UGCNET Computer Science August 2016 Paper II Retest
Ans .
(D) p
- Explanation :
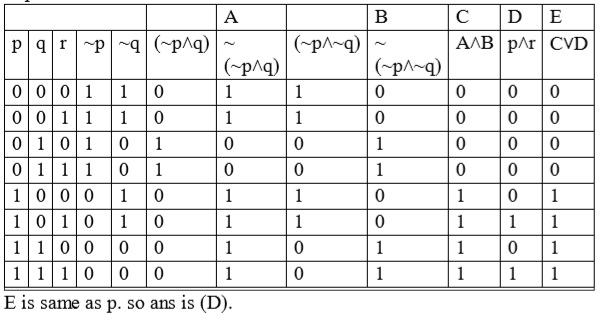
Ans .
(B) ↔~˄pq˅ ~p~q, pq˄~p~q~˅↔
- Explanation :
(~(p˄q))↔(~p˅~q)
Ans .
(D) |A – B| ≤ |AB| ≤ |AB| ≤ |A| + |B|
- Explanation :
Ans .
(B) 1/32
- Explanation :
select 10 bits and with every bit we have two choice either 0 or 1 so the total no of 10 length bit strings are 2^10
Now in palindrome if we chose first 5 bits then our job is done as next 5 are fixed ( first 5 in reverse order).
So, for five bits can be chosen in 25 (for every bit either 0 or 1).
Probability = 2^5/2^10= 1/ 32
Ans .
C) Both G1 and G2 do not contain Euler circuit.
- Explanation :
Ans .
(C) (214.5)10 and (D6.8)16
- Explanation :

Ans .
(C) 2’s complement
- Explanation :
Ans .
(B) AB + AC + AD + BCD
- Explanation :
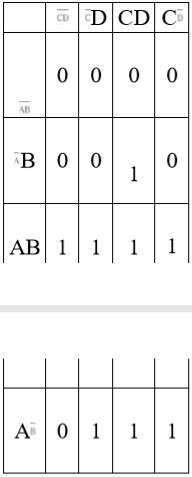
Ans .
(A) EXCLUSIVE-OR
- Explanation :
(X+(X+Y)’)’ + (Y+(X+Y)’)’
Apply DE MORGAN theorem
X'(X+Y)+Y'(X+Y)
XX’+X’Y+Y’X+Y’Y
0+X’Y+Y’X+0
X XOR Y
Ans .
(D) iii i iv ii
- Explanation :
Half adder-> Its is used to add 2 bits.
Full adder-> It is used to add 3 bits.
controlled inverter-> a circuit that transmits a binary word or its 1’s complement
Binary adder -> It is used to add 2 binary numbers
Ans .
(D) 2
- Explanation :
⇒⇒ (x*3)&&3 || j | k
⇒⇒ 0&&3 || (j | k)
⇒⇒ 0&&3 || 1
⇒⇒ (0&&3) || 1
⇒⇒ 0||1
⇒⇒ 1
Ans .
(B) Array of functions returning pointers to integers.
- Explanation :
f is an array of integer pointers and return type of a function
int * f[] () as we can see that return type of function is an array of pointers i.e. f
Ans .
(C) Friend functions are members of a class.
- Explanation :
friend function is not a member of class it works as a bridge between Two classes.
Ans .
(D) Inheritance, Virtual functions and references
- Explanation :
Polymorphism requires inheritance, Virtual functions and references
Ans .
(C) 2
- Explanation :

Ans .
(B) DML
- Explanation :
Ans .
(A) reducing the number of joins required to satisfy a query.
- Explanation :
Ans .
(D) (a), (b) and (c) are true.
- Explanation :
Ans .
