Ans .
C
- Explanation :
If the Primal problem is feasible, but unbounded in the direction of optimisation, then the dual has no feasible solution. Otherwise, if the Primal problem has an optimal solution, then the dual has also an optimal solution
Ans .
D
- Explanation :
All the three conditions are necessary for local maxima
Ans .
B
- Explanation :
draw lines for two inequalities nothing is common in shaded area so infeasible solution
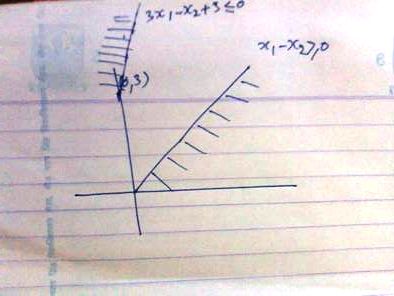
Ans .
B
- Explanation :
Predicate (decision) nodes are those nodes which has out degree atleast 2. Region =13-10+2 = 5 [i.e. edges - vertex + (p+1)] since p= 1] predicate nodes(P) region = P+1 = 5 P = 4
Ans .
A
- Explanation :
UFP is Unadjusted Function Point CAF is Complixity Adjustment Factor Function Point FP = UFP*CAF
Ans .
B
- Explanation :a. Data coupling ii. Dependency between modules is based on the fact they communicate by only passing of data
b. Stamp coupling iii. When complete data structure is passed from one module to another
c. Common coupling i. Module A and Module B have shared data
d.Content coupling iv. When the control is passed from one module to the middle of another
Ans .
B
- Explanation :
Software Configuration Management Process has following primary objective: 1. to identify all items that collectively define the software configuration 2. to manage changes to one or more of these items 3. to facilitate the construction of different versions of an application 4. to ensure that software quality is maintained as the configuration evolves over time
Ans .
B
- Explanation :
both are black box testing techniques as we only test at boundaries and at certain points they do not explore combinations of input circumstances for more detail refer http://reqtest.se/testing-sv/what-is-boundary-value-analysis-and-equivalence-partitioning/
Ans .
D
- Explanation :
Rest are myths (programmer myths and management's myths)
Ans .
A
- Explanation :
1.state diagram is a type of diagram used in computer science and related fields to describe the behavior of systems. State diagrams require that the system described is composed of a finite number of states;
2.In software engineering, a class diagram in the Unified Modeling Language (UML) is a type of static structure diagram that describes the structure of a system by showing the system's classes, their attributes, operations (or methods), and the relationships among objects.
3.An InstanceDiagram is a part of the UnifiedModelingLanguage that one does not see mentioned too often. The basic idea is to make a static snap shot of instances (not classes) in your system or subsystem. Make it show exactly who points to whom.
4.Object diagrams are derived from class diagrams so object diagrams are dependent upon class diagrams.Object diagrams represent an instance of a class diagram. The basic concepts are similar for class diagrams and object diagrams. Object diagrams also represent the static view of a system but this static view is a snapshot of the system at a particular moment.Object diagrams are used to render a set of objects and their relationships as an instance.
Ans .
A
- Explanation :
Keep methods coherent ---> Performs a single function or a group of a closely related functions Keep methods small----> Breaking a method into smaller parts Keep methods consistent--->Maintain parallel structure when possible Provide uniform coverage--->Write a method to get the last element of a list
Ans .
C
- Explanation :
SOAP is an acronym for Simple Object Access Protocol. It is an XML-based messaging protocol for exchanging information among computers. SOAP is an application of the XML specification.
Although SOAP can be used in a variety of messaging systems and can be delivered via a variety of transport protocols, the initial focus of SOAP is remote procedure calls(RPC) transported via HTTP.
Ans .
C
- Explanation :
Any prefix can be used, but the prefix "xsl" is used most frequently with XSLT. The prefix and the element name are separated by a colon (:). In other words, "xsl:…" is notated to separate transformation commands and output data. Since the XSLT stylesheet is an XML document, a root element is required.
Ans .
B
- Explanation :
Dynamic loading is a mechanism by which a computer program can, at run time, load a library (or other binary) into memory, retrieve the addresses of functions and variables contained in the library, execute those functions or access those variables, and unload the library from memory. In OOPs Dynamic Binding refers to linking a procedure call to the code that will be executed only at run time. The code associated with the procedure in not known until the program is executed, which is also known as late binding.
