UGCNET Computer Science August 2016 Paper III Retest
Ans .
(B) Asynchronous counter
- Explanation :
Ans .
(C) 8
- Explanation :
The Intel 8080, 8085, and Zilog Z80 are considered 8 bits, because that was the size of their accumulators and most of their registers, although it’s program counter was 16 bits, and specific pairs of registers could be combined to form 16 bit values or addresses. The Intel 8086 and 8088 are considered a 16 bits, but the 8086 accesses memory 16 bits at a time, while the otherwise identical 8088 accesses memory 8 bits at a time. It had 20 bits for addressing memory (so it could support up to 1 MB). The main registers are 16 bits wide, but some of them can be accessed 8 bits at at time (AX can be accessed as AH (high order part) or AL (low order part)). The Intel 80386 is a 32 bit cpu. The 80386 normally accesses memory 32 bits at a time with a 32 bit addresses. Motorola 68000 16/32 bit processor has 32 bit regisers, but accesses memory 16 bits at a time with a 24 bit address. The Motorola 68020 accessed memory 32 bits at a time. The Intel Pentium Pro is also a 32 bit cpu, but some versions had 36 bits of addressing, that required using address translation schemes. For a typical PC, the amount of memory that can be read at one time varies with the motherboard and cpu, normally it’s 64 bits (called double channel) or 96 bits (called triple channel).
Ans .
(C) Interrupt mask register
- Explanation :
Interrupt Mask Register operates on IRR(Interrupt Request Register) at the direction of the Priority Resolver.
Ans .
(B) DAD H
- Explanation :
HL= HL+ HL means DAD H
Ans .
(B) Register indirect
- Explanation :
The different types of instructions are as follows:
– Immediate Mode: As the name suggests the instruction in itself contains the operand.
– Register Mode: In this mode the operands of an instruction are placed in the registers which themselves are placed inside the CPU.
– Direct address mode: The address part of an instruction in this mode is the effective address.
– Indexed addressing mode: In this mode in order to obtain the effective address the contents of the index register is added to the instructions address part.
– Relative address mode: In this mode in order to find out the effective address the contents of the program counter are added to the address part of the instruction.
-Register Indirect Addressing: Register indirect addressing is similar to indirect addressing, except that the address field refers to a register instead of a memory location. It requires only one memory reference and no special calculation.
Ans .
(D) X Y
- Explanation :
Ans .
(B) I and IV only
- Explanation :
only B option correct as advantages of OODBM
Ans .
(B) Completeness condition
- Explanation :
Completeness condition is the answer because above question is definition of it.
Ans .
(D) 3, 4, 1 respectively
- Explanation :
Ans .
(C) Both I and II
- Explanation :

Ans .
(B) 1 and 2 respectively
- Explanation :
EXCEPT returns distinct rows from the left input query that aren’t output by the right input query. The EXCEPT ALL operator does not remove duplicates. For purposes of row elimination and duplicate removal, the EXCEPT operator does not distinguish between NULLs
Ans .
(D) C A D B
- Explanation :
Specialization: It uses Top to bottom approach means higher to lower
Generalizion: it uses bottom to up approach means lower to high.
Aggregation: it is treated as higher-level entity sets and can participate in relationships.
Mapping cardinalities: number of entities to which another entity can be associated via a relationship set
Ans .
(D) 161
- Explanation :
Ans .
(A) 2N
- Explanation :
A frame buffer is a large, contiguous piece of computer memory. At a minimum there is one memory bit for each pixel in the rater; this amount of memory is called a bit plane. The picture is built up in the frame buffer one bit at a time. N-bit colour Frame buffer: Color or gray scales are incorporated into a frame buffer rater graphics device by using additional bit planes. The intensity of each pixel on the CRT is controlled by a corresponding pixel location in each of the N bit planes. The binary value from each of the N bit planes is loaded into corresponding positions in a register. The resulting binary number is interpreted as an intensity level between 0 (dark) and 2n -1 (full intensity).
This is converted into an analog voltage between 0 and the maximum voltage of the electron gun by the DAC. A total of 2Nintensity levels are possible. Figure given below illustrates a system with 3 bit planes for a total of 8 (23) intensity levels. Each bit plane requires the full complement of memory for a given raster resolution; e.g., a 3-bit plane frame buffer for a 1024 X1024 raster requires 3,145,728 (3 X 1024 X1024) memory bits.
Ans .
(B) xi+1 = xi yi+1 = yi + 1 di+1 = di + 2 dx
- Explanation :
According to Breshenham’s line generation algorithm , the formula of above question is
xi+1 = xi
yi+1 = yi + 1
di+1 = di + 2 dx
Ans .
(B) (–1, 4)
- Explanation :

