IOT Architectures: Protocols
Link layer protocols: These determine how data is sent over the networks physical layer or medium (fiber optic cable, coaxial cable and radio waves). Different hosts or devices on the same link or physical medium exchange data packets using link layer protocols. Link layer protocols determine how the packets are signaled and coded by the hardware device over the medium to which the host is attached.
Link layer protocols for IOT:
IEEE 802.3 (Ethernet): Collection of wired Ethernet standards for link layer.
802.11 (WiFi): Collection of wireless local area network communication standards.
802.16 (WiMax): Collection of wireless broadband standards.
802.15.4 : Collection of wireless personal area networks with low-cost and low speed.
2G/3G/4G: Mobile communication standards.
IOT Architectures: Network Protocols
It is responsible for sending data packets from source network to destination network.
This protocols are responsible for routing and host addressing.
Each packet contains source and destination address which are used to route them from source and destination across multiple networks.
IPv4: 32 bit address to identify devices using addressing schemes. IP handles connections but does not guarantee packet delivery.
IPv6: 128 bit addressing scheme.
6LoWPAN: IPv6 over Low power wireless personal area networks. Handles compression mechanisms for IPv6 packets over 802.15.4 based networks.
IOT Architectures: Transport Protocols
This protocols provides end to end message transfer capability independent of the underlying network. The message trasnfer capability can be set up on connections either using handshakes or without handshakes. Transport layer provides functions such as error control, flow control, segmentation and congestion control.
Transmission control protocol: Connection is established prior to sending of packets. IP protocol deals with sending packets, TCP ensures reliable transmission of packets in order. TCP provides error detection capability so that duplicate packets are detected and lost packets are retransmitted. Flow control means that sender sends at a rate at which the receiver does not get overwhelmed. Congestion control is the capability of TCP to avoid network congestion.
UDP: It ensures fast delivery by avoiding connection setup. Hence, useful for time sensitive applications. However, it cannot ensure reliable delivery, ordering of packets and duplicate elimination.
IOT Architectures: Transport Protocols
This protocols provides end to end message transfer capability independent of the underlying network. The message trasnfer capability can be set up on connections either using handshakes or without handshakes. Transport layer provides functions such as error control, flow control, segmentation and congestion control.
Transmission control protocol: Connection is established prior to sending of packets. IP protocol deals with sending packets, TCP ensures reliable transmission of packets in order. TCP provides error detection capability so that duplicate packets are detected and lost packets are retransmitted. Flow control means that sender sends at a rate at which the receiver does not get overwhelmed. Congestion control is the capability of TCP to avoid network congestion.
UDP: It ensures fast delivery by avoiding connection setup. Hence, useful for time sensitive applications. However, it cannot ensure reliable delivery, ordering of packets and duplicate elimination.
IOT Architectures: Application Protocols
These protocols define how the applications interface with the lower level protocols to send data over the network. The application data which is in the form of files is encoded by the application layer protocol and encapsulated in the transport layer protocols which provides connection or transaction oriented communication over the network. These protocols enable process to process connections using ports:
HTTP: The protocol uses response-request model for communication between client and server. The resources on the internet are requested by client through his browser (client). Web servers respond by providing the requested resources.
CoAP: Constrained Application protocol is for constrained environments and machine to machine applications. It uses UDP for packet transfer and hence is connectionless. It also relies on client server model.
Websocket: It allows simultaneous transmission and receiving of messages over a single socket. Websocket is based on TCP and allows sending and receiving of messages between client and server while keeping TCP connection open.
MQTT: Message Queue Telemetry Transport. The protocol usually runs over TCP/IP; however, any network protocol that provides ordered, lossless, bi-directional connections can support MQTT. It uses client server architecture where the client is an IOT device that connects to the server (MQTT broker) and publishes messages to topics on the server. The broker forwards messages to the clients who have subscribed to those topics.
XMPP: Extensible Messaging and Presence Protocol is a communication protocol for message-oriented middleware based on XML. It enables the near-real-time exchange of structured yet extensible data between any two or more network entities. The entities can be IOT devices or devices with a server or between two servers.
IOT Architectures: Project
Service specifications defines the services in the IOT system, service types, service inputs/output, service endpoints, service schedules, service productions and service effects.
Project Name: Home Watch
Tag Line: A system that sends you an alert for possible hazards
Proposal Intent: The intent behind this project is to investigate and learn about the IoT devices and sensors. The main reason for choosing the motion sensor is to study the pattern of occupancy of people at a room in a house and utilize this observation to track the possible hazards. The implementation of this project will help to make our home more secure. The PIR sensor detects the motion and sends an alert to the owner regarding the motion.
Project Purpose: The purpose of this project is to discover the use of different sensors and the Arduino board. The aim is to study the behavior of PIR sensor when a motion is detected and send this observation as an email notification. This can be used to make home safe and detect forgery. The project detects the presence of an intruder in a room and sends a signal to the Arduino. The Arduino then sends an email alert to the homeowner regarding the situation.