(A) I only
- Explanation :
We know that cardinalty constraints on more-than-binary relationship with more than one arrow (1 sides) creates ambiguity in ER diagram. [For more info on this, please refer to the DBMS book by Korth]
The given ER diagram can mean any one of the following two cases:
Case 1: PQ → ST
Case 2: PQS → T and PQT → S
Now, going through the three instances, we can identify the FDs and non-FDs satisfied for the instances as follows:
Instance 1:
PQ↛ T (so, case 1 isnot valid)
PQS ↛ T (so, case 2 is also not vaid)
So, the ER-diagram can NOT be a representation of Instance 1.
Instance 2:
PQ↛ S and PQ↛ T (so, case 1 is not valid)
However, PQS → T and PQT → S (so, case 2 is valid)
So, the ER-diagram can be a representation of Instance 2.
Instance 3:
PQ → S and PQ → T as well (so, case 1 is valid)
Validy of case 1 ensures validity of the FDs in case 2 as well.
So, the ER-diagram can also be a representation of Instance 3.
Therefore, correct answer is (A) I only.
Ans .
(B) SELECT A, COUNT(*) FROM R;
- Explanation :
Aggregate functions,grouping attribute must be used with group by clause.
Ans .
(D) Deletion of the last node of the linked list.
- Explanation :
A)Insertion at the front of the linked list.
new_node->next=head;
head=new_node;
Θ(1)
B) Insertion at the end of the linked list.
Tail->next=new_node;
new_node->next=NULL;
Θ(1)
C) Deletion of the front node of the linked list.
Next_node=Head;
Head=Next_node->next;
free(Next_node);
Θ(1)
D)Deletion of the last node of linked list
Here, we have tail pointer but it will be of no use because there is no previous pointer (as it is single linked list).we need to have second last pointer so that we make it the last pointer and can free the last pointer i.e deleting the last node.So we need to traverse the whole linked list making it Θ(n).
struct node *p,*prev;
p=head;
while(p)
{
prev=p;
p=p->next;
}
prev->next=NULL;
free(p);
so ANSWER is (d)
Ans .
(D) 616
- Explanation :
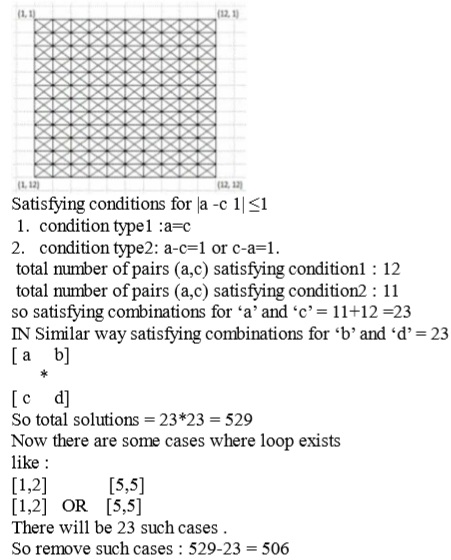

Ans .
(C) O(n)
- Explanation :
Printing the elements in an order means the elements should be printed in sorted order and we know inorder traversal of BST takes gives the sorted order and takes O(n) time.The recurrence involved is :
T(n) = 2T(n/2) + c for balanced BST which on solving gives O(n).
Ans .
(C) Both S1 and S2 are correct.
- Explanation :
Both of the statements are true.
A queue can be implemented using two stacks:
Consider two stacks s1 & s2 ( we will be using STL stacks for implementation ).
Enqueue Operation :: Simply push the element onto s1.
Dequeue Operation :: Transfer all elements from s1 onto s2. Popthe top element from s2. Transfer remaining elements from s2 back to s1.
A stack can be implemented using two queues: Let S1 and S2 be the two Stacks to be used in the implementation of queues.
struct Stack
{ struct Queue *Q1;
struct Queue *Q2;
}
We make sure that one queue is empty always.
Push operation : Whichever queue is not empty, insert the element in it.
Check whether queue Q1 is empty or not. If Q1 is empty then Enqueue the element in it.
Otherwise EnQueue the element into Q1.