Ans .
(C) View confusion
- Explanation :
vanishing point: a vanishing point only represents a direction an object points away from us. everything going in the same direction will converge to the same direction point View confusion: projects behind the center of projection are projected upside down and backward onto the view plane. Perspective foreshortening: An object is from the center of projection, the smaller it appears. the point of the plane that is parrallel to the view plane and also passes through the center of projection are projected ti infinity by the perspective projection:
Ans .
(B) (1/6, 5/6)
- Explanation :
Ans .
(B) i iv ii iii
- Explanation :
Lambda calculi (λ-calculi) are formal systems describing functions and function application. One of them, the un typed version, is often referred to as the λ-calculus. This exposition will adopt this convention. At its core, the λ-calculus is a formal language with certain reduction rules intended to capture the notion of function application Church, 1932
In 1960 John McCarthy, a computer scientist at the Massachusetts Institute of Technology (MIT), combined elements of IPL with the lambda calculus (a formal mathematical-logical system) to produce the programming languageLISP Lazy evaluation is the technique of not evaluating an expression unless and until the result of the expression is required. The &&, || and ?: operators are the conventional way to do lazy evaluation:
void test(int* p)
{
if (p && p[0])
...
}
The second expression p[0] is not evaluated unless p is not null. If the second expression was not lazily evaluated, it would generate a runtime fault if p was null. Type Classes: They allow us to declare which types are instances of which class, and to provide definitions of the overloaded operations associated with a class. For example, let’s define a type class containing an equality operator: class Eq a where
(==) :: a -> a -> Bool
Here Eq is the name of the class being defined, and == is the single operation in the class. This declaration may be read “a type a is an instance of the class Eq if there is an (overloaded) operation ==, of the appropriate type, defined on it.” (Note that == is only defined on pairs of objects of the same type.)
Ans .
(A) Multiple variables having the same location
- Explanation :
It is a process by which smooth curves and other lines become jagged because the resolution of the graphics device or file is not high enough to represent a smooth curve. Smoothing and antialiasing techniques can reduce the effect of aliasing. Aliasing in the context of programming languages refers to Multiple variables having the same location
Ans .
(B) 31, 3
- Explanation :
Inside funb(), x will actually refer to y of main(); and y and z will refer to x of main(). The Statement y = y + 4; will result in 14 and statement z = x + y + z will make z = 3 + 14 + 14 = 31 (because y and z point to same variable x of main). Since z refers to x of main(), main will print 31.
Ans .
(D) S → S1 | S2 S1 → aa S1 | A1 S2 → aaS2 | aA2 A1 → bbA1 | λ A2 → bbA2 | b
- Explanation :
A) S – -> aSb – -> aS1b –> ab //n=m=1 not even ;
B) S –> aaS –> aaS1 –> aabSb–>aabaaSb –>aabaab // not in a n b m format
C) S – -> aSb – -> aS1b –> ab //n=m=1 not even
D) always make strings in a n b m format ; such that n and m are even
Ans .
(D) {λ, a, b, ab, ba} {w ϵ {a, b}* | |w| ≥ 3}
- Explanation :
Σ = {a, b} and language L = {aa, bb}. (given)
complement of L is Σ* – L
so, option D is the answer
Ans .
(D) (a), (b) and (c)
- Explanation :
Ans .
(A) 2 sec
- Explanation :
Ans .
(A) a and b are true; c and d are false.
- Explanation :
Ethernet is the most widely installed local area network (LAN) technology. Ethernet is a link layer protocol in the TCP/IP stack, describing how networked devices can format data for transmission to other network devices on the same network segment, and how to put that data out on the network connection. It works on optic fiber. It is a point to point protocol over Ethernet is a network protocol for encapsulating PPP frames inside Ethernet frames.
Ans .
(A) 11010110111110
- Explanation :