Ans .
C
- Explanation :
Ad-hoc polymorphism allows functions with the same name act differently for each type In programming languages, ad hoc polymorphism is a kind of polymorphism in which polymorphic functions can be applied to arguments of different types, because a polymorphic function can denote a number of distinct and potentially heterogeneous implementations depending on the type of argument(s) to which it is applied.
Ans .
A
- Explanation :Since JAVA is Object Oriented language
Ans .
A
- Explanation :

Ans .
Correct Answer is none
- Explanation :
Ans .
D
- Explanation :
Important advantage of using new and delete operators in C++ is we can allocate and deallocate memory at any time.
Ans .
A
- Explanation :
a.Forward movement ---->iv. Choose sub goal with possible unifier.
b. Unification ---->i. Variable can be done with a constant, another variable or a function
c. Deep backtracking ---->ii. The entire conjunctive goal is executed.
d. Shallow backtracking ---->iii. Previous sub goal to find alternative solutions.
Ans .
A
- Explanation :
By Expanding both the Grammars you can verify the answers.
Ans .
D
- Explanation :
T flip flop toggles the state if input T is 1, and does not change state if input T is 0. T flip flop is a clocked (synchronous or edge-triggered) flip flop. Edge triggered flip flops can only change its values at the edge of a clock, in absence of edge does not change its state, remains same. In given circuit, clock symbol is showing that it is positive edge triggering (low to high change). Note that there are mainly four different types of clock-triggering methods. Now, we need to find out Q0Q1 after 4 clock cycles. Initial: 00 States Q0 and Q1 are zero Clock 1: 11 State Q0 changed to 1 because input T is 1 and previous state was 0 and State Q1 changed to 1 because input T is 1 and previous state was 0. Clock 2: 01 State Q0 changed to 0 because input T is 1 and previous state was 1 and State Q1 remains same because clk value is 0. Clock 3: 10 State Q0 changed to 1 because input T is 1 and previous state was 0 and State Q1 changed to 0 because input T is 1 and previous state was 1. Clock 4: 00 State Q0 changed to 0 because input T is 1 and previous state was 1 and State Q1 remains same because clk value is 0.
Ans .
D
- Explanation :
A process in which the speaker implies and a listener infers. Simply Pragmatics studies language that is not directly spoken. The speaker hints at or suggests a meaning , and the listener assume the correct intention. Pragmatics study how words can be interpreted in different ways based on the situation.
Ans .
B
- Explanation :
The objective of unification procedure is to discover at least one substitution that causes two literals to match
Ans .
C
- Explanation :
h* underestimates h . Rule is an algorithm gives an optimal solution if h* never overestimates h (admissible heuristics so b is out underestimating h means algorithm is looking for better solution which may be found if it is there(optimal solution)
Ans .
C
- Explanation :
Most of the search strategies either reason forward of backward however, often a mixture o the two directions is appropriate. Such mixed strategy would make it possible to solve the major parts of problem first and solve the smaller problems the arise when combining them together. Such a technique is called "Means - Ends Analysis". Operator subgoaling is a computer problem solving method in which the inability of the computer to take the desire next step at any point in the problem solving process leads to a subtotal of making step feasible Steps: Computing the current state s1 to a goal state s2 and computing their difference D12. Satisfy the preconditions for some recommended operator op is selected, then to reduce the difference D12. The operator OP is applied if possible. If not the current state is solved a goal is created and means- ends analysis is applied recursively to reduce the sub goal.
Ans .
B
- Explanation :
Alpha-Beta pruning is not actually a new algorithm, rather an optimization technique for minimax algorithm. It reduces the computation time by a huge factor. This allows us to search much faster and even go into deeper levels in the game tree. It cuts off branches in the game tree which need not be searched because there already exists a better move available. It is called Alpha-Beta pruning because it passes 2 extra parameters in the minimax function, namely alpha and beta.
Ans .
D
- Explanation :
The fuzzy intersection of two fuzzy sets A and B on universe of discourse X: μA∩B(x) = min [μA(x), μB(x)] , where x belongs to X The minimum of 0.2 and 0.1 will be 0.1, The second value is min(0.5,0.5)=0.5 The third value is min(0.6,0.2)=0.2 The fourth value is min(0.1,0.7)=0.1 The last value is min(0.9,0.8)=0.8 So the answer is option D.
