = Round Robin with Quantum value 2 (A(2), B(2), A(1),C(2),B(2),D(2),C(2),B(2) Pr Arr.Time P.Time FCFS SJF SRT RR A 0 3 3-0=3 3-0=3 3-0=3 5-0=5 B 1 6 9-1=8 9-1=8 15-1=14 15-1=14 C 4 4 13-4=9 15-4=11 8-4=4 13-4=9 D 6 2 15-6=9 11-6=5 10-6=4 11-6=5 Average 7.25 6.75 6.25 8.25 Shortest Remaining Time produces minimum average turn-around time.
Ans .
C
- Explanation :
3 + 4x = 3 + 8y where 0 <= y <= 7
and x >= 5 (because the number represented in base x is 34)
x = 2y and 0 <= y <= 7
The following are possible solutions
y = 3, 4, 5, 6, 7
x = 6, 8, 10, 12, 14
Ans .
B
- Explanation :
Sender host transmits first packet to switch, the transmission time is 5000/107 which is 500 microseconds. After 500 microseconds, the second packet is transmitted. The first packet reaches destination in 500 + 35 + 20 + 20 + 500 = 1075 microseconds. While the first packet is traveling to destination, the second packet starts its journey after 500 microseconds and rest of the time taken by second packet overlaps with first packet. So overall time is 1075 + 500 = 1575.
Ans .
B
- Explanation :
From the above table, P(Y=0 nX3=0) = 3/8 And P (X3=0) = 1/2 P (Y=0 | X3=0) = P(Y=0 nX3=0) / P(X3=0) = (3/8) / (1/2) = 3/4 = 0.75 This solution is contributed by Anil Saikrishna Devarasetty . Another Solution : It is given X3 = 0. Y can only be 0 when X1 X2 is 0. X1 X2 become 0 for X1 = 1, X2 = 0, X1 = X2 = 0 and X1 = 0, X = 1 So the probability is = 0.5*0.5*3 = 0.75
Ans .
B
- Explanation :
The last or fourth octet of network address is 144 144 in binary is 10010000. The first three bits of this octal are fixed as 100, the remaining bits can get maximum value as 11111. So the maximum possible last octal IP address is 10011111 which is 159. The question seems to by asking about host address. The address with all 1s in host part is broadcast address and can't be assigned to a host. So the maximum possible last octal in a host IP is 10011110 which is 158. The maximum possible network address that can be assigned is 200.10.11.158/31 which has last octet as 158.
Ans .
B
- Explanation :
get(6) [25 Calls] / \ [17 Calls] get(5) get(3) [7 Calls] / \ get(4) get(2)[5 Calls] / \ [7 Calls] get(3) get(1)[3 Calls] / \ get(2) get(0) / \ [3 Calls]get(1) get(-1) / \ get(0) get(-2)
Ans .
B
- Explanation :
Since there are 100 vertices, there must be 99 edges in Minimum Spanning Tree (MST). When weight of every edge is increased by 5, the increment in weight of MST is = 99 * 5 = 495 So new weight of MST is 500 + 495 which is 995
Ans .
B
- Explanation :
((p, q), (r, s)) ? R if and only if p–s = q–r (p, q) is not related to (p, q) as p-q is not same as q-p. The relation is symmetric because if p–s = q–r, then s-q = s-p.
Ans .
B
- Explanation :
Red,Blue and Green together make total three prime implicant. As we know "A prime implicant of a function is an implicant that cannot be covered by a more general (more reduced - meaning with fewer literals) implicant. (Wikipedia)" we've to see only prime implicants . We can make group of four 1's as in the figure(green group) , a group of two 1's in blue and red .As we can't reduce it further so this is minimal representation of problem and hence total number of prime implicant =3. So answer (B) part.
Ans .
B
- Explanation :
The value of sine function varies from -1 to 1.
For sin = -1 or any other negative value, I becomes false.
For sin = 1 or any other negative value, II becomes false
Ans .
B
- Explanation :
After drawing K map of F = P` + QR ,we can find out S2 and S3 are TRUE
Ans .
B
- Explanation :
Therefore the correct option is B.
Ans .
B
- Explanation :
Let m be the order of B+ tree m(8)+(m-1)12 <= 1024
[Note that record pointer is not needed in non-leaf nodes]
m <= 51
Since maximum order is 51, maximum number of keys is 50. Let m be the order of B+ tree
m(8)+(m-1)12 <= 1024
[Note that record pointer is not needed in non-leaf nodes]
m <= 51
Since maximum order is 51, maximum number of keys is 50.