Ans .
(C) 0.368
- Explanation :
It is proven that:
the throughput for slotted is S = G * e ^-G
max. throughput is 0.368 when G = 1
ref: forouzan ( book name : data communication and networking)
Ans .
(A) 256, 8 bits
- Explanation :
bit rate of 8000 bps and a baud rate of 1000
Each signal carries=bitrate/baudrate=8
No. of signal elements= 2^8=256
Answer= 256,8
Ans .
(B) HAQC
- Explanation :

Ans .
(C) 9375
- Explanation :
Ans .
(B) 41
- Explanation :
Ans .
(C) 4n – 4
- Explanation :
Ans .
(D) 20, 18, 17, 13, 12, 10, 15
- Explanation :
Ans .
(B) O (d (n + k))
- Explanation :
Ans .
(C) iii i iv ii
- Explanation :
Ans .
(D) no
- Explanation :
Ans .
(B) the start of method declaration.
- Explanation :
Ans .
(A) Composition is a strong type of association between two classes with full ownership.
- Explanation :
Ans .
(B) Abstract class can directly be initiated with ‘new’ operator.
- Explanation :
Ans .
(B)
- Explanation :
Ans .
(D) Asynchronous
- Explanation :
Ans .
(D) 99.97%
- Explanation :
Ans .
(A) e b a c d
- Explanation :
Ans .
(A) d a b c e
- Explanation :
Ans .
(B) ISO 9001 : 2000
- Explanation :
Ans .
(B) Correctness, reliability, robustness, efficiency, usability.
- Explanation :
Ans .
(D) II and III
- Explanation :
Ans .
(C) Both (I) and (II) are correct.
- Explanation :
Ans .
(D) O(mn2)
- Explanation :
Ans .
(B) 34 microseconds
- Explanation :
Ans .
(B) 8, 10, 7
- Explanation :
Ans .
(A) 1
- Explanation :
Ans .
(B) 4
- Explanation :
Ans .
(3) Identical with average revenue
- Explanation :
Ans .
(B) 00*
- Explanation :
Ans .
(D) 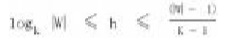
- Explanation :
Ans .
(3) Identical with average revenue
- Explanation :
Ans .
(D) DPCM
- Explanation :
Ans .
(A) Dark
- Explanation :
Ans .
(B) 8
- Explanation :
Ans .
(D) (a), (b) and (c)
- Explanation :
Ans .
(D) (a), (b) and (c)
- Explanation :
Ans .
(A) Fuzzification → Rule evaluation → Defuzzification
- Explanation :
Ans .
(D) (d) and (e)
- Explanation :
Ans .
(C)
- Explanation :
Ans .
(A) ls – l | grep “June” | sort + 10n
- Explanation :
Ans .
(D) An MDI application displays output in the client area of the frame window.
- Explanation :
Ans .
(C) I, II, III
- Explanation :
Nice command runs a command with a modified scheduling priority.It is used to set or change the priority of a process. A process’s nice value can be set at the time of creation.It also takes a command line as an argument. syntax:
nice [OPTION] [COMMAND [ARG]...]
Ans .
(D) I, II, and III are equivalent sentences.
- Explanation :
Ans .
(B) d c a b
- Explanation :
A semantic network, or frame network, is a network that represents semantic relations between concepts. A directed graph is used to represent a semantic network. A frame is an artificial intelligence data structure used to divide knowledge into substructures by representing “stereotyped situations.” Frames are the primary data structure used in artificial intelligence frame languages. Frames are also an extensive part of knowledge representation and reasoning schemes. Primitive knowledge is knowledge that is defined explicitly by facts. Derived knowledge is knowledge that can be inferred from other knowledge. Derived knowledge is usually specified in terms of rules.
Ans .
(A) Is a graph-based method of knowledge representation where nodes represent concepts and arcs represent relations between concepts.
- Explanation :
A semantic network, or frame network, is a network that represents semantic relations between concepts. A directed graph is used to represent a semantic network.
Ans .
(B) Group Decision Support System
- Explanation :
Brainstorming is a group creativity technique by which efforts are made to find a conclusion for a specific problem by gathering a list of ideas spontaneously contributed by its members. Withhold criticism: In brainstorming, criticism of ideas generated should be put ‘on hold’. Instead, participants should focus on extending or adding to ideas, reserving criticism for a later ‘critical stage’ of the process. By suspending judgment, participants will feel free to generate unusual ideas.
Ans .
(B) I1I1 is correct but I2I2 is not a correct inference.
- Explanation :

Ans .
(A) Predicate calculus
- Explanation :