Ans .
C
- Explanation :
when h(A)=1 that is height or membership function is 1 fuzzy set become normal or crisp set
choice A means element does not belong to set so neither a fuzzy nor normal
choice B is not defined (noon-meaningful) and so is choice D both can not be same though so some misprint if it is >0 then it will be only fuzzy set and not normal
Ans .
D
- Explanation :
ans is D (some slight change as sigma should come only one time) weighted sum is calculated by multiplying inputs with their respective weights and then adding them all which can be shown as Σ wi . xi
Ans .
B
- Explanation :
Data compression ratio is defined as the ratio between the uncompressed size and compressed size Thus a representation that compresses a 10 MB file to 2 MB has a compression ratio of 10/2 = 5, often notated as an explicit ratio, 5:1 (read "five" to "one"), or as an implicit ratio, 5/1.
Note that this formulation applies equally for compression, where the uncompressed size is that of the original; and for decompression, where the uncompressed size is that of the reproduction.
Sometimes the space savings is given instead, which is defined as the reduction in size relative to the uncompressed size: Thus a representation that compresses a 10MB file to 2MB would yield a space savings of 1 - 2/10 = 0.8, often notated as a percentage, 80%.
Ans .
C
- Explanation :
The AES (Advanced Encryption Standard) cryptosystem allows variable key lengths of size 128 bits , 192 bits and 256 bits . 56 is used by DES.
Ans .
D
- Explanation :
As given polynomial is x3+1 =>1001 with this directly we can say option D because we add 3 digits more for the data and this satisfied only by option D But general solution could be 1001) 11001001000(1100011 1001 ---------------- 01011 1001 ---------------- 00100 0000 ---------------- 01000 1001 ---------------- 0001100 1001 ---------------- 01010 1001 ---------------- 0011 so the message transmitted is 11001001011 Option D
Ans .
C
- Explanation :
minimum number of comparison require to find minimum and maximum is: Approach is divide and conquer .... T(n) = T(floor(n/2)) + T(ceil(n/2)) + 2 T(2) = 1 // if two element then compare both and return max and min T(1) = 0 // if one element then return both max and min same If n is a power of 2, then we can write T(n) as: T(n) = 2T(n/2) + 2 After solving above recursion, we get T(n) = 3/2n -2 Thus, the approach does 3/2n−2 comparisons if n is a power of 2. And it does more than 3/2n−2 comparisons if n is not a power of 2.
Ans .
B
- Explanation :
The efficient algorithm to multiply the two matrices has the time complexity O(n2.81) using Strassen’s algorithm.
Ans .
B
- Explanation :
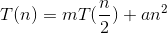 Now according to Master Theorem a=m , b=2 and f(n)=an2
nlog m > f(n) for all m>4 [Using case-1: Master Theorem]
so solution is O(nlg m)
Ans : B
Note :
Now according to Master Theorem a=m , b=2 and f(n)=an2
nlog m > f(n) for all m>4 [Using case-1: Master Theorem]
so solution is O(nlg m)
Ans : B
Note : 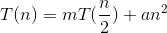 inplace of
inplace of 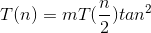
Ans .
C
- Explanation :
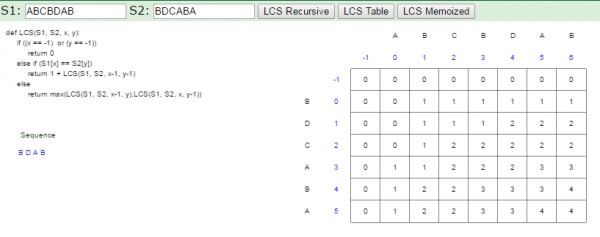
4 is ans i.e. BDAB , BCAB , BCBA .
Ans .
D
- Explanation :
Best and Avg. case= O(n+m) worst case= O(n^2)
Ans .
D
- Explanation :
Clique- A clique is a subset of vertices of a graph such that every two distinct vertices are adjacent( Every two vertices adjacent means a complete subgraph). Minimal Vertex Cover- A minimal vertex cover of a graph is set of minimum vertices such that each edge of the graph is incident to at least one vertex of set. Ans - Maximal , Minimal
Ans .