Ans .
B
- Explanation :
S1: There is an anti-dependence between instructions I2 and I5. False, I2 and I5 don't form any write after read situation. They both write R7. S2: There is an anti-dependence between instructions I2 and I4. True, I2 reads R3 and I4 writes it. S3: Within an instruction pipeline an anti-dependence always creates one or more stalls. Anti-dependency can be removed by renaming variables. See following example. 1. B = 3 2. A = B + 1 3. B = 7 Renaming of variables could remove the dependency. 1. B = 3 N. B2 = B 2. A = B2 + 1 3. B = 7
Ans .
B
- Explanation :
For i = 0, the value of i+k becomes -1, default block is executed, count = 1. For i = 1, the value of i+k becomes 0, default block is executed, count = 2. For i = 2, the value of i+k becomes 1, all blocks are executed as there is no break, count = 5 For i = 3, the value of i+k becomes 2, three blocks after case 1: are executed, count = 8 For i = 4, the value of i+k becomes 3, two blocks are executed, count = 10
Ans .
B
- Explanation :
For i = 0, z = 1 mod 8 = 1, since c[0] = 1, z = 1*2 mod 8 = 2.
For i = 1, z = 2*2 mod 8 = 1, since c[1] = 0, z remains 4.
For i = 2, z = 16 mod 8 = 0
Ans .
C
Ans .
D
- Explanation :
S1 | X | Y | | | X | Y | X | Y | | | X | Y | S2 | | X | Y | X | Y | | | X | Y | X | Y | | S3 | | | X | Y | | | | | X | Y | | | We can interleave instructions like the above pattern. Latency between X and Y is 1. Latency between fist and second X is 5. The pattern repeats after that. So, MAL is (1 + 5)/2;
Ans .
D
- Explanation :
If Ist is followed, then hold and wait will never happen. II, III and IV are similar. If any of these is followed, cyclic wait will not be possible
63
Ans .
A
- Explanation :
x += f1() + f2() + f3() + f2();
x = x + f1() + f2() + f3() + f2();
f1() returns 26
f2() returns 51
f3() returns 100
second call to f2() returns 52
[Note x is static in f2()]
x = 1 + 26 + 51 + 100 + 52 = 230
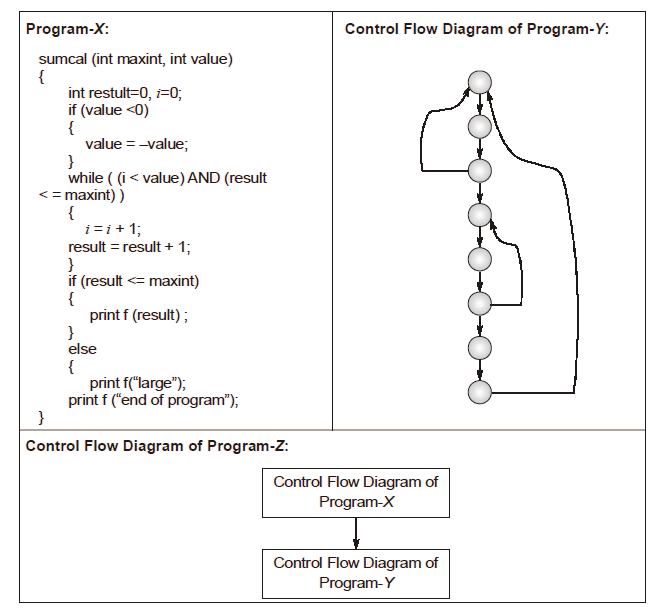
Ans .
A
- Explanation :
The cyclomatic complexity of a structured program[a] is defined with reference to the control flow graph of the program, a directed graph containing the basic blocks of the program, with an edge between two basic blocks if control may pass from the first to the second. The complexity M is then defined as.
M = E - N + 2P,
where
E = the number of edges of the graph.
N = the number of nodes of the graph.
P = the number of connected components.
Source: http://en.wikipedia.org/wiki/Cyclomatic_complexity
For first program X, E = 11, N = 9, P = 1, So M = 11-9+2*1 = 4
For second program Y, E = 10, N = 8, p = 1, So M = 10-8+2*1 = 4
For Third program X, E = 22, N = 17, p = 1, So M = 22-17+2*1 = 7
]