Push (struct Stack *S, int data) { if(isEmptyQueue(S->Q1) EnQueue(S->Q2, data);
else EnQueue(S->Q1, data); }
Time Complexity: O(1)
Pop Operation: Transfer n-1 elements to other queue and delete last from queue for performing pop operation.
If queue Q1 is not empty then transfer n-1 elements from Q1 to Q2 and then, DeQueue the last element of Q1 and return it.
If queue Q2 is not empty then transfer n-1 elements from Q2 to Q1 and then, DeQueue the last element of Q2 and return it.
Ans .
(C) 2205
- Explanation :
=> * + 3 + 3 ^ 3 ( 3+ 3) 3
=> * + 3 + 3 ^ 3 6 3
=> * + 3 + 3 (3^6) 3
=> * + 3 + 3 729 3
=> * + 3 ( 3 + 729 ) 3
=> * + 3 732 3
=> * ( 3 + 732) 3
=> * 735 3
=> (735 ) * 3
=> 2205 ( ans- C)
Ans .
(A) Electromagnetic waves with frequencies from 300 GHz to 400 THz.
- Explanation :
electromagnetic radiationwith wavelengths ranging from one meter to one millimeter; with frequencies between 300 MHz (100 cm) and 300 GHz (0.1 cm)
Ans .
(A) twisted pair, 100 metres
- Explanation :
100 Base-TX uses 100 Base-TX uses cable and maximum segment size is 100 metres
Ans .
(B) 2 Mbps
- Explanation :
12000*10000/60= 2 Mbps
Ans .
(A) iv i ii iii
- Explanation :
a) Application layer is the topmost layer in TCP/IP protocol stack.Hence is related to software related things.
b) Presentation layer presents the data in proper format for transmission so it is concerned with semantics of the data.
c) Session layer maintains multiple connections and synchronization since we know session is a combination of multiple connections and hence it is associated with dialog control management
d) transport layer deals with flow control and congestion control mainly.
Ans .
(B) IMAP
- Explanation :
Ans .
(C) 10
- Explanation :
Ans .
(D) 2FH
- Explanation :
MVI A, 35H // content of accumulator = 35H = 0011 0101
MOV B, A // content of register B = 35H
STC // set carry flag = 1.
CMC // complement carry flag = not( 1) = 0.
RAR // Each binary bit of the accumulator is rotated right by one position through the Carry flag. And modify carry = D0.
and D7 = previous carry. // Now content of accumulator = 0001 1010 , carry = 1.
XRA B // The content of accumulator are exclusive OR with register B.
(0011 0101 )XOR ( 0001 1010 )
= 0010 1111
= 2F H
Ans .
(B) Replace P * 32 by P<<5
- Explanation :
Ans .
(B) I and III
- Explanation :
Linker Tasks: I and III
Assembler task: II
Access control task: IV
Ans .
(B) An unambiguous grammar has same left most and right most derivation.
- Explanation :
Ans .
(C) Yes, D, E, G
- Explanation :
Ans .
(A) 11
- Explanation :
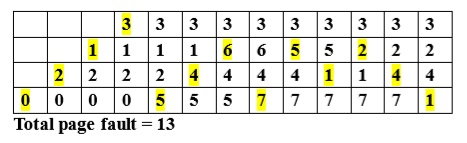
Ans .
(B) 14
- Explanation :
Peak demands of p1,p2,p3 are 2,5 and 7.
allocate 1 less than peak demand i.e,, p1 –> 1 ,p2–>4 ,p3–>6
the number of resources for which deadlock occurs is 1+4+6 = 11
Add one to the number of resources we get 12 ,the value for which deadlock will not occur . ( 13 is nearest possible answer )
Ans .
(B) C, E, D, B, A
- Explanation :
Ans .
(A) 3
- Explanation :
Ans .