B
- Explanation :
Let L be an infinite context-free language. Then there is some positive integer m such that, if S is a string of L of length at least m, then S = uvwxy (for some u, v, w, x, y) |vwx| <= m |vx| 1>= uviwxiy is a member of L for all nonnegative values of i. B is ans.
Ans .
C
- Explanation :
(A)S→aSB , B→bB ∣ λ From this grammar we can't able to generate any string because there is no terminal string present for S.hence we can eliminate this option. (B)S→aSB , B→bB ∣ b From this grammar we can't able to generate any string because there is no terminal string present for S.hence we can eliminate this option. (C)S→aSB ∣ b , B→b From this we can generate all required string (b,abb,aabbb.....). (D)S→aSb ∣ b From this we can generate all required string (b,abb,aabbb.....) but question asking for GNF and this grammar is not GNF. Hence,Option(C)S→aSB ∣ b , B→b is the correct choice.
Ans .
D
- Explanation :
Every context sensitive language is recursive
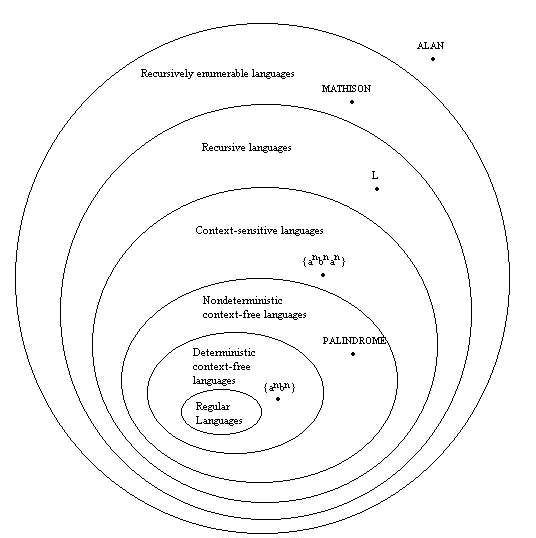
There is a recursive language that is not context sensitive
Ans .
C
- Explanation :
Uncompressed pixel = 800*600
each of 8 bit = 800*600 *8
Bit rate for transmitting = 800*600 *8 *40 =153600000 = 153.6Mbps
C is ans
Ans .
C
- Explanation :
200.200.200.200 belongs to class C [192-223].
Ans .
C
- Explanation :
Transport layer is the fourth layer in OSI Reference Model. It responds to service requests from Session layer and issues service requests to Network layer. Transport Layer is responsible for delivering messages between hosts. In Transport layer, data travels in the form of segments. Transport layer is responsible for creating an end to end connection between source IP and the destination IP. For establishing this end to end connection, Transport layer is using two major protocols TCP and UDP. TCP is connection oriented protocol where UDP is connection less protocol. So by using TCP we can create an end to end reliable connection between source and destination hosts. Transport layer is called host-to-host transport layer in TCP/IP model.
Ans .
B
- Explanation :

Ans .
C
- Explanation :
The start and stop bits are used in serial communication for synchronization i.e. to tell the receiver data is come after me ready to accept it , and data is finish after me.
Ans .
A
- Explanation :
Attenuation is a general term that refers to any reduction in the strength of a signal. Attenuation occurs with any type of signal, whether digital or analog. Sometimes called loss, attenuation is a natural consequence of signal transmission over long distances.
Distortion, in acoustics and electronics, any change in a signal that alters the basic waveform or the relationship between various frequency components; it is usually a degradation of the signal. Straight amplification or attenuation without alteration of the waveform is not usually considered to be distortion.
Noise is unwanted electrical or electromagnetic energy that degrades the quality of signals and data. Noise occurs in digital and analog systems, and can affect files and communications of all types, including text, programs, images, audio, and telemetry.
The decibel (dB) is a logarithmic unit used to express the ratio of two values of a physical quantity, often power or intensity. One of these values is often a standard reference value, in which case the decibel is used to express the level of the other value relative to this reference
Ans .
C
- Explanation :
a. Indexed Addressing iii. Addressing memory by giving a register plus a content offset. b. Direct Addressing iv. can only be used to access global variables whose address is known at compile time. c. Register Addressing i. is not used when an operand is moved from memory into a register or from a register to memory. d. Base-Indexed Addressing ii. Memory address is computed by adding up two registers plus an (optional) offset.