IOT Architectures: Domain Model Specification
The domain model describes the main concepts, entities, and objects in the domain.
The domain for the current project includes physical entities for rooms.
The devices in the system are Bread Board to which PIR and LED are attached.
Laptop/Desktop hosts the software such as Arduino IDE and Python code that sends an email alert to a homeowner. The homeowner uses an app to control the email notifications.
Domain Model Specification: The domain model specification of home watch system is as shown below:
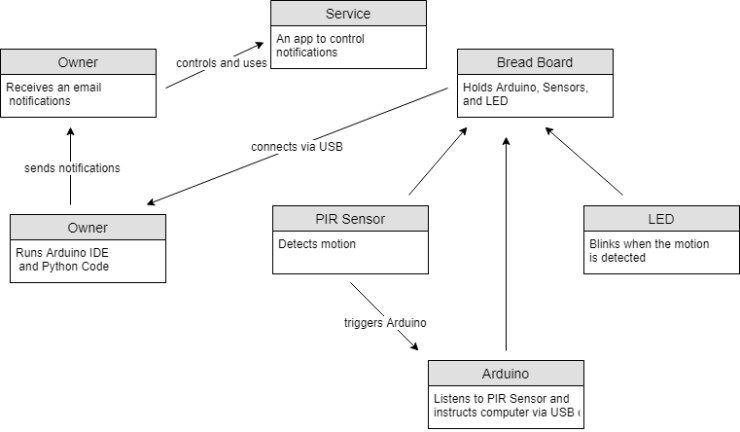
IOT Architectures: Service Specifications
The services provided by the application are:
The sensor reading is read from the PIR sensor.
The Arduino is triggered when motion is detected.
The laptop/computer hosts the python program that sends an email notification to the homeowner.
The owner uses an app to control the notifications.
Other services :
Data is stored in the database and the cloud.
Data is accessible via web services.
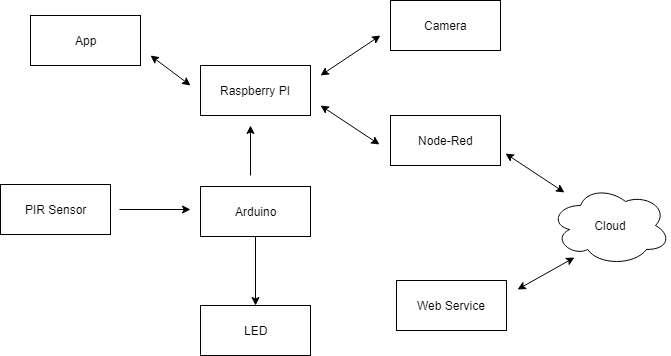
The big picture of the services offered by the Home watch system is shown above. The PIR sensor detects motion and the Arduino is triggered. LED blinks as the indication of the detection of motion. The python program running on Laptop/Desktop send an email to the homeowner.
This can be upgraded with additional devices such as using Raspberry PI as a computing device and Node-Red to communicate the message between cloud and the sensor. Camera module can be used to capture an image when the motion is detected and the image can be sent via email. A web service can be built to provide data for analysis and an app for homeowners to control the notifications.
Functional view specification: The functional groups involved in the Home Watch project are as shown in below figure:
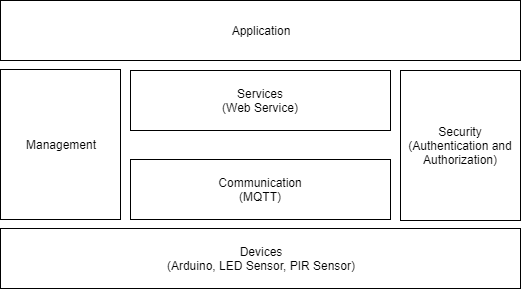
Devices: The computing device is Arduino and the sensor is PIR motion sensor. LED is used to indicate detection of motion. Furthermore, camera module, buzzer, Raspberry PI can be used to enhance it further.
Communication: For the scope of this project, it is a simple wifi-based communication. MQTT a light-weight messaging protocol to publish data to the applications can be used when an application is built.
Services: This project implements a web service to publish data.
Application: The application functional group provides an interface to the users to control and monitor various aspects of the IOT system. Although it is out of scope for this project, an application can be built to control the data and notifications.
Security: Security is a primary concern when it comes to internet-enabled devices and application. The project uses a home network to transmit data. When the project is made larger with the implementation of applications, authentication and authorization can be implemented.
Operational View Specification: Operation view address how an actual system can be realized by using devices and technologies among many options and making them communicate and operate in an efficient manner.
Devices options: Arduino, PIR Sensor, LED. Buzzer, Camera, Raspberry PI are needed for further enhancement.
Communication options: network layer-IPV4, MQTT
Services options: Web Service.
Application options: It is out of scope for the project but as discussed earlier, Node-red web application can be realized.
Security options: Two-phase authentication and authorization.