(A) n1/n2
- Explanation :
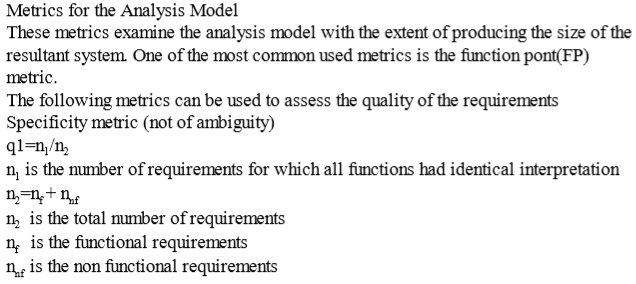
Ans .
(A) the difficulty in accommodating changes after requirement analysis.
- Explanation :
Ans .
(B) prototype model
- Explanation :
Prototype model: The basic idea here is that instead of freezing the requirements before a design or coding can proceed, a throwaway prototype is built to understand the requirements. This prototype is developed based on the currently known requirements. By using this prototype, the client can get an “actual feel” of the system, since the interactions with prototype can enable the client to better understand the requirements of the desired system. Prototyping is an attractive idea for complicated and large systems for which there is no manual process or existing system to help determining the requirements. Waterfall model is the simplest model of software development paradigm. It says the all the phases of SDLC will function one after another in linear manner. Iterative model leads the software development process in iterations. It projects the process of development in cyclic manner repeating every step after every cycle of SDLC process. V -model‘ is also used by many of the companies in their product. ‘V -model’ is nothing but ‘Verification’ and ‘Validation’ model. In ‘V -model’ the developer’s life cycle and tester’s life cycle are mapped to each other. In this model testing is done side by side of the development. Likewise ‘Incremental model’, ‘RAD model’, ‘Iterative model’ and ‘Spiral model’ are also used based on the requirement of the customer and need of the product. Big Bang Model This model is the simplest model in its form. It requires little planning, lots of programming and lots of funds. This model is conceptualized around the big bang of universe.
Ans .
(C) 4k + 1
- Explanation :
boundary value analysis 4n+1
Robusness testing 6n+1
worst case testing 5n
Ans .
(C) Reliability
- Explanation :
Reliability is the probability of failure-free operation of a system over a specified time within a specified environment for a specified purpose Robustness is the ability of a computer system to cope with errors during execution and cope with erroneous input. Correctness of an algorithm is asserted when it is said that the algorithm is correct with respect to a specification Accuracy of a measurement system is the degree of closeness of measurements of a quantity to that quantity’s true value
Ans .
(A) Denial of service attack
- Explanation :
Simple And Complex Attack-:Heard first time of this type of attack,classification is actually active and passive attack.
Denial of service attack-:Not Giving/allowing Legitimate user to access /use his resources which he is supposed to use.
Masquarade attack-:Using fake identity to gain unauthorized access. Given Question is a type of Man in the middle attack.
Ans .
(C) Data warehouse
- Explanation :
DATA WAREHOUSE is subject oriented, integrated, time variant, non-volatile collection of data in support of management decisions.a large store of data accumulated from a wide range of sources within a company and used to guide management decisions.
Ans .
(C) Decision Tree
- Explanation :
A decision tree is a graph that uses a branching method to illustrate every possible outcome of a decision. Decision trees can be drawn by hand or created with a graphics program or specialized software. Informally, decision trees are useful for focusing discussion when a group must make a decision and classification rules are extracted from Decision tree
Ans .
(A) Association
- Explanation :
Cross-selling is the action or practice of selling an additional product or service to an existing customer. In practice, businesses define cross-selling in many different ways. Elements that might influence the definition might include the size of the business, the industry sector it operates within and the financial motivations of those required to define the term.
The objectives of cross-selling can be either to increase the income derived from the client or to protect the relationship with the client or clients. The approach to the process of cross-selling can be varied.
Ans .
(B) COBWEB
- Explanation :