Ans .
D
- Explanation :
Design Criteria for Instruction Formats (How to outlast the current processor.)
1. Size of the Instructions balance instruction size vs. required capabilities, addressing, and inst. fetch times typically word length or multiple word lengths 1a. Consider the instruction fetch and instruction building required multiple word fetches require more time … leading to fewer instructions per second (average memory access time and I-cache make a difference)
2. Include enough bits to define “ALL” operations allow for future growth provide some “unassigned” opcodes
3. Determine any address range or size limitations a 32-bit address by byte accesses only 4GB of space the number of RISC registers defines the address field size (32 reg - 5 bits each)
Ans .
D
- Explanation :
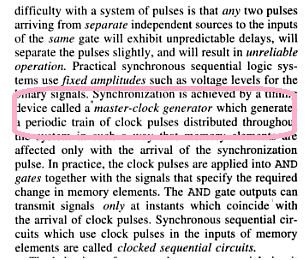
Ans .
D
- Explanation :
serial access memories are used where data naturally needs to flow in and out in serial form
Ans .
C
- Explanation :
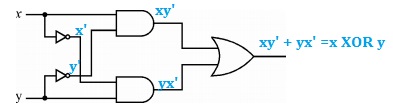
Ans .
B
- Explanation :
A trap is an exception in a user process. It's caused by division by zero or invalid memory access. It's also the usual way to invoke a kernel routine (a system call) because those run with a higher priority than user code. Handling is synchronous (so the user code is suspended and continues afterwards). In a sense they are "active" - most of the time, the code expects the trap to happen and relies on this fact.
An interrupt is something generated by the hardware (devices like the hard disk, graphics card, I/O ports, etc). These are asynchronous (i.e. they don't happen at predictable places in the user code) or "passive" since the interrupt handler has to wait for them to happen eventually.
Ans .
A
- Explanation :
First strong entity types are made to tables. So, we get two tables M and P. I assume R1 is 1:1 or 1:n as that would minimize the number of tables as asked in question. Now participation of M in R1 is total (indicated by double arrow) meaning every entity of M participate in R1. Since R1 is not having an attribute, we can simple add the primary key of P to the table M and add a foreign key reference to M. This handles R1 and we don't need an extra table. So, M becomes {M1, M2, M3, P1}. N here is a weak entity weakly related to P. So, we form a new table N, and includes the primary key of P (P1) as foreign key reference. Now (P1, N1) becomes the primary key of N. Thus we get 3 tables. M: {M1, M2, M3, P1} - M1 primary key, P1 references P P: {P1, P2} - P1 primary key N: {P1, N1, N2} - (P1, N1) primary key, P1 references P. So, answers is A.
Ans .
A
- Explanation :
πcustomer-name(σbalance >10000(Deposit)) we have to apply projection and use table Deposite. A is ans
Ans .
D
- Explanation :
1. Select S.stuid from student S where not exist (select * from student e where e course ='5' and e marks ≥ s marks) = false
Select S.stuid from student S where not exist (select * from student e where e course ='5' and e marks > s marks) = correct
Q.2. select S.stuid From student S where s.marks > any (select distinct marks from student S where s.course =5) = false
select S.stuid From student S where s.marks >All (select distinct marks from student S where s.course =5) = correct
Ans .
D
- Explanation :
Decomposition rule : If x->yz then x->y , x->z
Union rule : If x->y , x->z then x->yz
Composition rule: if x->y and z->w then xz-> yw
Pseudo transitivity rule : If x-> y and yw->z then xw-> z [ y replace by x].
X→Z
Ans .
D
- Explanation :
It is easy to observe that B-tree has secondary index Natural join is Relational Algebraic Operation Closure of set of attributes is related to Functional Dependency Non-procedural Query language is related to Domain Calculus Hence ans is D Primary index: A primary index is an index on a set of fields that includes the unique primary key for the field and is guaranteed not to contain duplicates. eg. Employee ID can be Example of it. Secondary index: A Secondary index is an index that is not a primary index and may have duplicates. eg. Employee name can be example of it. Because Employee name can have similar values.
Ans .
D
- Explanation :
option D is the ans as statement III is incorrect
First two statements are correct
A spaceball is a "six degrees of freedom" device. It allows full rotation in multiple directions, such as with a CAD model. a trackball, however is merely a standard mouse. rather than having the ball moved by the mouse platform, you manually actuate the ball. it just moves the cursor around. the libsball page has a nice image showing the spaceball's range and type of motion. a trackball just does XY axis motion.
Ans .
D
- Explanation :
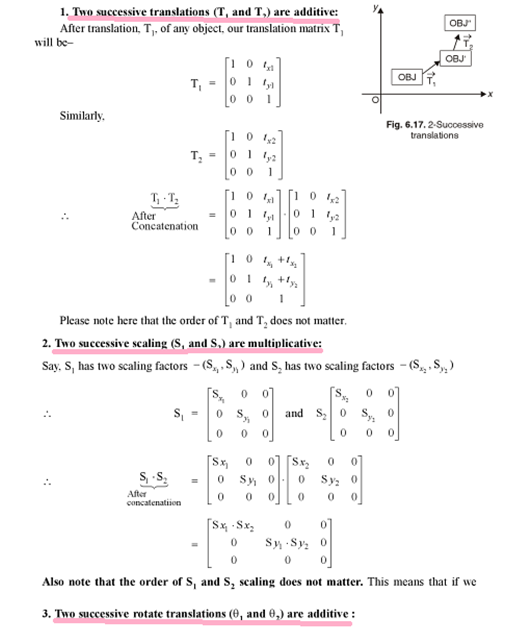
Ans .
D
- Explanation :
Put the value of x and y in the equation 3x+7y if 3x+7y >2 then it lies on the same side of origin else if 3x+7y > 2 it does not lies on the same side of origin
Ans .
C
- Explanation :
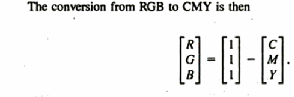
Ans .
D
- Explanation :
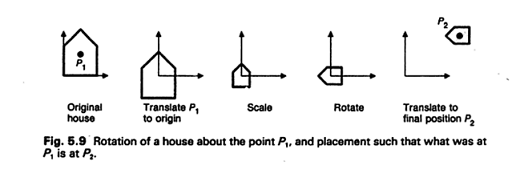
Ans .
C
- Explanation :

Ans .
B
- Explanation :
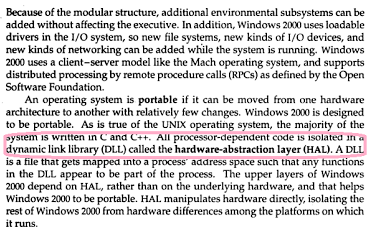
Ans .
D
- Explanation :
OLE is used to place a sound into a word document
Ans .
D
- Explanation :
Translation Look-aside Buffer (TLB) is an associative memory in which item to be searched is compared with all the keys simultaneously.When the associative memory is presented with an item, the item is compared with all keys simultaneously. If the item is found, the corresponding value field is returned.
Ans .
D
- Explanation :
Recovery through killing processes is the Crudest but simplest way to break a deadlock.
– Kill one of the processes in the deadlock cycle: the other processes get its resources.
– Choose process that can be rerun from the beginning
Ans .
A
- Explanation :

Ans .
A
- Explanation :
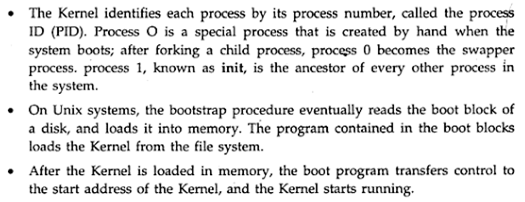
Ans .
D
- Explanation :
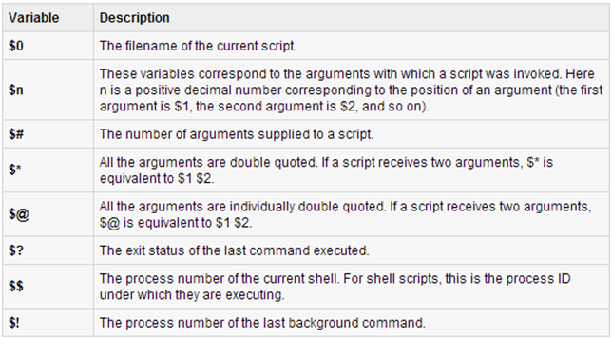
Ans .
B
- Explanation :